Another day, another cyber espionage campaign exploiting two legitimate and well-known cloud services to deliver the malicious payload.
Once again, this campaign was unearthed by researchers at Sentinel One, and it is aimed to distribute the Remcos Remote Access Tool (yet another example of a remote control tool used for malicious purposes) through the DBatLoader to target predominantly organizations in Eastern Europe.
DbatLoader, is a malware downloader characterized by the abuse of cloud services to host the second stage payload that contains and executes the actual malware payload (in this specific case the Remcos RAT).
The attack starts with phishing emails distributing DBatLoader in the form of attached tar.lz archives disguised as financial documents, such as invoices or tender documentation, originating from institutions or business organizations related to the target. The phishing emails are sent from compromised private email accounts and accounts from public email services relevant to the targets.
Once the attachment is decompressed and the embedded executable is run, DBatLoader downloads and executes an obfuscated second-stage payload from two public well-known cloud services: Microsoft OneDrive (the most abused cloud service to deliver malware) and Google Drive. The executed payload abuses the mock folders technique to bypass the Windows User Account Control and drop the Remcos RAT.
How Netskope mitigates the risk of legitimate cloud services exploited to deliver malware
Microsoft OneDrive and Google Drive are among the thousands of services where the Netskope Next Gen SWG can provide granular access control, threat protection, and DLP capabilities, and the hundreds of services for which instance detection is available.
In case a legitimate cloud service is exploited to deliver malware, it is possible to configure a policy that prevents potentially dangerous activities (such as download) from non-corporate instances, or in general from any unneeded cloud storage service for the enterprise.
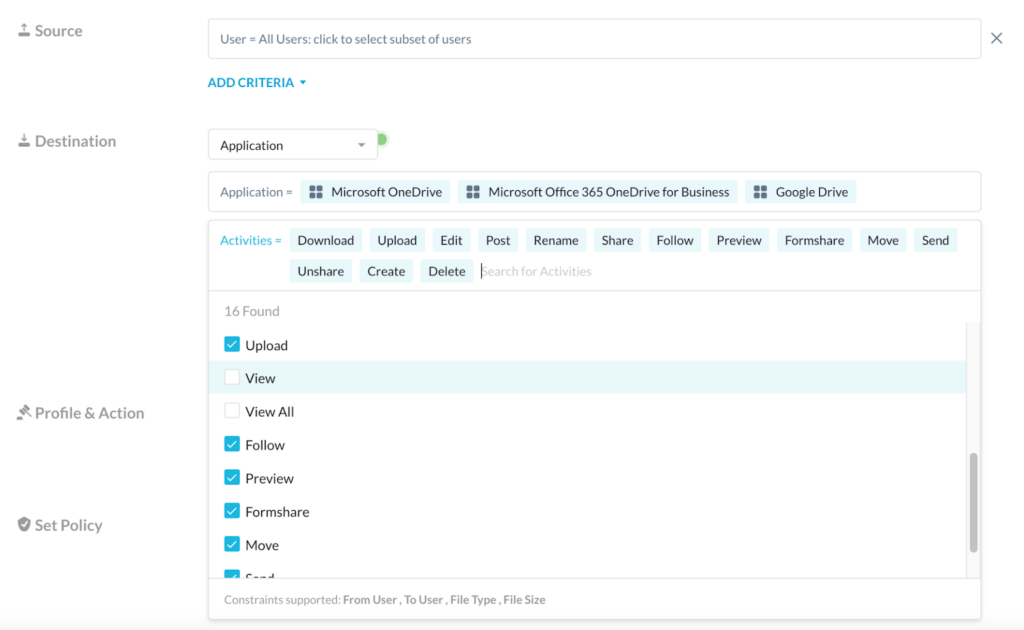
The following picture shows the example of a policy blocking any activity, except “View” and “View All” for Microsoft OneDrive, Microsoft OneDrive for Business, and Google Drive. The unmatched granular access control across the apps (a total of 16 activities can be governed in total), can also be applied to specific instances.
Netskope customers are also protected against malware downloads from a legitimate cloud service and the web in general by Netskope Threat Protection. Netskope Threat Protection scans web and cloud traffic to detect known and unknown threats with a comprehensive set of engines, including signature-based AV, machine learning-based detectors for executables and Office documents, and sandboxing, including patient zero protection.
Netskope Cloud Exchange provides powerful integration tools to leverage investments across their security posture through integration with third-party tools, such as threat intelligence feeds and endpoint detection technologies.
Finally, Netskope Advanced Analytics provides specific dashboards to assess the risk of rogue cloud instances being exploited to deliver malware or becoming the target of anomalous communications, with rich details and insights, supporting security teams in the analysis and mitigation/remediation process.
You can subscribe to the Cloud Threats Memo mailing list at this link.
Stay safe!




 Voltar
Voltar 















 Leia o Blog
Leia o Blog