Summary
Netskope Threat Labs is tracking a widespread phishing campaign affecting hundreds of Netskope customers and thousands of users. The campaign aims to steal credit card information to commit financial fraud, and has been ongoing since the second half of 2024. The attacker targets victims searching for documents on search engines, resulting in access to malicious PDF that contains a CAPTCHA image embedded with a phishing link, leading them to provide sensitive information. All malicious PDFs are hosted on the Webflow CDN.
| Category | Description |
|---|---|
| Hosting | Webflow |
| Domain | assets.website-files[.]com |
| Top targeted industries | Technology, Manufacturing, and Banking |
| Top targeted regions | North America, Asia, and Southern Europe |
| Information targeted | Credit card information, email address, first and last name. |
| Attack vector | Search engines |
Search engine serving phishing PDFs
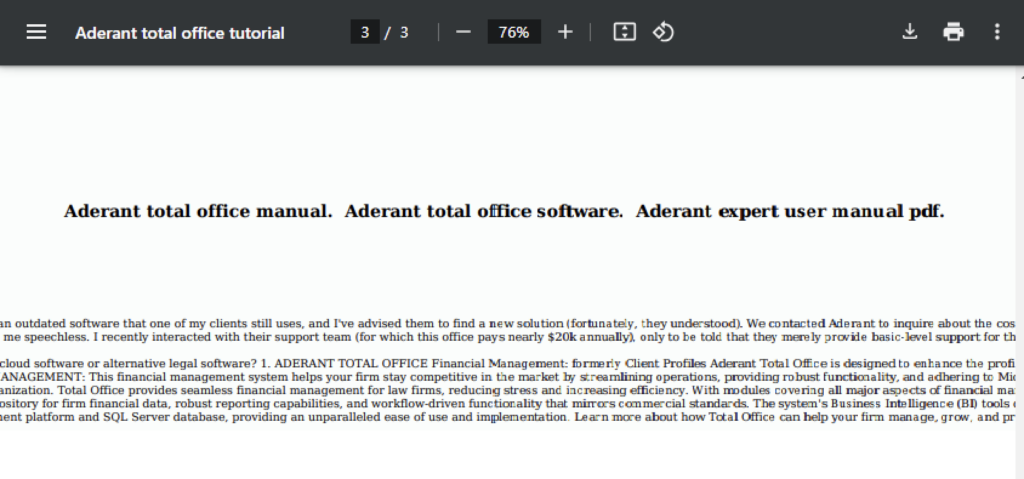
The phishing campaign Netskope Threat Labs has been tracking abuses Webflow CDN to host malicious PDFs. While Webflow offers CDN storage for customer assets, this service is misused to store malicious PDF files. These PDFs appear in search engine results when victims search targeted keywords, such as book titles, documents and charts. The PDF files contain multiple targeted keywords that victims are likely to search for. The malicious PDF files are used to redirect users to phishing websites using fake CAPTCHA images.
Phishing link embedded in CAPTCHA
Netskope Threat Labs recently reported a malware campaign using a deceptive CAPTCHA technique to trick victims into running malicious scripts. This time, attackers use CAPTCHA for phishing by embedding the phishing URL in a CAPTCHA image inside the malicious PDF file, redirecting users to phishing pages when they attempt to solve the challenge.
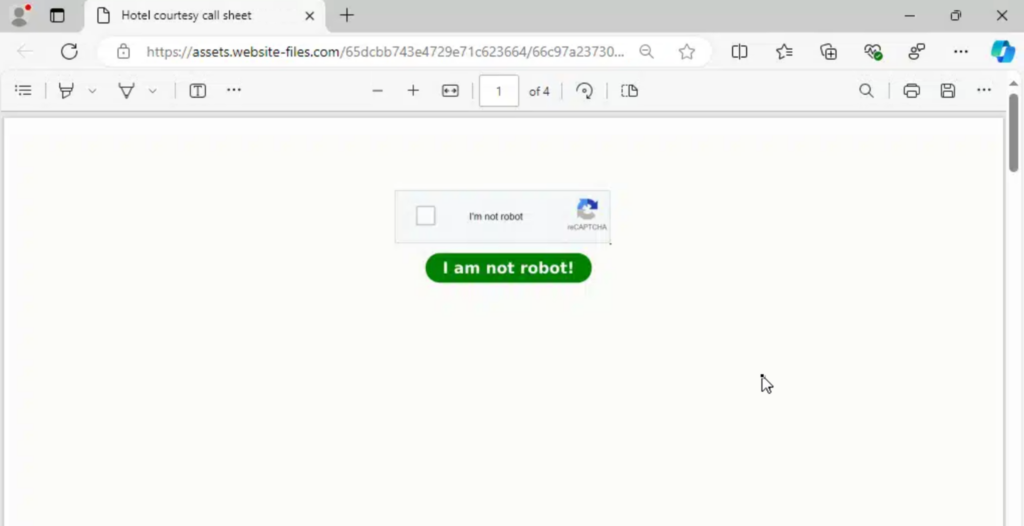
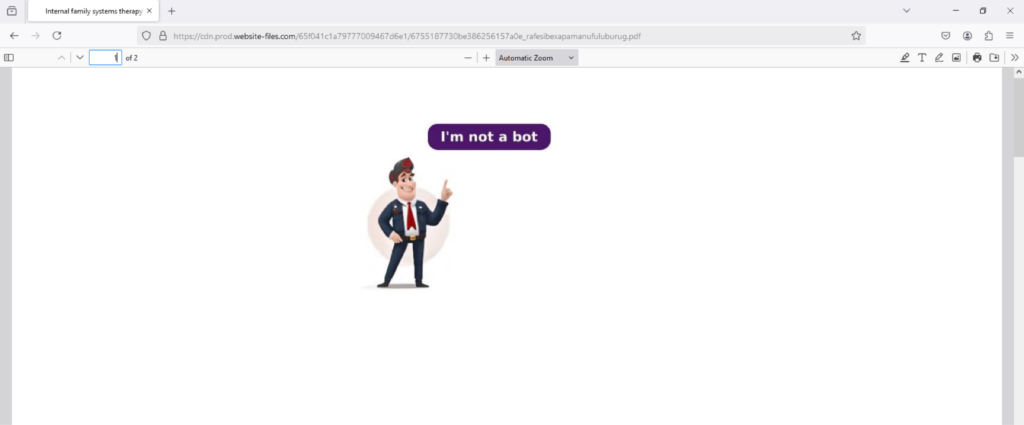
Ironically, when you click the CAPTCHA button, you will be redirected to an actual Cloudflare Turnstile CAPTCHA. This creates the illusion that the original fake CAPTCHA was real, potentially tricking victims into believing they’re interacting with a genuine security check. Like with previously reported phishing campaigns, attackers are known to hide their phishing pages under CAPTCHAs to avoid being detected by static scanners.
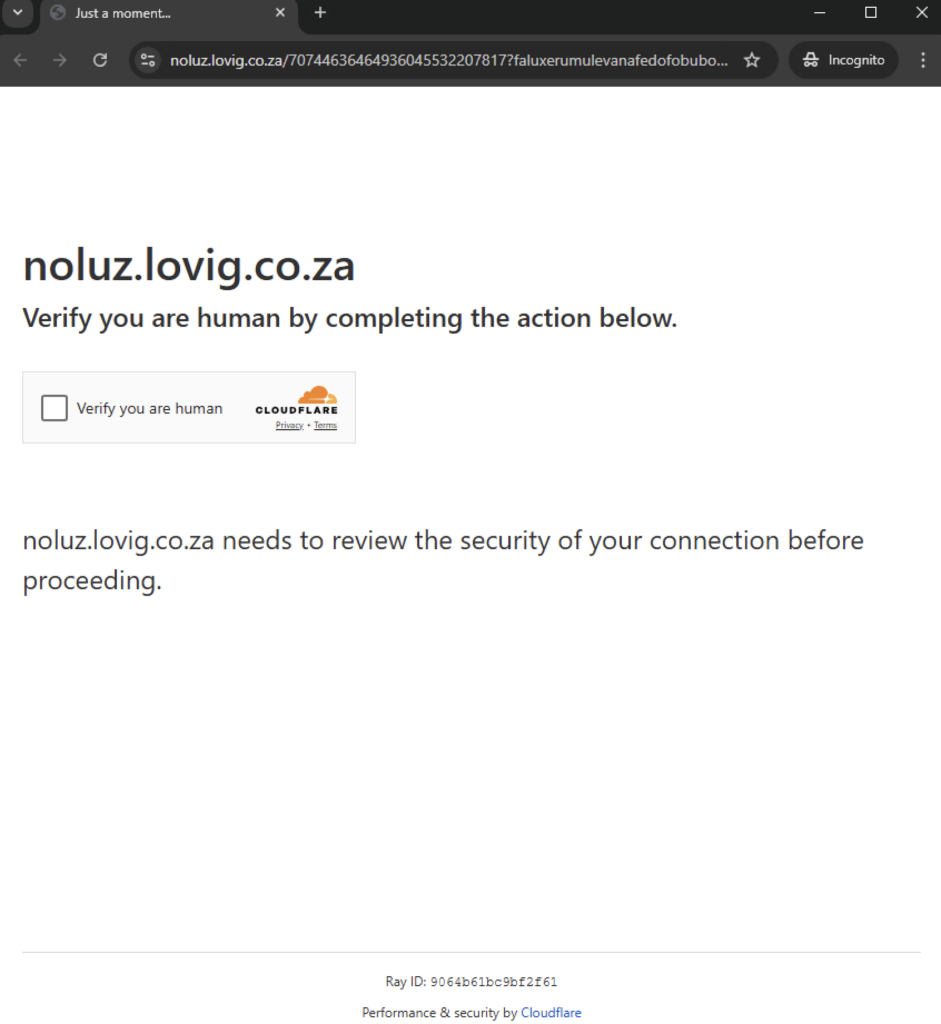
After completing the Cloudflare CAPTCHA, they are redirected to a forum where a file is offered, named after the search engine keyword they used to find the site.
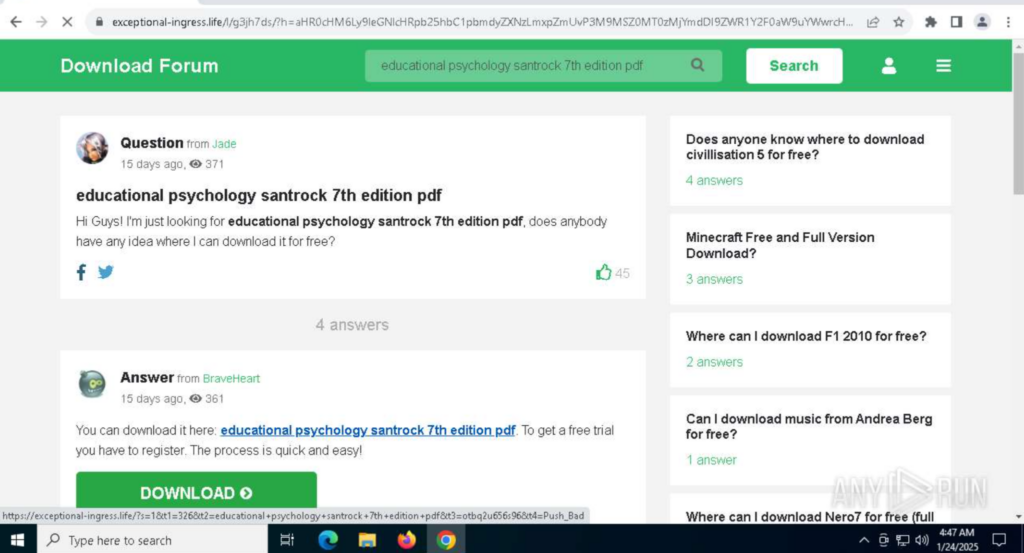
When the victim attempts to download the document, they will be asked to sign up for their page, providing their email address and first and last name.
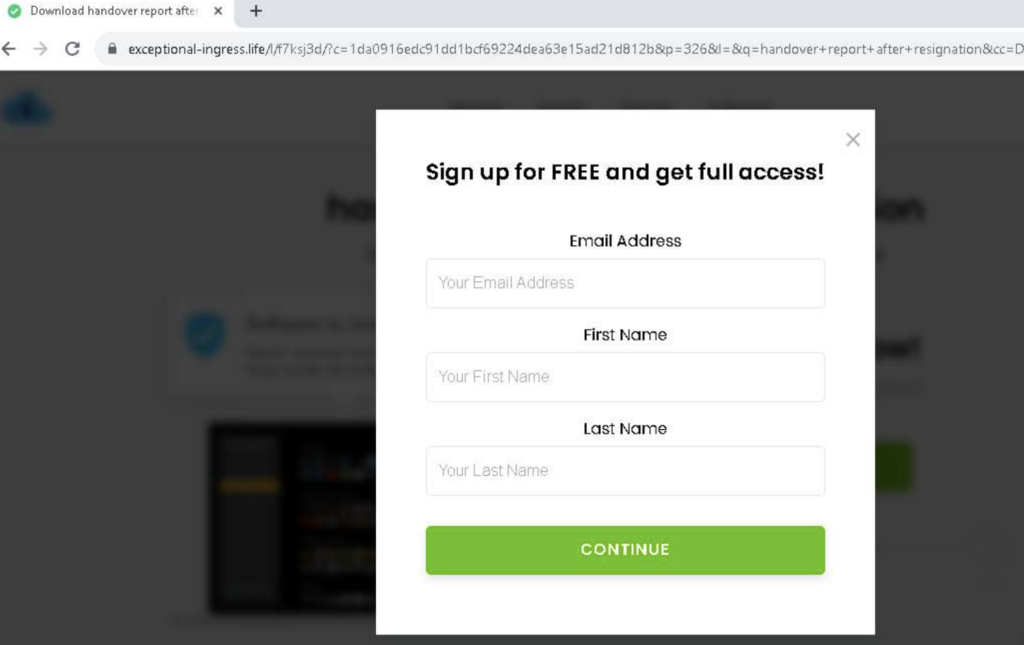
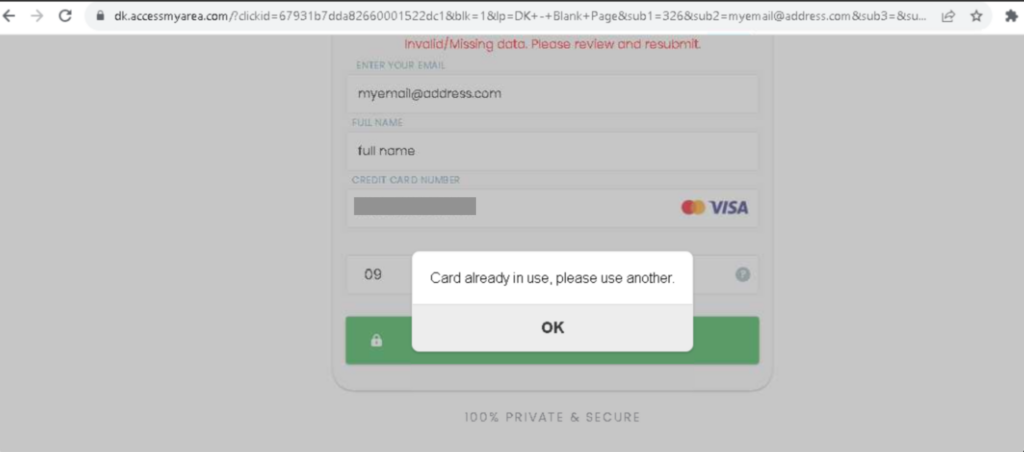
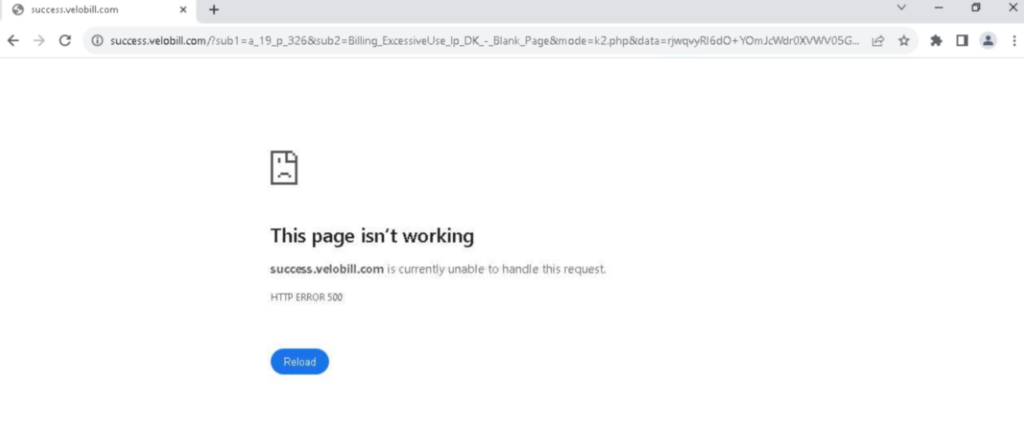
To complete the sign up process, the victim is then asked for their credit card details. Upon entering credit card details, the attacker will send an error message to indicate that it was not accepted. If the victim submits their credit card details two or three more times, they will be redirected to an HTTP 500 error page.
Conclusion
Attackers are targeting victims searching for documents on search engines to siphon away their financial and personal information. They use SEO techniques to lead victims into accessing malicious PDF files hosted on the Webflow CDN, which contain a fake CAPTCHA image. Attackers embed phishing links into the fake CAPTCHA image to redirect victims to the phishing website. They use Cloudflare Turnstile to deceive victims they are solving a legitimate CAPTCHA, while also protecting their phishing pages from static scanners. Netskope Threat Labs will continue to track and respond to these phishing campaigns.
Netskope Detection
- Netskope Threat Protection
- Document-PDF.Trojan.Heuristic
- Document-PDF.Phishing.Generic
- Document-PDF.Spam.Heuristic
- Netskope Advanced Threat Protection provides proactive coverage against this threat
- Gen.Detect.By.NSCloudSandbox.tr
Disclosure
The URLs were reported to Webflow on January 23, 2025.
Data Analysis
The analysis presented in this blog post is based on anonymized usage data collected by the Netskope Security Cloud platform relating to a subset of Netskope customers with prior authorization.
IOCs
All the IOCs related to this campaign can be found in our GitHub repository.




 Back
Back 





















 ブログを読む
ブログを読む