As we all learn how to practically apply the emerging technology of Secure Service Edge (SSE), here is a significant SSE use case—perhaps the most significant, at least in our immediate future. Looking ahead to 2022, many businesses will no doubt have return-to-office plans at the front of their minds. But coming back to the office brings its own unexpected risks that security leaders need to be ready for. Similarly, the “Great Resignation” of knowledge workers in search of more permanent work-from-home options is also looming on the horizon. The “Great Switch” is the more likely situation similar to free agency with athletes as already seen in the service sector of the job market in 2021. It’s clear security teams need to reorient their mindset now to make sure their data is secure wherever it lives and from wherever it is being accessed as employees make career changes. Specifically, utilizing the visibility, instance awareness, and data context inherent to a secure access service edge (SASE) architecture, as well as the technologies that comprise SSE and form the security side of SASE.
Insider threats behind the “Great Resignation”
Putting this situation in perspective, most organizations will announce their intention to return to offices 30-60 days in advance to give employees ample time to prepare. What many are expecting is that employees who have become accustomed to remote work will not want to return to an office setting, looking for permanent remote work instead, and willing to change jobs for more flexible arrangements. But as job searches surge, so does the risk for sensitive data exfiltration.
Earlier this year, Netskope Threat Labs found a 300% rise in employee data theft during their last 30 days of employment, with 74% of that data going to personal instances of Google Drive. What’s more, the Netskope Cloud Threat and Threat Report also notes that 83% of managed corporate devices already have personal app instances installed making data exfiltration even easier.
Without proper integrated data context, visibility, and instance awareness, businesses are opening themselves up to a huge risk if their sensitive data is exfiltrated during office reopening efforts. If the average employee is moving as many as 20 company files to a personal app instance per month, and you aren’t able to see the data and where it is going, you have a serious problem on your hands already.
This is where technologies that make up SSE, within a properly designed SASE architecture, can help security leaders level their security strategy and keep sensitive data secure as it moves throughout cloud applications, both managed and unmanaged including personal instances favored for data exfiltration.
SSE considerations in action
SSE, as Gartner defines it, refers to the evolving security stack needed to successfully achieve a SASE convergence, including cloud access security broker (CASB), secure web gateway (SWG), Firewall-as-a-Service, and zero trust network access (ZTNA) capabilities. Two core SSE benefits are the ability to follow data wherever it goes and to understand the context around the data access.
In the Netskope Security Cloud, this can manifest through data protection that utilizes inline AI/ML classifiers for images and documents including resumes, source code, and other specific types of sensitive data. Similarly, Netskope Advanced Analytics can show unknown data movement and risks categorized by app, user, instance, and activity, plus high-risk apps, duplicate app use, and other risks. When integrated with user and entity behavior analytics (UEBA), the context of where these classifiers and risks are detected with instance awareness and can trigger an alert and notify the security team of suspicious activity.
To better contextualize how this all works in action, here’s what we learned in a recent case study. At a financial services company Netskope SSE collects activity on the company’s web, apps, cloud services, and data activity. Netskope SSE identified a departing employee who had copied more than 1,200 sensitive company files to a personal app instance for cloud storage. In this situation, and as pictured below, Netskope UEBA not only saw that the user was downloading 10 times more files than they normally would, but also was able to see that those files were going to personal cloud app instances. As a result, UEBA correlated more than six anomalies and various DLP alerts to immediately lower the user’s User Confidence Index (UCI) score from near 1000 (good) to 347 (poor) and alert the company’s security team.
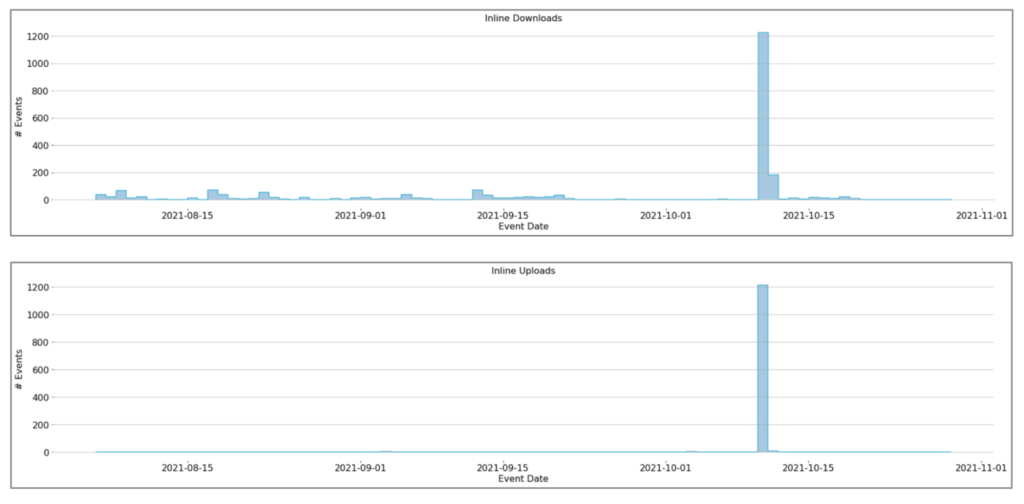
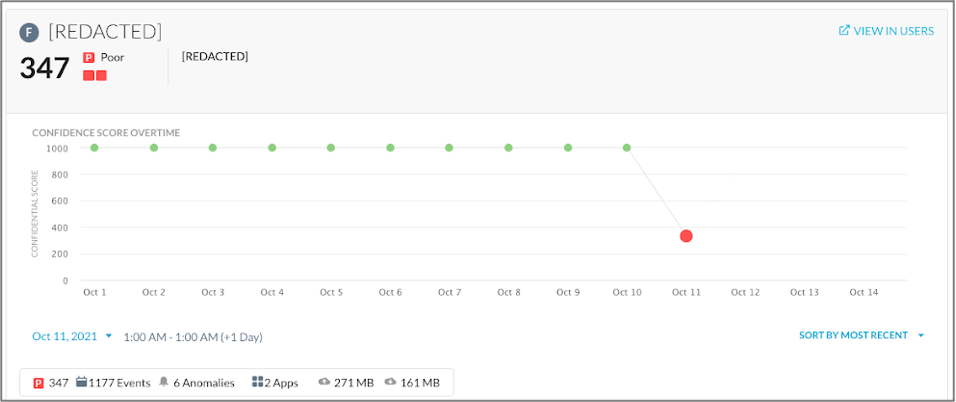
Netskope adaptive policy controls can also act upon UCI for user risk, plus Cloud Confidence IndexTM (CCI) for app risk in real-time with coaching on user behavior, recommending safer alternatives, invoking step-up authentication, or requesting justifications for desired activity. Leveraging context and context in policy controls enables Netskope to detect insiders, compromise, and undesired data movement inline and via API inspection.
With this kind of insider threat situation in mind, security leaders looking to evolve their security strategy to accommodate return-to-work plans with the Great Resignation (or Switch) on the horizon must have visibility into where their data flows with context and instance awareness. For SSE threat and data protection efficacy within SASE, context is a core requirement that legacy defenses hosted in the cloud today just cannot provide. As a result of this security migration with four key transformations, SASE can help better enable your network and security transformation phases, however, SSE will determine your success with app and data transformation phases in direct relation to threat and data protection.




 Back
Back 





















 ブログを読む
ブログを読む