Summary
In August 2023, Netskope Threat Labs highlighted an increase in downloads of PDF phishing attachments in Microsoft Live Outlook, caused by a series of phishing campaigns targeting users of the email service. We took a closer look and found that these campaigns are mostly Amazon-themed scams with a few Apple and IRS-themed phishing attempts sprinkled throughout. Just like in our previously reported phishing blog posts, attackers are abusing free services in these campaigns. In this campaign, they abuse conversion trackers and redirectors to evade detection. Additionally these campaigns specifically targeted personal Microsoft Live Outlook accounts in North America, Southern Europe, and Asia. Let’s take a closer look at the details of these campaigns:
Amazon-themed phishing campaign
Netskope Threat Labs recently analyzed the cause of an increase in malware downloads from Microsoft Live Outlook and found that a major contributor was a variety of Amazon-themed phishing PDF attachments. The sender purports to be a member of the Amazon support team notifying recipients that their account has been suspended due to incorrect billing information. In order to supposedly rectify the situation, the users need to update their billing information by clicking the hyperlink. The attacker is abusing different redirectors with URL shorteners to hide the actual malicious URL and evade detection.

Some of the phishing links used in these campaigns lead to a compromised website that mimics PayPal’s page, where they ask users to fill up personal information and credit card details.
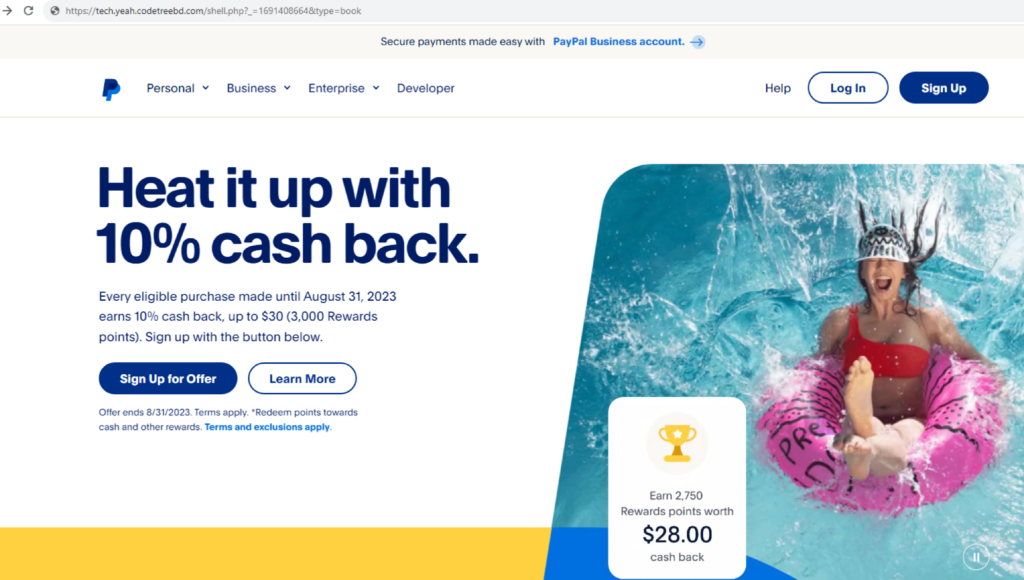
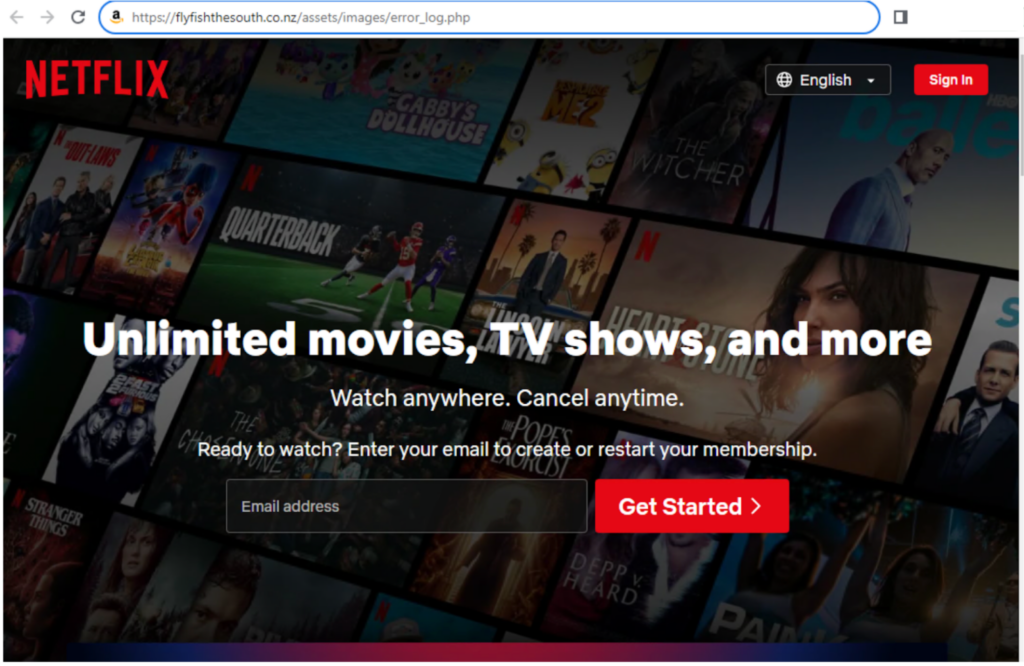
In some of the other scam campaigns we analyzed, even though the PDF attachment is requesting their targets to re-enter their Amazon billing information, some of the links redirect to other sites unrelated to Amazon, like login pages for Ionos and Netflix.
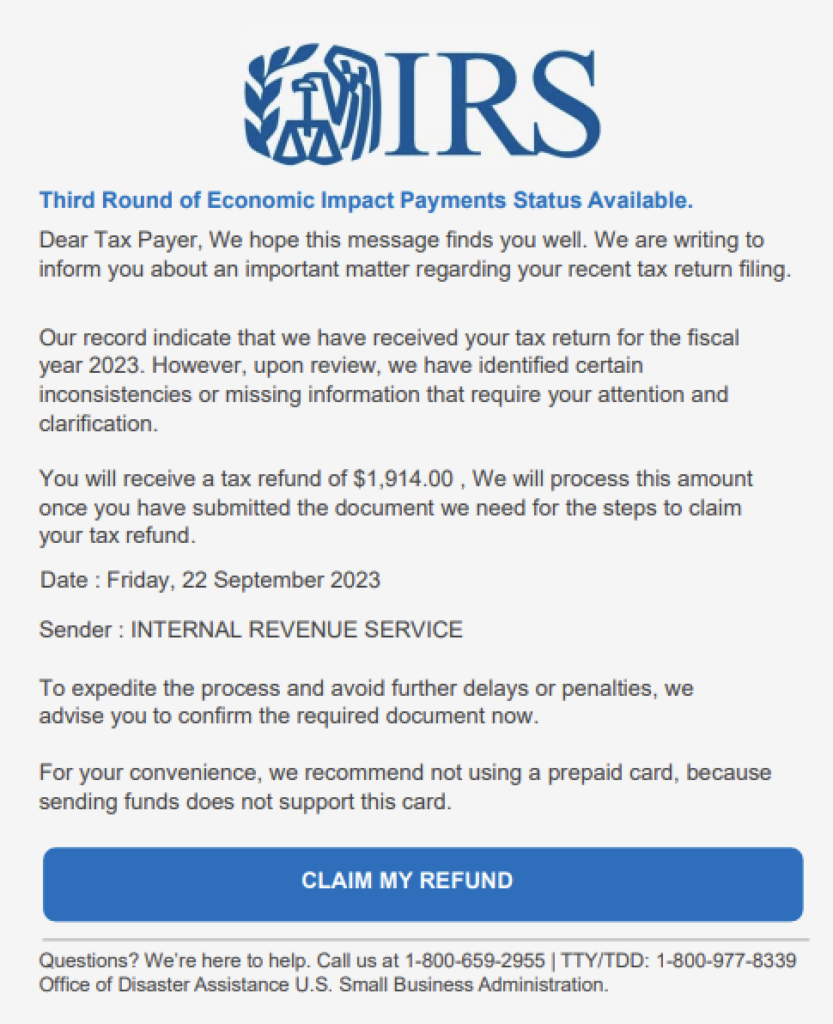
A small subset of phishing PDF attachments we analyzed purport to be from Apple and used similar social engineering tactics and the same redirector domains and URL shorteners. Another phishing campaign uses an IRS-themed scam, claiming that the recipient has a tax refund that can be collected when they click the link. These campaigns also used social media redirectors, like Linkedin Smart Links and Twitter, as well as free ecommerce marketing email services to evade detection. Let’s dig a bit deeper into how attackers used these redirectors:
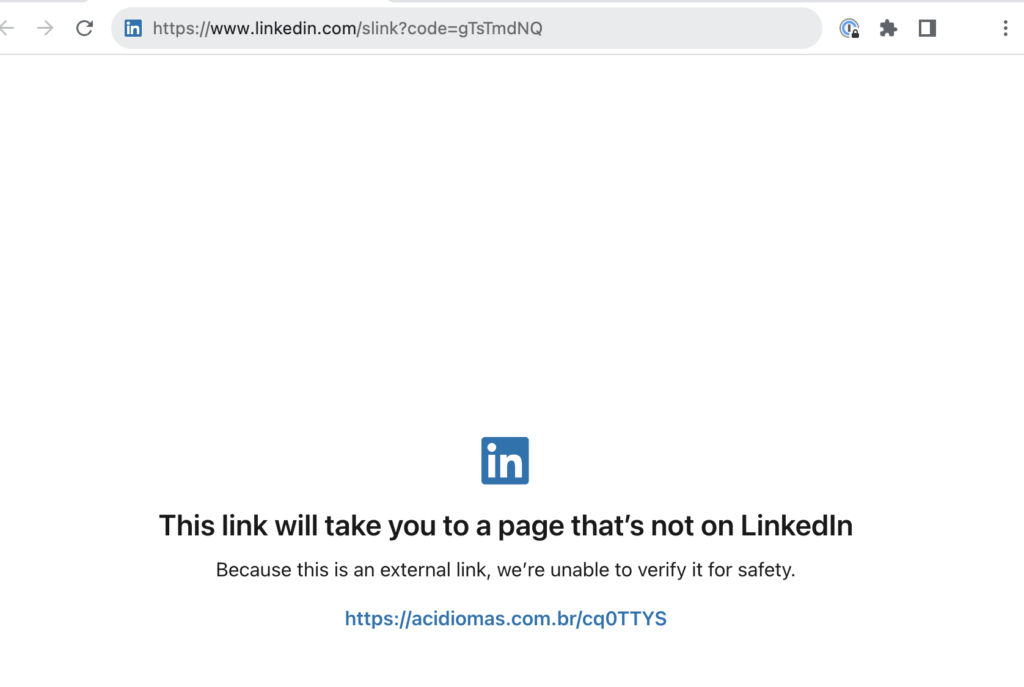
LinkedIn Smart Links and Twitter used as redirectors
The attackers on these phishing campaigns are abusing social media platforms LinkedIn and Twitter as redirectors to the phishing websites. Attackers abuse LinkedIn Smart Links, which is a feature to package and share files and websites to prospects and customers. However they were abused to redirect targets to phishing websites. Using both LinkedIn Smart Links and Twitter as redirectors can help bypass email scanners and can also provide insights about the users who click on the malicious links, which might be useful to them in their future phishing campaigns.
QR Code Generator Used As a URL Shortener
Another redirector service these phishing campaigns use is QR Code Generator PRO. This is a free online tool that allows users to generate QR codes to open different resources. For these campaigns, attackers only abuse the URL shortening feature, not the QR code itself. To shorten a URL using this tool, you have to create a website QR code type and input the malicious website as the resource. Once the QR code is created, instead of sharing the code, you can instead share the generated shortened URL.

Abusing free ecommerce marketing email services
These phishing campaigns abused e-commerce platforms’ click tracking domains to serve the redirectors that lead to the phishing sites. From the samples collected by Netskope Threat Labs, Klavio and Privy were the most commonly abused platforms. Both platforms provide free trial usage, which makes it lucrative to attackers, who often take advantage of free services. We suspect that attackers also leverage the visibility these platforms provide, using the insights to improve targeting.
Conclusions
These PDF phishing campaigns are targeting personal Microsoft Live Outlook accounts and are using the common social engineering technique of creating an urgent call to action. They abuse legitimate redirector domains and URL shorteners like Twitter, LinkedIn, and QR Code Generator PRO to evade detection. Phishing attacks like this can be avoided by never entering sensitive information (like passwords or banking details) after clicking on a link. Instead, you should always browse directly to the sites in question. For example, if you believe there is a billing issue with your Amazon account, login directly to amazon.com to verify. Netskope Threat Labs will continue to track and respond to this set of phishing campaigns.
Recommendations
Netskope Threat Labs recommends that organizations review their security policies to ensure that they are adequately protected against these and similar phishing pages and scams:
- Inspect all HTTP and HTTPS traffic, including all web and cloud traffic, to prevent users from visiting malicious websites. Netskope customers can configure their Netskope NG-SWG with a URL filtering policy to block known phishing and scam sites, and a threat protection policy to inspect all web content to identify unknown phishing and scam sites using a combination of signatures, threat intelligence, and machine learning.
- Use Remote Browser Isolation (RBI) technology to provide additional protection when there is a need to visit websites that fall in categories that can present higher risk, like Newly Observed and Newly Registered Domains.
IOCs
All the URLs related to these campaigns can be found in our GitHub repository.




 Atrás
Atrás 





















 Lea el blog
Lea el blog