Summary
CrossLock is a ransomware group that emerged in April 2023, targeting a large digital certifier company in Brazil. This ransomware was written in Go, which has also been adopted by other ransomware groups, including Hive, due to the cross-platform capabilities offered by the language. CrossLock operates in the double-extortion scheme, by threatening to leak stolen data on a website hosted on the deep web if the ransom isn’t paid by the victim.
In this blog post, we will show how the CrossLock ransomware works.
Analysis
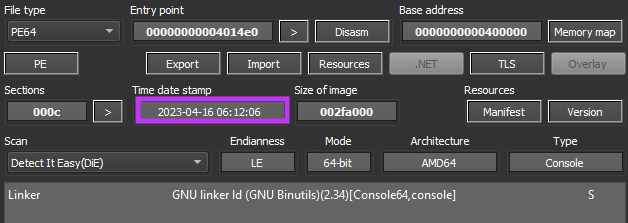
The CrossLock ransomware was developed in the Go programming language, and was likely compiled on April 16, 2023, which is the same day where the attackers added the Brazilian digital certifier in their deep web site.
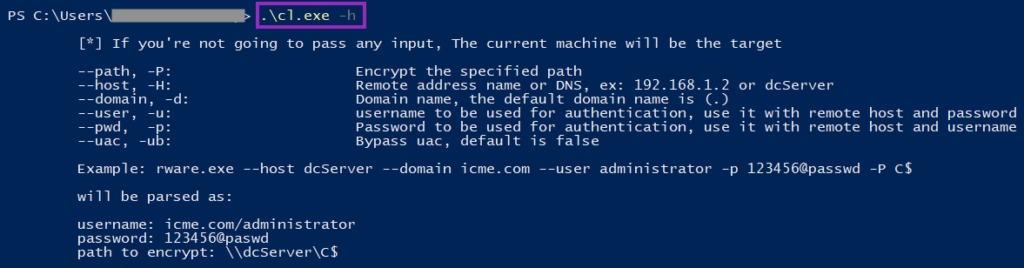
Attackers can use CrossLock to infect not only a local system, but also a remote system by using their custom parameters, which are described below:
| Parameter | Description |
|---|---|
| --path, -P | Encrypt the specified path |
| --host, -H | Remote system to run CrossLock (which can be a DNS or an IP address) |
| --domain, -d | The domain name (default is “.”) |
| --user, -u | Username used to authenticate in the remote system |
| --pwd, -p | Password of the user specified in “-u” or “--user” |
| --uac, -ub | If specified, tries to bypass Windows UAC to run with elevated privileges |
Like other ransomware families, such as BlackCat, CrossLock offers a “help” menu to provide instructions on how to use these parameters. They even included an example on how to execute CrossLock on a remote system and encrypt the entire file directory.
When executed, CrossLock outputs what it’s doing to a console. Also, the attacker left a few debug logs enabled, so it’s possible to get more insights of what it’s doing by just looking at the output.
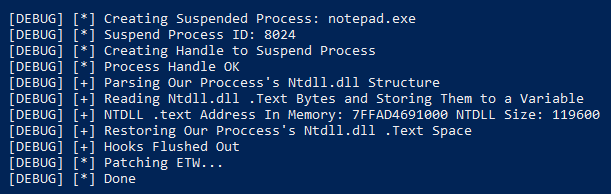
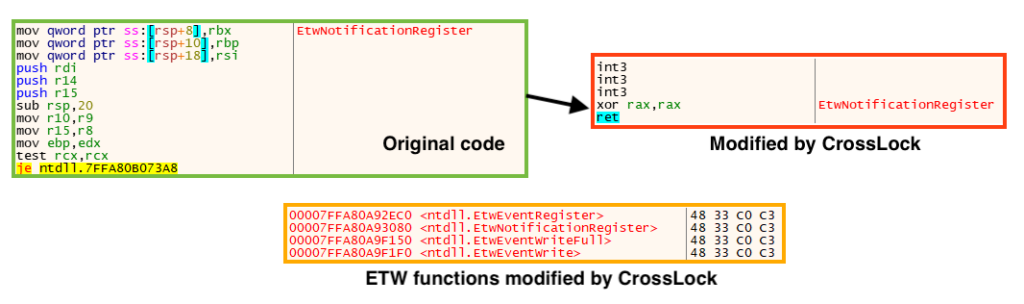
To avoid detection, CrossLock bypasses the Event Tracing for Windows (ETW), which is a mechanism that provides system and application logs that can be used by developers for debugging. This is done through a common API hooking technique, by patching functions EtwEventRegister, EtwNotificationRegister, EtwEventWriteFull, and EtwEventWrite on “ntdll.dll”.
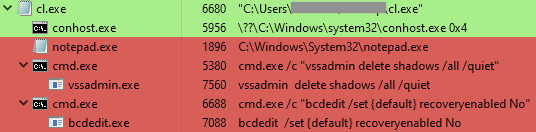
CrossLock has a hardcoded list of services and processes that it tries to stop before encrypting files, which is a common practice among ransomware families. First, it tries to stop services related to backup services, databases, and security software. Then, it tries to stop a series of processes. The complete list of services and processes it tries to stop can be found in our GitHub repository.
CrossLock also runs additional commands to delete Windows Shadow Copies using vssadmin, and to disable boot recovery using bcdedit.
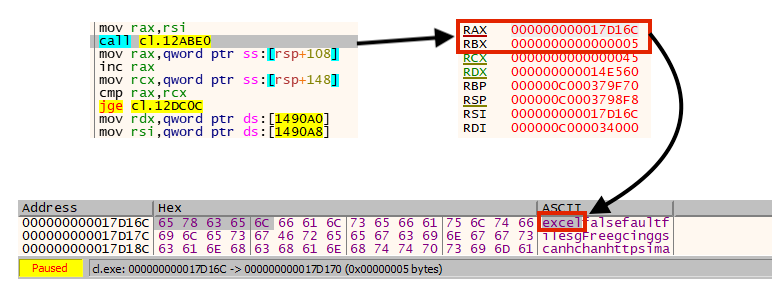
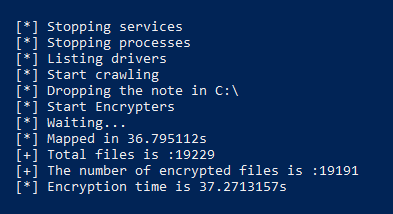
If no path was specified via “–path” or “-P” parameters, CrossLock starts crawling and encrypting files.
Like other ransomware families, CrossLock does not encrypt files that contain specific extensions or that are under specific folders, such as Windows, Program Files, and ProgramData. This is a common practice that avoids encrypting files that can corrupt the system. The list of extensions CrossLock ignores can be found in our GitHub repository.
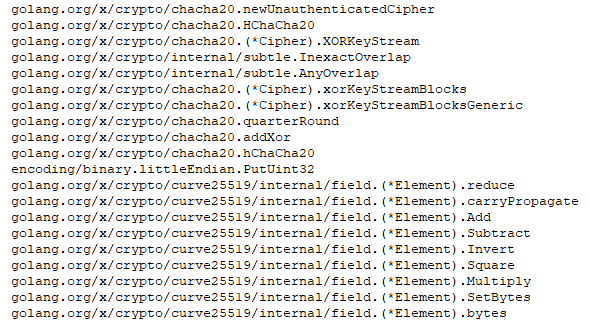
To encrypt files, CrossLock combines Curve25519 and ChaCha20 algorithms, which are implemented through Go packages.
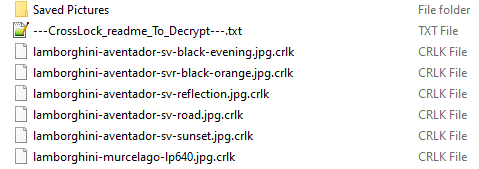
CrossLock adds the extension “.crlk” to encrypted files.
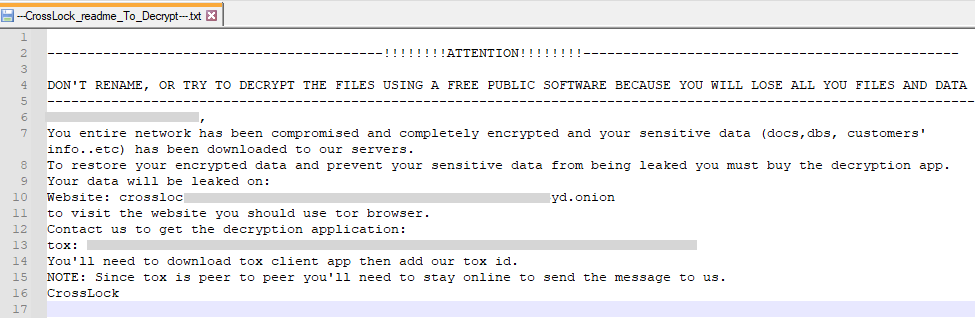
The ransom note contains the name of the company that was targeted and instructions to contact the attackers via tox chat to negotiate the ransom value.
Conclusion
CrossLock is a ransomware group that emerged in April 2023, having its encryptor developed in the cross-platform language Go. So far CrossLock ransomware has added only one target in its list, and there is only a Windows variant of its encryptor. Since CrossLock was developed in Go, it is possible that samples targeting other OSes may emerge.
Protection
Netskope Threat Labs is actively monitoring this campaign and has ensured coverage for all known threat indicators and payloads.
- Netskope Threat Protection
- Win64.Ransomware.BlackLockbit
- Netskope Advanced Threat Protection provides proactive coverage against this threat.
- Gen.Malware.Detect.By.StHeur indicates a sample that was detected using static analysis
- Gen.Malware.Detect.By.Sandbox indicates a sample that was detected by our cloud sandbox
IOCs
All the IOCs related to this campaign, and a Yara rule can be found in our GitHub repository.




 Voltar
Voltar 





















 Leia o Blog
Leia o Blog