I’m not big on acronyms or buzzwords. Like many executives, my eyes glaze over when I’m being prospected with an alphabet soup of technology terms I supposedly “need” to care about.
So why, then, does the title of this article include Security Service Edge (SSE), Secure Access Service Edge (SASE), and Zero Trust? Despite our justified disdain for acronyms, the ideas behind these terms hold genuine importance for business leaders. In the rush (by technology vendors and analysts) to over-market these terms, we are confusing the message and obscuring their business value.
Simply put: if I’m a business leader, particularly a non-technical business leader, why on earth do I care what SSE, SASE, and Zero Trust mean?
I’ll tell you. As enterprises, we built our IT environments around two tenets: 1.) people working in offices, and 2.) applications and data living in data centers. Neither of those continues to be true, and the pandemic has been a catalyst for even faster evolution. Changing how we secure people working productively from anywhere is a journey security leaders have already started, and there’s much work still to be done.
But this journey is worth it. It will improve agility in how you go to market. It will secure your most important assets, people and data, everywhere they are. It will also mean breaking down organizational silos to help your people work more closely together, cross-functionally, than they ever have before. It means making cybersecurity a responsibility for everyone involved.
This journey will also help organizations save money. Traditional security investments are typically funded by cost avoidance, in the form of reputational and monetary costs of a breach or a ransomware attack. Unlike the incremental funding of these traditional security investments, organizations can succeed in their SSE journey by using the savings from consolidating point solutions and existing security products, reducing network and connectivity costs, and simplifying operations by consolidating teams and redeploying resources and people towards other needs within the organizations.
SSE, SASE, and Zero Trust are confusing terms, but when understood correctly, the ideas in them are an elegant way of explaining this journey, which is now completely necessary for every company in the world.
Where we’ve arrived and where we’re headed
SASE is an architecture—a design for converging formerly separate security and networking functions in a way that maximizes the value and utility of the cloud. SSE is the set of security services that securely enable that SASE architecture. Zero Trust is a set of principles that help guide our journey and for implementing SSE within a SASE architecture. But before we get into these ideas, first, let’s look at what’s brought us to the present state of technology and the need for evolving how we deliver security.
People are working from anywhere on any device. This trend was further accelerated by the global pandemic when every company shifted to remote work or a hybrid workforce. Pre-pandemic, our environments weren’t keeping up with this shift. Post-pandemic, however, they’re even further behind and need to change even faster to catch up.
We have more of a digitally-native workforce every day. Want to know what the Number One language people learning in the world is right now, spoken or coded? Python. We can’t tell our digital natives they can’t solve problems using technology. Googling answers to problems is hard-wired into their brains at this point, and they develop solutions to problems using what they find in those searches. Sometimes those solutions are SaaS applications. If our employees grab a free SaaS application to successfully keep themselves productive, we often call that shadow IT. But as the CIO of a Tier 1 auto-supplier recently told me, recalling something their own CEO said, that’s not “shadow IT” … it’s business IT. It’s using the technology available to solve a perceived business problem, so we need to find a way to support it instead of trying to stop it.
Company data is everywhere. To paraphrase something my friend Joan Holman, CIO of the global law firm Clark Hill, told me, all of our jewels used to be in our data center. Think of it like a castle, surrounded by a moat. But then, with the arrival of cloud and widespread working from home brought on by the COVID-19 pandemic, the moat dried up and everyone left the castle with all of the jewels, and we have no idea where they went. As one of my colleagues, Steve Riley, describes it, we are moving from a state of a data center to multiple centers of data.
Threats are getting more sophisticated. You’ve heard of “omnichannel” in retail; now we have omnichannel in cybersecurity threats, from phishing attacks embedded in very realistic-looking text messages to active exploitation of misconfiguration errors and poor cloud posture management. So much of it goes back to how we protect data when it’s flowing everywhere, throughout the cloud, sometimes unchecked. To use just one well-known recent example, data is moving into public cloud cloud-based applications, and the log4j vulnerability is getting exposed in a lot of public cloud-based applications, meaning a lot of data is potentially at risk.
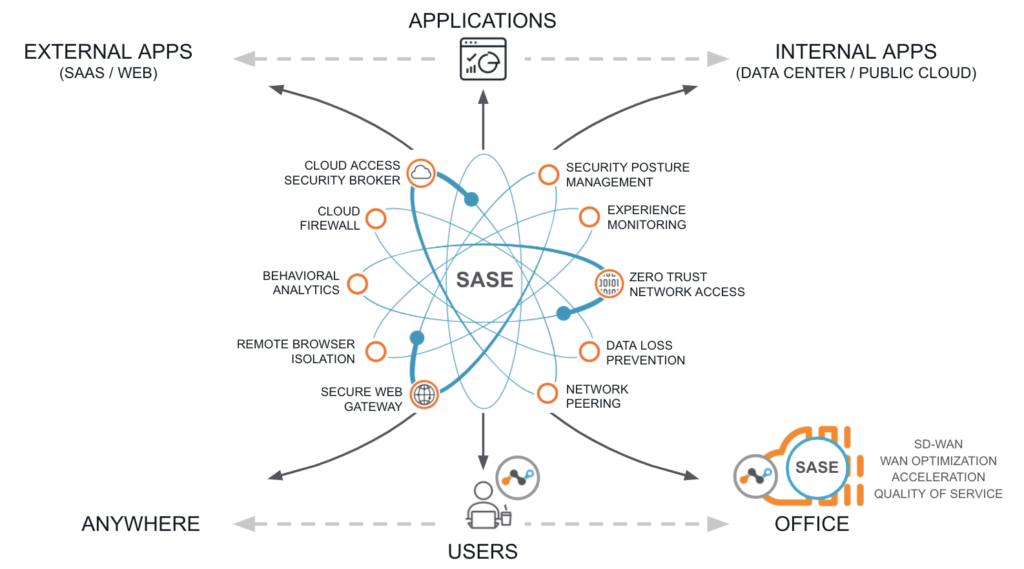
The diagram above is how we conceptualize SASE at Netskope. It has a lot of words on it, but everything in this diagram solves a particular problem and has direct implications for how you translate your spend on security technology into how effectively you can manage risk, make your business more agile, and make your business more productive. The key to what we call Intelligent SSE and SASE, however, is that they go beyond all of these pieces individually to also describe how they elegantly fit together.
Part of that fit is Zero Trust principles, which are applied through the SASE architecture to help you achieve Continuous Adaptive Trust. This is a state in which real-time access and policy controls adapt on an ongoing basis based on a number of contextual factors, including the user’s security hygiene, the devices they’re operating, the apps and distinct instances (i.e., personal or corporate) they’re accessing, the threats that are present, and the sensitivity of the data they’re attempting to access. No longer are we trusting, but verifying, as in the old days; we’re now verifying, then trusting.
Achieving Continuous Adaptive Trust can help reduce risk and, zooming out further, a SASE architecture with SSE capabilities can help provide agility and reduce costs. To elevate this conversation beyond the level of technology, here’s how we see those business values manifest:
- Risk, in which you protect critical assets, ensure resiliency of the systems and your business, and improve the security hygiene of your users to create better digital citizens out of your people
- Agility, in which you improve the employee experience, increase your speed to market for new security capabilities, and make data-driven decisions with better information than ever before
- Cost, in which you reduce total cost of ownership, achieve better operational efficiency, and take hard dollar costs out of your P&L thanks to consolidating vendors and moving network security to the cloud, so your legacy infrastructure is only accessed when absolutely necessary
There are many use cases where the benefits of this value creation would apply both short- and long-term. I’ll unpack each of these in future articles, but for now, consider:
- M&A: How can we collaborate better and faster in a complex M&A transaction involving the combination of teams, tools, and processes? In the due diligence process, how do we assess the potential risks of an acquisition? How do we get visibility into an acquisition’s cloud environment and place better controls within it? How can we simplify access to applications and data without increasing risk, impacting user experience, waiting on hardware, while also eliminating redundant hardware and technologies? And how do we provide secure remote access without relying on hardware—which is currently feeling the heavy impact of global supply chain issues?
- Shadow IT: How can we connect more of our team to discuss the problems they’re trying to solve, then standardize on a solution with IT, vs. constantly chasing down and/or trying to control the “shadow IT” activities happening in silos? Remember: what we think of as “shadow IT” is really business IT—users aren’t using it to be shady, they’re using it to get things done. So, how can IT leaders better engage with users about the problems they need to solve, and potentially leverage existing investments, before they get emotionally attached to new applications that are ultimately redundant or lack the desired secure posture?
- Public Cloud Governance: How do we ensure other teams within our organization are developing in public cloud environments with the necessary security controls, posture, and visibility? Can we redirect our users to work in these approved public cloud environments from the beginning, so we aren’t surprised by a digital transformation project once the press release drops?
- Real-Time Coaching: If we want to coach our users to make better real-time decisions, how do we do better than quarterly or annual security awareness training and actually enforce better behavior in real-time? Can we redirect them to the right apps and processes we want them to use and ultimately make them better digital citizens? How can we use the intelligence data from an SSE platform to make awareness training more targeted?
- Data Protection: To use just one example of how to better protect data on the move in the cloud, how can we use AI and machine learning to prevent data exfiltration (including images, screenshots, and digital whiteboards), accidentally or maliciously? Also, how can we make sure we aren’t violating any data privacy laws or regulations?
Properly configured SSE and SASE directly contribute to all of the above outcomes and allow you to solve business-level problems without buying “more” or forcing your old infrastructure onto needs it was never designed for.
No matter how you approach these SSE and SASE conversations with your team, underscore the idea of a journey with long-term impact. You’re asking often-skeptical stakeholders to partner with you on that journey. You don’t get there by spewing acronyms. You do get there by highlighting the business value within each of these concepts and showing how all the pieces can fit tightly together.
Connect with me on LinkedIn and let me know how you’d explain SSE or SASE in business strategy terms.
If you’re curious about what security trends are on the horizon for 2022, especially around SSE, download a copy of the Gartner Predicts 2022 report.




 Retour
Retour 





















 Lire le blog
Lire le blog