Challenges from the modern workforce
The problem of securing the modern workforce goes beyond occasional spats between IT and security. The real problems we see are user credentials under constant attack, alongside attempts to harvest and exploit enterprise data. Plus the cloud resources that workforces need are tough to secure, especially when deployed outside of IT-led processes. In light of these issues, corporations need a way to securely provide always-on cloud access for users while safeguarding enterprise data anywhere it goes.
There are underlying challenges that no single vendor can solve to help address these obstacles for securely enabling the modern workforce. Regardless of its efficacy, no one tool can solve all of these problems, and as a result we need modern tools to be integrated. For example, identity-based controls require federation, while legacy security solutions are stuck on the binary of either allowing or blocking sessions, applications, or transactions.
Let’s expand on these examples and explore what the dependencies of identity based and security-based controls mean for IT teams.
- Identity-based controls
According to the July 2022 Netskope Cloud and Threat Report, organizations use an average of 2,100 apps, while only approximately 89 applications are managed by IT according to Okta’s Business at Work 2022 Annual Report. The modern workplace typically enables users to procure and access applications without requesting permission from security or IT. IT can only federate applications that they have formally rolled out, leading to this significant disparity. There are third-party systems or applications that can drive users back to IT, but IT still needs to federate to fully control the application.
- Security-based controls
The traditional approach was to block unknown or untrusted applications or websites because security teams lacked the ability to see how users could engage with these resources. It did not matter that identity providers, like Okta, provided an authenticated user to tie to the resource being reached because either the connection was implicitly trusted (a known user going to the “safe” OneDrive site, but really using their non-corporate instance), or explicitly denied (known user going to a relatively unknown cloud site to do perfectly safe business and blocking may just be “safer”). Without context, security-controls are going to over-correct or under-correct.
With context and deep visibility into not only the user and the destination, but also the minutiae around how they are connecting and what they are doing with the data and service, we can safely navigate and enable the modern worker. Here’s how we can do this:
Continuous adaptive zero trust
Netskope and Okta are proud to reaffirm our commitment to an integration strategy that helps IT and security provide nuanced, continuous zero trust controls that keep the workforce secure, performant, and productive. How do we do this?
- Fine-grained access control lets IT provision users and groups within Netskope for policies covering ALL Internet activities
- Policy-driven cloud access backed by strong authentication powers visibility into user access and behavior from login to logout for all applications and web browsing
- Globally consistent, continuously enforced, real-time identity-based policy including automated ongoing identity validation based on risk
- Enterprises can enjoy real-time end-to-end protections from a wide array of internal and external threats thanks to this industry-leading identity and secure access services edge (SASE) partnership
Netskope helps companies get more out of their identity spend by binding the use of all applications to Okta managed identity in Netskope reporting and enforcement. So even if your users decide to start engaging with an application that no one in the IT/identity shop knows about, Netskope ties their non-federated usage to their Okta identity. Now IT can bring those much-needed applications (and there are MANY) back into the Okta Life Cycle Management program.
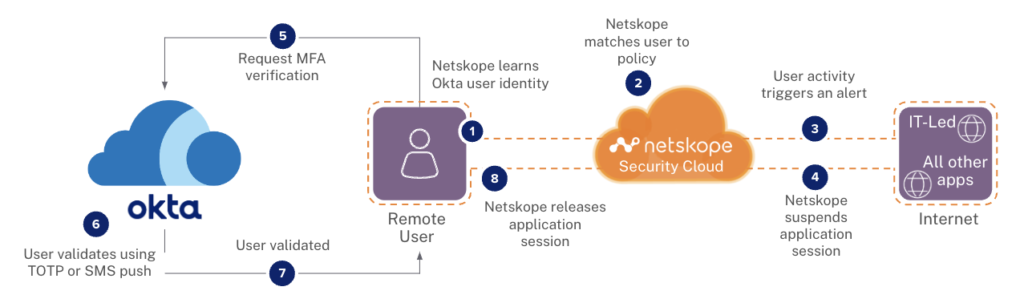
Another example of how this works is in our joint approach to delivering Access, Authentication, and Authorization (AAA) in a hybrid IT environment. Netskope Private Access for Zero Trust Network Access (ZTNA) securely enables users—that Okta Advanced Server Access has authenticated at session establishment and that Netskope continuously revalidates using Okta step up tech—to access the premise or cloud-based solution. Okta then manages the authorization of the user to work with the application. Netskope brings secure access, Okta delivers industry leading authentication and authorization, as depicted in the diagram below.
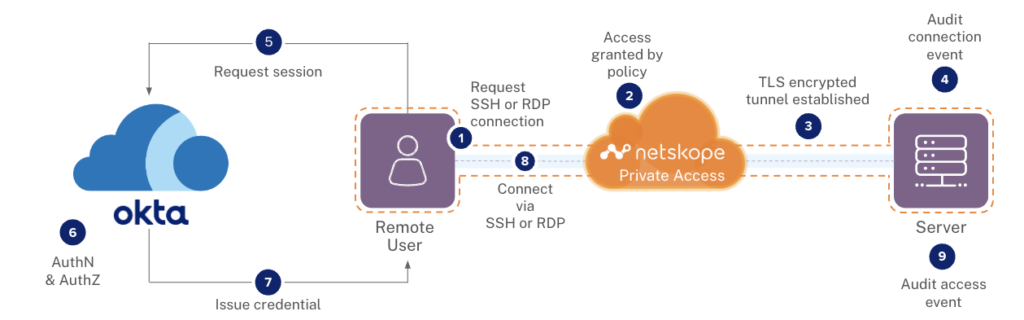
Together, we’re unstoppable and the age of free love between IT and Security is possible. Learn more about how Netskope can help you get more out of your Okta solution and safely enable your modern workplace.
Netskope is sponsoring and exhibiting at Okta’s annual customer and user conference, Oktane 22, on Nov 8-10 in San Francisco. We’re showcasing the Netskope SSE Intelligent platform and our key Okta integrations that help organizations eliminate the security risks associated with Shadow IT, and provide more visibility and control over all applications used by employees, sanctioned and unsanctioned and more. Stop by the Netskope booth #E7 to speak with our team and to see our latest demos.




 Back
Back 















 ブログを読む
ブログを読む