We’ve seen major shifts in the digital landscape that have far reaching implications on organizations around the world. These include the widespread adoption of hybrid work, the accelerated migration from on-premise to cloud resources, and the exponential increase of data in the cloud.
While organizations gain many benefits from leveraging new cloud technologies, there are several challenges that arise with new ways of doing business, including the increasing complexity of an ever-expanding attack surface, the rising number of attacks targeting web and cloud apps, and protecting users, devices, and data regardless of where they reside. With hybrid work, employees and their devices have moved outside the traditional corporate network. Despite this shift, employees still need to do their jobs by securely using cloud and web apps their employers do not own, and the corporate data residing in the cloud must be protected. Organizations need visibility and control from endpoint to cloud services.
The Netskope and CrowdStrike Joint Solution
The Netskope and CrowdStrike joint solution plays a critical role in enabling a cloud-first architecture of “remote” endpoints that directly access cloud resources. Netskope helps organizations stay ahead of cloud, data, and network security challenges by protecting people and data anywhere they go, regardless of how they access the internet. Netskope prevents critical data from leaving corporate control while protecting against cloud-launched threats targeting cloud services and connections. CrowdStrike provides robust endpoint protection with next generation antivirus, endpoint detection and response, and threat intelligence.
The Netskope and CrowdStrike joint solution is made possible by the Netskope Cloud Exchange platform. Cloud Exchange offers a suite of integration modules to enable cloud-based data and intelligence sharing across multiple security and IT functions so teams, processes, and systems can act faster, more efficiently, and more effectively to identify, respond to, and prevent threats.
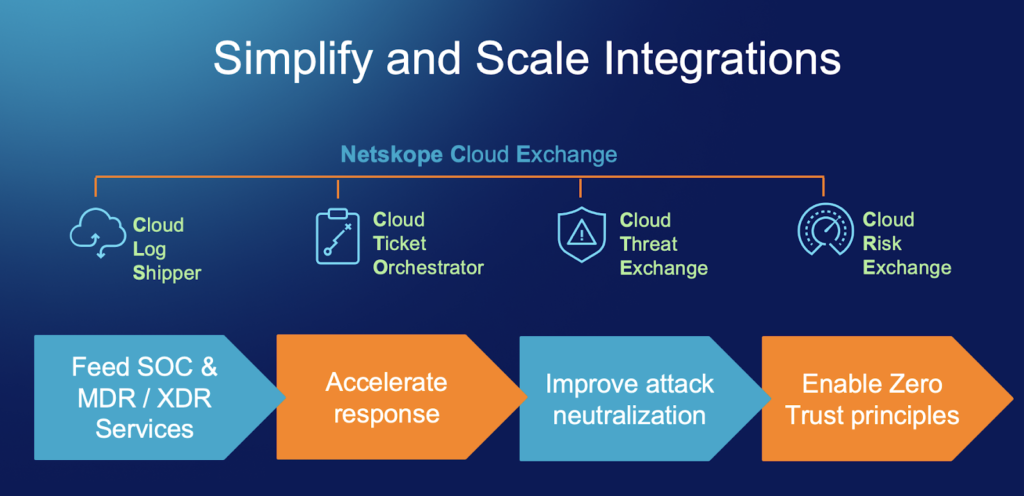
Cloud Exchange extracts valuable Netskope threat and risk telemetry, as well as external threat intelligence and risk scores, which enable improved policy implementation, creation, and exportation of log events from the Netskope Security Cloud. Cloud Exchange gives customers the ability to improve their security posture and maximize the value of their existing investments by easily and seamlessly integrating components across their security stack, including Endpoint/EDR (like CrowdStrike Falcon), email, SIEM/XDR/UEBA (like CrowdStrike XDR), cloud storage, data lakes, IT service management, threat intelligence services, and other reachable services.
Let’s deep dive into how Netskope Cloud Exchange works with the CrowdStrike solution by examining two use cases and how they positively impact joint customers.
Use Cases
Holistic Visibility and Control for XDR
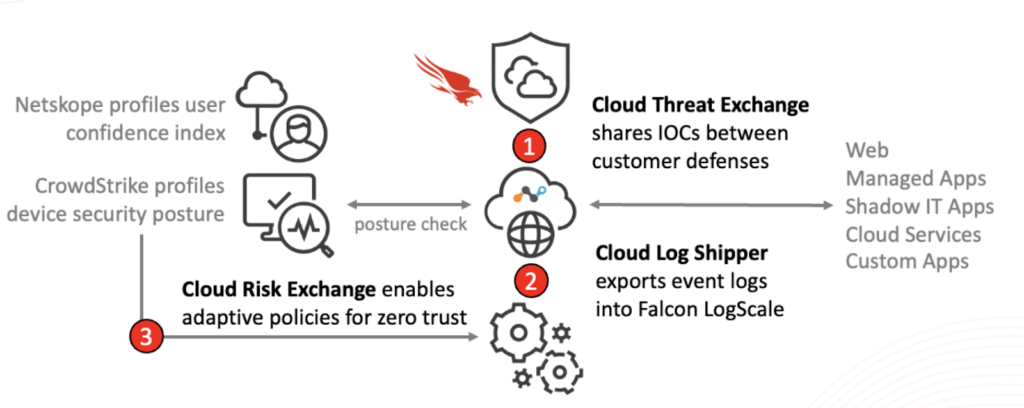
Security teams deal with too many disparate tools and data points when trying to correlate a cyber-attack kill chain across multiple threat vectors. Their aim is to gain insight into how an attack was initiated, what next steps were taken, what was compromised, etc., across many different discrete pieces of data. Netskope Cloud Exchange enables real-time sharing of indicators of compromise between Netskope and CrowdStrike Falcon to immediately ensure that what one platform knows about highly targeted attacks, both platforms know and can act on, minimizing dwell time. The Netskope Cloud Exchange integration with CrowdStrike gives joint customers the additional cloud intelligence to know exactly what took place from the cloud point of view and what needs to be done to prevent it from happening again. The benefits to organizations include:
- Gaining a holistic view of threats across endpoint and cloud
- Automating the sharing of actionable threat information
- Improving response times
- Sharing up-to-the-minute, customer-specific intelligence feeds across endpoint and cloud
Improved Protection for Your Hybrid Workforce
In hybrid work environments, remote employees need to perform their work off-site while organizations need to protect their data, which is also typically off-site. Employees may access the internet using a wide variety of devices in different ways. What constitutes safe cloud use in one situation (comprising a combination of variables), is not safe in other situations. For example, a low-risk employee using a company-issued laptop to download sensitive documents from the corporate shared drive (low-risk, acceptable) versus a risky employee using a personal device to download sensitive docs from the corporate shared drive (high-risk, unacceptable in most situations).
The Netskope and CrowdStrike joint solution increases protection for the hybrid workforce by enforcing granular policies based on rich context such as device classification, user confidence information and host risk. It combines risk information from both Netskope and CrowdStrike and makes continuous adjustments in near-real-time. Our approach to risk is based on two layers of enforcement:
- Predefined policy: This is the “usual” policy that establishes a baseline or a starting point of normal, acceptable cloud resource use. For example, different policies are enforced for users on company-issued devices versus risky or non-protected devices.
- Zero trust continuous compliance: We take it another step further by dynamically adjusting which policies apply based on continuously measured user and host risk that override the standard or predefined policy. How do we do that? For example, CrowdStrike knows when there’s malware on a device and Netskope knows when a user is risky, so we adjust the user and host profile to match a more restrictive policy. When risk is reduced on one or both elements, the user matches against a different set of policies that opens up activities and data. For example, an employee who can upload and download documents between the corporate Google Drive and her laptop during normal business loses her ability to make such uploads or downloads after getting malware on her laptop. However, she is still able to send emails, read documents and perform other such activities. As she regains the use of a safe host, she regains full rights.
The diagram below shows how Cloud Exchange facilitates these two use cases between Netskope and CrowdStrike:
In summary, the joint Netskope and CrowdStrike solution helps organizations in many ways, including:
- Empowering employees to perform their jobs from any location or device
- Reducing the cost and complexity of managing multiple point solutions
- Enforcing security without sacrificing productivity
- Streamlining threat response and enhancing overall protections
To learn more, join us at the Netskope session on September 20 at Fal.Con 2022. We look forward to seeing you in Las Vegas!




 Voltar
Voltar 
















 Leia o Blog
Leia o Blog