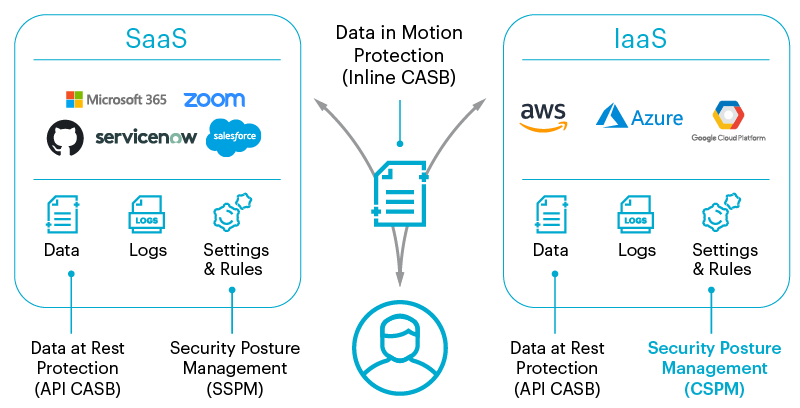
Now that we understand what security posture is, Cloud Security Posture Management (CSPM) refers to a suite of security tools and practices meant to identify and correct misconfiguration issues between organizations and the cloud. More specifically, services like Amazon Web Services (AWS), Microsoft Azure, Google Cloud, and other Cloud Service Provider (CSP) Infrastructure-as-a-Service (IaaS) cloud environments.
This is different from SaaS Security Posture Management (SSPM) which deals with the configurations of SaaS applications, rather than the infrastructure and platform services that CSPM covers.

Why do you need CSPM?
The use of cloud services is on the rise as more businesses move their businesses away from on-premise data storage and web hosting in favor of cloud-based infrastructure. The security risks associated with misconfiguration are numerous. In fact, 48% of misconfigurations in the cloud lead to the exposure of sensitive data. This puts your data, your users, your devices, and your systems all at risk of intentional and unintentional breaches.
Even if you configure your cloud infrastructure correctly, over time they can drift away (either intentionally or unintentionally) from their original setups. This is known as “misconfiguration drift” which happens when users reconfigure permissions or other settings in order to make exceptions for specific work needs, such as moving data from one place to another. The problem is that these changes leave other assets exposed, even if unintentionally. Eventually, these changes add up, leading to an unsecure cloud posture that leaves assets and systems open to those who would otherwise not have access to them.
Blog: Addressing Configuration Errors with CSPM and SSPM




 Back
Back