Ever-increasing demands for remote work and the shift to cloud-as-default have propelled many companies to re-energize their data protection and threat neutralization strategies. Successful strategies emphasize robust identity and access management (IAM) and detailed visibility into all traffic and transactions. Okta, one of our strategic partners for IAM, recently published its eighth annual Business at Work report. Okta identifies Netskope as the fastest-growing application by number of unique workers, with an astounding 913% year-over-year gain. Clearly, security is experiencing a renaissance.
Anonymized data assembled from thousands of companies, applications, and IT integrations, plus millions of daily authentications and verifications around the world, inform Okta’s reporting and analysis. Each year Okta highlights the most popular and the fastest-growing applications, along with extra context, such as region and industry. Okta also identifies distinct trends that characterize common patterns from year to year. I’d like to highlight a couple of these trends to explore the benefits of Netskope’s partnership with Okta.
Tear down this (fire)wall
One major theme for 2022 is, unsurprisingly, work from anywhere. Okta observes that products and services installed as “temporary stopgap measures during a time of crisis” morphed into long-term deployments that “fuel better workplace collaboration, clearer communication, and stronger security for teams around the world or across the room—or, increasingly, both.”
Another theme, one that enables the first, is the cloud is inescapable. No matter how you slice it—whether by category or region or industry or unique workers or customer count—SaaS applications dominate. Okta’s data indicates that companies deploy an average of 89 applications; companies with more than 2000 employees deploy an average of 187. But wait: are these numbers on the low side?
The Netskope July 2021 Cloud and Threat Report indicates an average of 805 applications. Why the discrepancy? Unmanaged SaaS. Whether you view it as pernicious shadow IT or propitious business IT, it constitutes 97% of your overall SaaS utilization, likely bypassing your identity provider (IdP). Alarmingly, 48% of unmanaged SaaS receives a poor Netskope Cloud Confidence Index risk rating. Can you articulate, with certainty, that you know exactly where your sensitive data is? Yeah no, I thought so.
With Netskope and Okta, converting unmanaged SaaS to managed SaaS is simple and quick. We can show you a handy demo in under two minutes. Not only does the application become managed by Netskope, but also a specific activity triggers Okta to intervene with a step-up authentication prompt, even if the application lacks IdP integration. Here’s the setup:
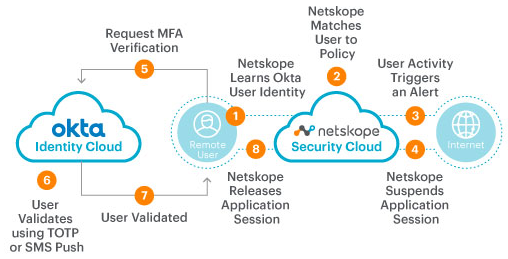
Of course, most typical business functions should transpire in approved applications. But when it’s necessary for a group or department to interact with an unapproved one, Netskope and Okta together provide a way to manage certain actions within it, based on context and content. Moreover, Netskope Advanced Analytics reveals every application that workers access via Okta identities and the credentials they entered.
Configure all the things
What else can we learn from Okta’s report? Your future—perhaps your present—bristles with multiple overlapping redundant clouds of every *aaS flavor. Among SaaS applications, the quadfecta of Google Workspace plus Slack plus Zoom plus Box is poised to overtake Microsoft 365, sometimes even among companies already adopting the eponymous Microsoft suite. For IaaS and PaaS, application developers increasingly pair AWS with GCP; even individually, they’re outpacing Azure’s still-respectable growth. For any multi-cloud combination you can imagine, Netskope and Okta provide consistent security and the tools to demonstrate that you’ve secured it correctly.
Every successful cloud security strategy rests on the foundation of a reliable and robust identity and access management strategy. Too many secret clouds present an attractive target for attackers. Whenever possible, hook your cloud subscriptions to your identity provider: always know who logs in when and from where. Evaluate additional accompanying signals to measure login confidence and permit only the safest and necessary actions possible. Adjust access as new signals suggest more or less confidence. Netskope and Okta support system for cross-domain identity management (SCIM): workers placed into a high-risk Okta group immediately receive any policy restrictions defined in a corresponding high-risk Netskope group.
Gartner predicts that “99% of cloud breaches will have a root cause of customer misconfiguration or mistakes.” Sensitive data worms into unexpected places, attackers probe lax network access controls, malware sneaks into cloud applications and storage. Netskope security posture management for IaaS and for SaaS assess the security configurations of your cloud subscriptions and suggest improvements. They track improvement over time, deftly generating exactly the evidence that nosy interlopers—regulators, auditors, your customers—demand for demonstrating good cloud governance. While the cloud can be more secure than your data center, the defaults often aren’t. Extinguish your cloud angst with Netskope and Okta.
Two great cloud services brighten your cloud safety together
The cloud represents many inversions: from one data center to many centers of data; from applications and data and workers on the inside to the outside; from security departments approving everything to departments being bypassed. Security controls built for earlier eras are blind to today’s traffic; security practices designed in earlier eras are ineffective with today’s architectures. A new model is required, one with an inversion of its own: from trust but verify to verify then trust.
A boon to hundreds of companies already, the Netskope Security Cloud together with the Okta Identity Cloud transforms the model into reality, evaluating signals both during and after every login to obtain the full context surrounding every transaction. Rooted in identity and suffused with activity, such context-aware access balances trust against risk to match the type of access to the value of protected assets in real time. You’ll shrink attack surfaces, limit blast radiuses, constrain lateral movement, and respond to threats with greater speed and accuracy.
Check out our other demos and download the Netskope with Okta solution brief. Connect with Netskope and with Okta to stay up-to-date. To learn more about how Netskope and Okta can secure your cloud journey, give us a shout.




 Back
Back 





















 ブログを読む
ブログを読む