Recently, a team of experts from JumpSEC Labs discovered a vulnerability in Microsoft Teams that allows malicious actors to bypass policy controls and introduce malware through external communication channels. Leaving end-users susceptible to phishing attacks.
Microsoft’s advice is to educate end-users to detect phishing attempts. One workaround would be to disable Microsoft Teams collaboration with external organizations.
This particular vulnerability in Microsoft Teams enables threat actors to bypass existing policy controls, allowing them to share links to malicious files within Teams chats, without the end-user ever accepting a message-request. This circumvention of security measures can have severe consequences for organizations, especially considering that Microsoft Teams boasts a user base of 300 million users worldwide.
To make matters worse, this attack does not rely on email, bypassing traditional email security measures and abusing the inherent trust end-users have with collaboration tools. Besides end-users, many organizations inherently trust SaaS as a reliable source as well. This translates to security controls where trusted sources are not inspected and thus bypassed.
The Netskope Threat Labs Stats for June 2023 blog revealed that 60% of all malware downloads through HTTP/HTTPS were traced back to popular cloud apps. Additionally, 32% of SaaS-delivered malware originated from OneDrive and SharePoint, indicating the need for strengthened security measures on these platforms. The notion that SaaS is considered a ”trusted source” directly contradicts the fundamental principle of zero trust.
Based on these principles, organizations should always inspect all downloads for threats, regardless of their origin. This approach allows organizations to enable external parties to share content while still leveraging Netskope Advanced Threat Protection to block malicious file transfers.
To effectively combat such threats, organizations need a comprehensive cybersecurity solution that follows the principles of zero trust and secure access service edge (SASE). Netskope implements these principles through its private cloud platform regardless of an organization’s location or the nature of their workloads (Web, SaaS, VPC, IaaS, etc.), protecting users and machines across various environments.
The power Netskope provides is the ability to identify and control the usage of specific SaaS instances within a service. This granular control empowers organizations to mitigate and manage risks effectively while enabling collaboration across multiple SaaS platforms. By implementing Netskope, organizations can protect users from interacting with unknown and unmanaged SaaS applications, including those originating from desktop clients like Microsoft Teams. Additionally, Netskope allows organizations to enforce limitations on SaaS activities, such as sharing, liking, reposting, and downloading files, especially when they involve trusted external partners.
These capabilities make it possible to protect end-users against these phishing attacks as shown in the diagram below.
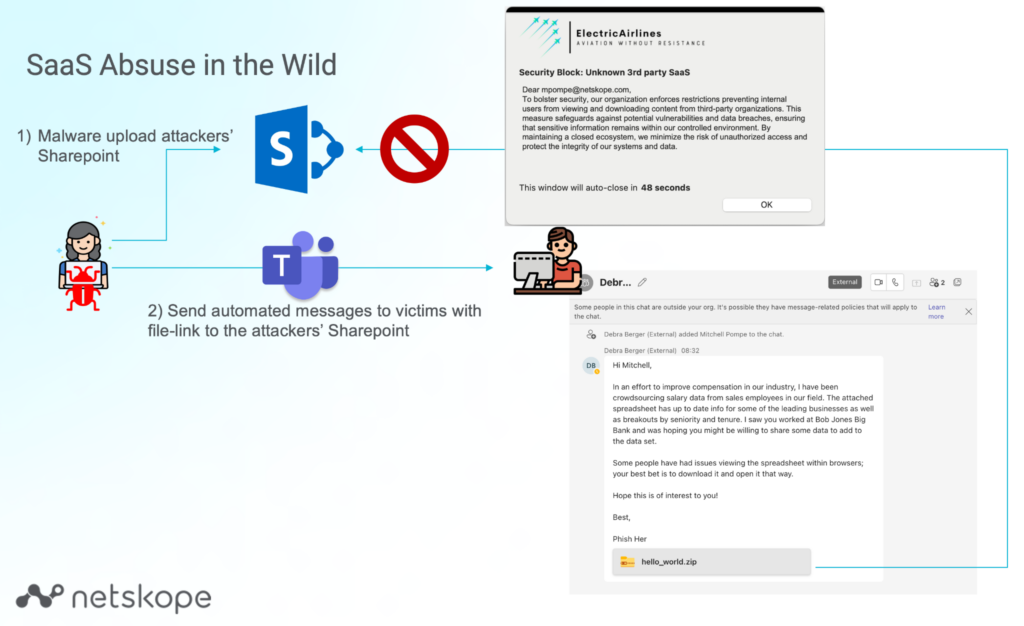
Additionally, to enable these security measures, Netskope leverages advanced threat protection techniques such as sandboxing and data protection. These features allow for the scanning of sensitive information, such as personally identifiable information (PII), source code, or medical records, to identify potential threats or policy violations. By combining these advanced measures with the robust Netskope security platform, organizations can effectively defend against emerging threats.
Netskope’s Advanced Analytics capabilities provide security teams with specific dashboards and valuable insights to assess the risk of rogue cloud instances being exploited for malware delivery or the potential of anomalous communications targeting the organization. Rich details and comprehensive analysis empower security teams to make informed decisions and streamline the mitigation and remediation processes. The Sankey diagram below showcases a visual representation of the interaction between various SaaS, the used instances, and their respective activities.
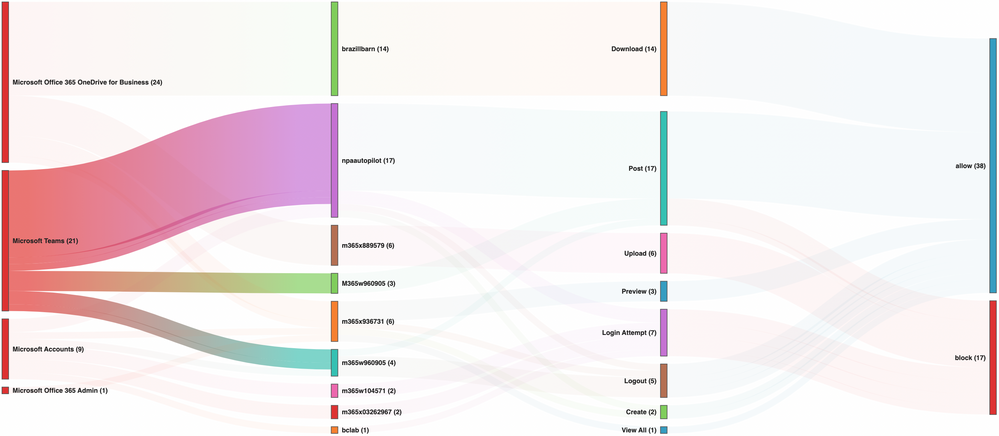
The Microsoft Teams vulnerability discussed in this blog highlights the importance of comprehensive visibility, understanding, and control of SaaS, the instances, and the activities within.
By leveraging the comprehensive security solutions offered by Netskope, organizations can effectively protect themselves from emerging threats and vulnerabilities by applying zero trust, advanced threat protection and robust data security measures.
To learn more on how Netskope can help your organization to mitigate similar risks via instance awareness, watch this demo: Defending against cloud threats with instance-awareness. Additionally, to learn more about the latest emergent cloud-native threats, and how Netskope can mitigate them, subscribe to the Cloud Threats Memos so you don’t miss a threat!




 Zurück
Zurück 





















 Den Blog lesen
Den Blog lesen