The RSA Conference 2018 Asia Pacific & Japan was held in Marina Bay Sands, Singapore from the 25 – 27 July. Several distinguished professionals from around the world attended the event, which included technical trainings, security conference and a capture the flag (CTF) competition.
Abhinav Singh and Ashwin Vamshi from the Netskope Threat Research Labs were privileged to deliver a talk on “Endpoint vs. Cloud: Forensicating Cyberthreats in Two Parallel Worlds!”.

With a major shift of services towards cloud, the dynamics of threats have changed and they have started adapting to this new playground. From a security and threat detection perspective, it becomes crucial to understand how the cloud platforms differ from the traditional client-server models. One of the main agenda of the talk was to compare the endpoint deployment with current cloud infrastructure while performing various security assessments like penetration testing, forensics, and malware analysis. The concept of shared responsibility model in cloud infrastructure opens up new challenges as well as opportunities to tackle some of the most rudimentary challenges of security. A deeper understanding of the model helps in early adoption of right security solutions and practices at an early stage of migration towards cloud.
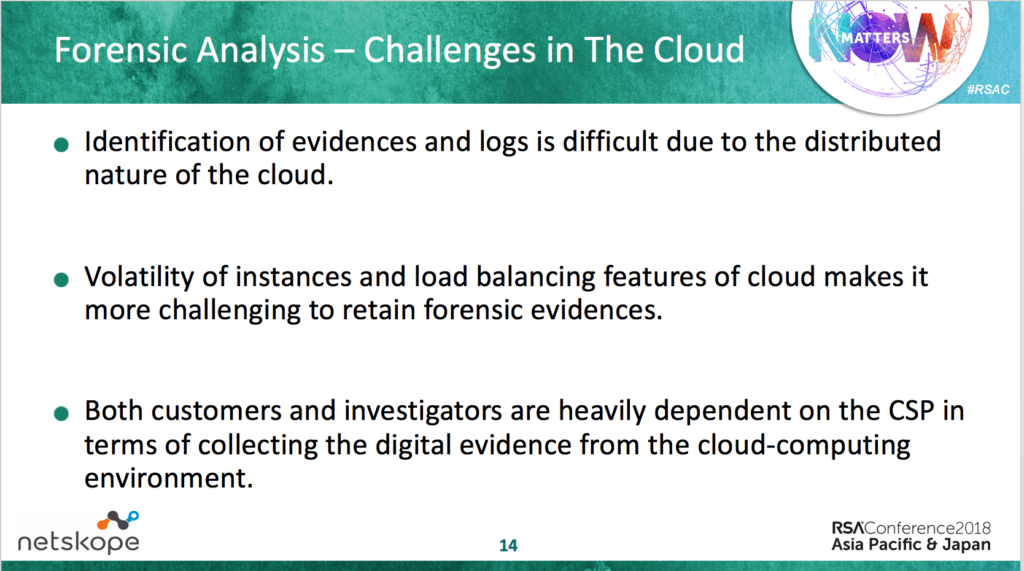
Another important agenda of the talk was to understand some of the advance intrusion capabilities in the cloud like pivoting inside IaaS, privilege escalations and minimizing traces of activities inside a cloud infrastructure. We provided a list of the cloud attacks that have been detailed in our research blogs
- Resurgence of Phishing-as-a-Service (PhaaS) platforms
- Virlock’s resurgence poses bigger threat to file syncing over the cloud
- Decoys, RATs, and the Cloud: The growing trend
- Stepping Stone Attack launches EternalBlue Internally
- Xbooster Parasitic Monero Mining Campaign
- Cryptojackers on the hunt for your IaaS resources
One of the major differences in compromising the cloud infrastructures is to hijack its resources and use them for illegal cybercrime activities like cryptojacking and botnet attacks. The slide image below lists some of the major impacts to cloud infrastructure upon falling victim to such intrusion attempts. 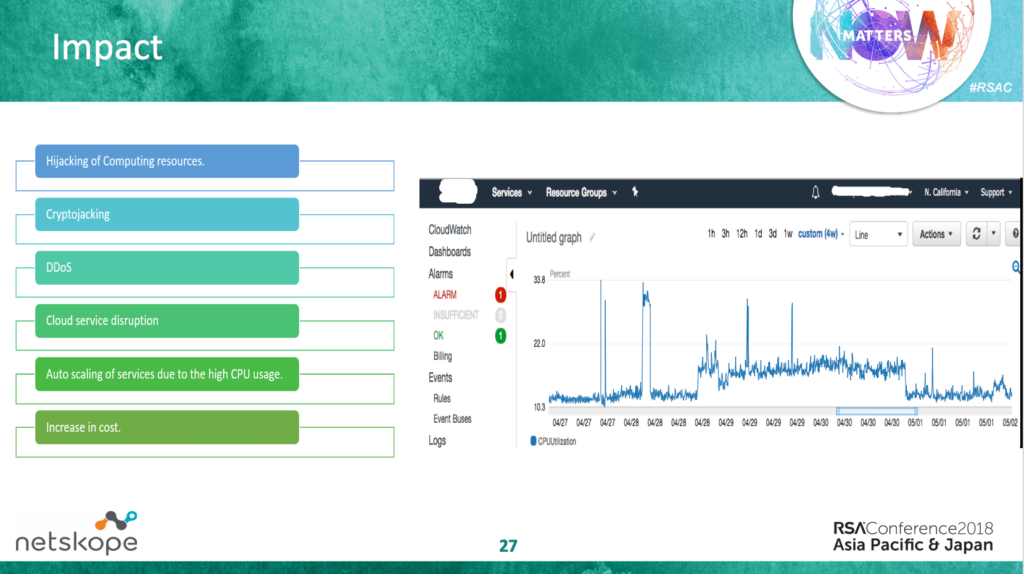
The talk concluded with some key takeaways:
- Comparing the Endpoint security with Cloud security
- Mapping various security aspects like penetration testing, forensics, malware analysis and identity management in the two platforms.
- Understanding intrusion techniques in a cloud infrastructure.
- Understanding key features of cloud platform to build new security solutions.
The last agenda of the talk was to educate the audience in building a cloud security model for the enterprises. We discussed some of our use-cases that helped create the cloud security threat stack at Netskope and how it can be utilized by organizations in securing their SaaS, PaaS or IaaS infrastructures.
Overall, the talk proved its worth in the speaking slots by attracting a near full-house audience and a rich QA session post the talk. Our speakers were delighted with the opportunity to meet and attend talks workshops from speakers all over the world in the cybersecurity arena of RSA Conference 2018 Asia Pacific & Japan.




 Atrás
Atrás 




















 Lea el blog
Lea el blog