At the convergence of digital transformation, an industry-wide focus on SASE, and the effects of the continuing COVID-19 pandemic, there are key forces that security practitioners need to be aware of and operate within. This is the first blog in a series of three detailing these forces and how security leaders and practitioners can adapt to them in a digitally transforming, SASE-enabled world. This blog covers the forces of Business Strategy and Information Technology Operations.
Force 1: Business Strategy
Changes in business strategy are driving a major shift in how you need to think about your security strategy. As part of digital transformation, a significant amount of business processes are moving from internally developed on-premise applications to SaaS-based applications running in the cloud. This business-driven movement is having a greater impact on security strategy than ever seen before.
First, ask yourself, “Is digital transformation changing the way my organization functions?” The movement of the data from internal data centers to cloud-based applications will ultimately mean a shift in your controls and processes. With many businesses becoming digital service providers, their business now covers multiple revenue channels that require managing and securing. However, as new revenue channels are created, there is a logical increase in volumes of data the organization must store, process, and secure.
Most successful business organizations have concluded that access to timely operations information results in higher-performing companies. Data analytics have become the lifeblood of the company and access to the data needs to be available from anywhere at all times. As a result, successful CISOs need to enable the business to access the data and perform their jobs without the impediment of location of the individual user or application. Each company differs, but all successful companies are maximizing their potential by using new SaaS-based applications.
Given these major shifts in business strategy are driving changes in the way we manage and think about data, we have long held onto the principle of least privilege. It’s time to re-evaluate the principle considering the changing business needs to perform analytics at a rapid pace without impediment. This is not to suggest that all data be open to the entire organization, but more that non-sensitive operational data be made available to the data scientists in the organization to allow for business operations innovation. Moving away from need-to-know, but allowing the discovery of what is useful for operational analytics.
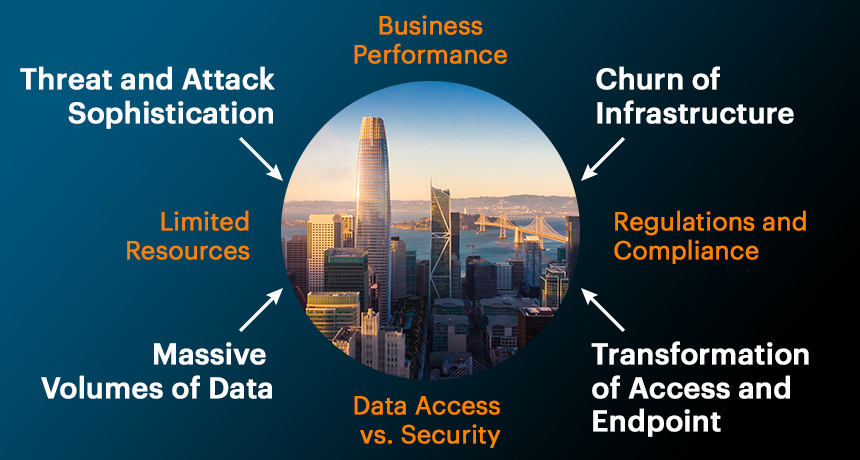
The Challenge
There are four fundamental macro issues security teams are being forced to face:
- Threats and attacks are becoming highly sophisticated and targeted toward specific organizations
- Exponential growth of data to be classified and protected
- Fundamental churn and change of infrastructure is underway due to cloud and virtualization
- Endpoints are transforming from static corporate-owned and controlled assets to personally owned and operated devices to allow for the fast and convenient access of business information.
At the same time, security teams face pressures of business performance. More than ever the information security team is a critical component of business success. Security staff resources are limited and are costly. The balancing of data access versus keeping the data secure is more difficult than ever, and the regulatory environment continues to establish strict rules on how data can be used alongside the required security controls.
Remote Workforce
As a real world example of these challenges in practice, global health concerns resulting from the COVID-19 pandemic have caused a major shift in remote working strategy. In the past, most organizations had only a small percentage of staff working from home, but that has all changed now and for the foreseeable future. This massive increase in remote workers also expands the attack surface and, because of the specific threats posed by the recent proliferation of remote staff, security leaders should assess both short-term and long-term needs.
Remote working strategy should start with the endpoint. Many workers will use corporate provided devices that are equipped with the typical endpoint security capabilities. However, many remote workers are also using personal devices to perform their daily work duties. Organizations should implement an inspection process at connection time to check that the device attaching to the network has adequate security controls.
Zero Trust Network Access (ZTNA) should be implemented with robust multi-factor authentication to ensure the user is who they claim to be before connecting to the corporate network or vital applications. Services that can enable both secure access to SaaS applications and private applications hosted in the data center or IaaS provides the advantage of enabling direct-to-internet connection rather than routing all the remote worker network traffic through the data center, to the application, back to the data center and then to the end user.
Utilization of security as a service capabilities can accelerate deployment and save the expensive cost of routing all the traffic to the data center. Instead this involves routing user traffic through inspection prior to connecting to the application by using a cloud security platform. Cloud security platforms can inspect the traffic for data leakage concerns, threats to the user or application, and filter destination sites. Better organizations are moving away from VPNs that are often not used by end-users and provide full network access when used. Next generation VPN services have the advantage of being able to inspect the destination and then, if authorized, connect users to the specific application. This provides the user with a transparent route directly to the cloud application or to the private application hosted in the data center without providing broad network access.
Security as a Business Accelerator
Like the brakes on a car, which give a driver the ability to go at higher speeds with less risk, the best security measures allow a business to move faster, not slower. Security in today’s digital reality should only introduce constraints that remove barriers to delivering data into the hands of the business decision-makers who need it most.
As data explodes, user behaviors evolve, and business models change rapidly, security can be an accelerator that allows the enterprise to fully harness data’s potential. The most successful CISOs have transitioned from a “No, you can’t,” to a “Yes we can, and here’s how” mindset. Safely allowing users access to all relevant data, all the time, empowers the enterprise to secure its most competitive asset—its data—and thus gain an edge in the race to answer the most pressing business questions.
Force 2: Information Technology Operations
Complexity is the enemy of security and we have made our security architecture too complex. Over the years we have seen a compounding effect of adding layers of security, especially at the endpoint. Unless you have done a recent cleanup you will find the endpoint has numerous client security applications, all performing similar and/or overlapping controls. It is time to take a fresh look at what is running in the environment and consolidate and simplify the architecture. Moving toward best of breed platforms that provide integrated/seamless functionality will simplify and lower operational costs.
As organizations go through this transformation they need a clear understanding of the maturity of the current IT and security operations program. Most IT teams are undertaking a major shift in their strategy moving to a “Cloud First” approach, replacing core enterprise applications with those offered as SaaS applications in the cloud. At the same time, there is also a further shift in this strategy to “Cloud Only,” in which companies are moving to completely eliminate their data centers. This is driving reinvestment in people, processes, and technologies to meet the new requirements while managing both threat and data protection. While almost every area of security is impacted, some of the key areas to review include:
- Authentication
- Network security
- Visibility
Authentication
Remote workers require a more robust authentication system. You cannot only rely on physical location or device. Multi-factor systems that are almost transparent to the end user need to find a balance between good security and ease of use. Workers today require the ability to work from multiple devices such as their laptop, tablet, phone, and even personal computers. The digital world is built around the user and modern technology gives them lots of choices. In the past, we considered the user as the weakest link, but now the user has the most power.
For a long time, we have implemented the concepts of “least-privilege” or “need-to-know,” wherein we granted users minimal access with strong protections. Similar to how we shifted our network strategy from “allow-only” to “Zero Trust networks,” we need to shift the way we approach user access. The new normal will be allowed access, “user decides,” and applying restrictions to data by exception, shifting the focus to enabling data use. If you do make the shift to lower restrictions on data access, it will require implementing more sophisticated behavior analytics to detect data misuse.
Adaptive Trust
More than 90% of new computers purchased are now mobile devices. Today’s power users demand the ability to login from anywhere, on any device, and access everything. To meet this new demand, companies need to adjust their authentication and authorization processes and technology.
One way to approach the problem is via an adaptive trust scheme. An adaptive trust scheme matches the level of confidence in the authentication to the level of risk of the asset being accessed or changed. An adaptive trust model looks at five core elements to determine if access is granted:
- Authentication level
- Access level
- Application trust
- Device trust
- Asset classification
Implementing Adaptive Trust
Using these five core elements of adaptive trust, a dynamic decision can be made in real-time as to whether access should be granted. Higher value information and access level requires more trust in the user, device, and application. Higher levels of trust are more costly and intrusive, so a better security program will find the balance between the trust level required and the action being requested. Keep in mind that Zero Trust goes beyond the user and includes the devices, applications, etc. In today’s dynamic world there is not any implicit trust anywhere in the transaction.
Network Security
Secure access service edge (SASE) is the convergence of network-as-a-service and security-as-a-service and an emerging security and network framework that guides the approach in which data and applications are deployed and consumed. SASE further evolves security infrastructure to protect an increasingly perimeterless environment. The goal of the SASE model is to shift operations from managing security appliances for both cloud and web to delivering a central, policy-based service via a cloud-native microservice platform. This is where we see the emergence of a Next Generation Secure Web Gateway (NG SWG) that is cloud-native and understands the new protocol languages of both the internet and cloud.
The shift to information-rich cloud applications has moved the majority of traffic from inside the data centers to cloud-based applications, so it no longer makes sense to backhaul all the information. Without proper controls, this eliminates the security, visibility, and threat protection of a traditional data center. Zero Trust Network Access (ZTNA) is a methodology for addressing and supporting the mobile workforce. ZTNA is not a single technology or process, but a number of principles that when brought together provide the ability to match the level of authentication and device attributes (managed versus unmanaged) with the associated level of risk. The level of risk is related to the employee, the sensitivity of the information, the type of access, and the trust level of the application.
When using a SaaS application there is a higher need to understand who is using the application and for what purpose. SaaS applications typically have a great deal of functionality and the best way to handle the changes is through a Cloud Access Security Broker (CASB) with advanced threat protection and DLP. Using a CASB provides the ability to identify and protect against malware, provide visibility into the SaaS applications being used, and control how they are being used. The approach must also include blocking or allowing types of data through data loss prevention (DLP) policies and identify the risk level of an application to protect against the use of high-risk cloud applications.
Visibility
Visibility is one of the most important controls to prevent massive security breaches. If you can detect and respond immediately when an endpoint is compromised then there is no material financial impact. If the breach takes months or years to detect there are significant financial and business operations costs, possibly in the millions.
The lack of visibility is a very real problem for many organizations. Businesses are finding solutions to their most pressing needs in new SaaS-based applications. But, it’s possible that the security organization doesn’t even know the business is using a given SaaS app, and you can’t manage the risk of something you can’t see. This is especially true when SaaS solution providers rarely give you access to application logs, traditionally used to build SIEM. Unless you have forced hairpinning of all the network traffic from the managed devices through your data center, It’s going directly to the cloud-based applications. If your users are going directly to O365, GSuite, Salesforce then you are completely blind to the transaction, unless you implement a monitoring proxy. Further exacerbating the problem is that most users have more than one machine and are accessing the applications from their personal machines, tablets, or phones. Without implementing the right technologies there is another big hole in your visibility.
Given this shift in network traffic, your strategy needs to include a forward and reverse proxy capability to enable inspection of the network traffic. This is because most cloud applications have implemented SSL encryption, which leaves traditional decryption methods blind as well. The solution must look beyond just the destination URL deep into the JSON and be able to decode the cloud traffic to be context and content aware. Your solution also needs to be inline to be able to react in real-time and answer these sorts of questions: Is the user accessing a corporate or personal instance of the application? Are they trying to read, write, or share the data? Is the data sensitive and does our corporate policy allow this transaction?
SaaS solution providers are going to need pressure from the industry to provide the logs to their customers to keep the system in check and to provide the necessary oversight to meet our risk management and regulatory demands.
Curious about the remaining forces? You can read Part 2 here and Part 3 here.
While it is true that 2020 has changed the landscape of cloud security, Netskope was purpose-built for SASE. Let us show you why during our SASE Week! Click here for more information!




 Zurück
Zurück 





















 Den Blog lesen
Den Blog lesen