Cybercriminals are increasingly abusing popular cloud apps to deliver malware to their victims. In 2020, more than half of all the malware downloads detected and blocked by the Netskope Security Cloud platform originated from cloud apps. Cloud apps are commonly abused to deliver Trojans, with attackers attempting to exploit the trust placed in the app used for delivery. Increasingly, cloud apps are also abused for next-stage downloads, with attackers attempting to blend in with benign traffic. This blog post analyzes how attackers are abusing popular cloud apps and what you can do to defend yourself.
This blog post accompanies the release of the February 2021 Cloud and Threat Report, which analyzes 2020’s most interesting trends in enterprise cloud and web security. In addition to highlighting personal app usage, the Cloud and Threat Report also highlights four other trends:
- Cloud app use continues to rise, with a 20% increase led by collaboration and consumer apps
- Malicious Office documents increased dramatically, now representing 27% of all malware downloads.
- Personal app usage in the enterprise continues to increase, with 83% of users accessing personal apps from managed devices.
- Cloud phishing continues to increase, with 13% of phishing campaigns hosted in the cloud and 33% targeting cloud app credentials.
Cloud vs. Web: The Trend
For each malware download, we determine whether the download originated from a cloud app or from the web based on its URL. If the URL matches one of the cloud apps signatures in our CCI database, then it is a “cloud app” download. Otherwise, it is a “web” download. For example, a file downloaded from somerandomwebsite[.]com/malware.exe does not match any of the signatures in our CCI database and is labeled a “web” download. A file downloaded from drive.google[.]com/file/d/abcd1234 matches the Google Drive signature in our CCI database and is labeled a “cloud” download.
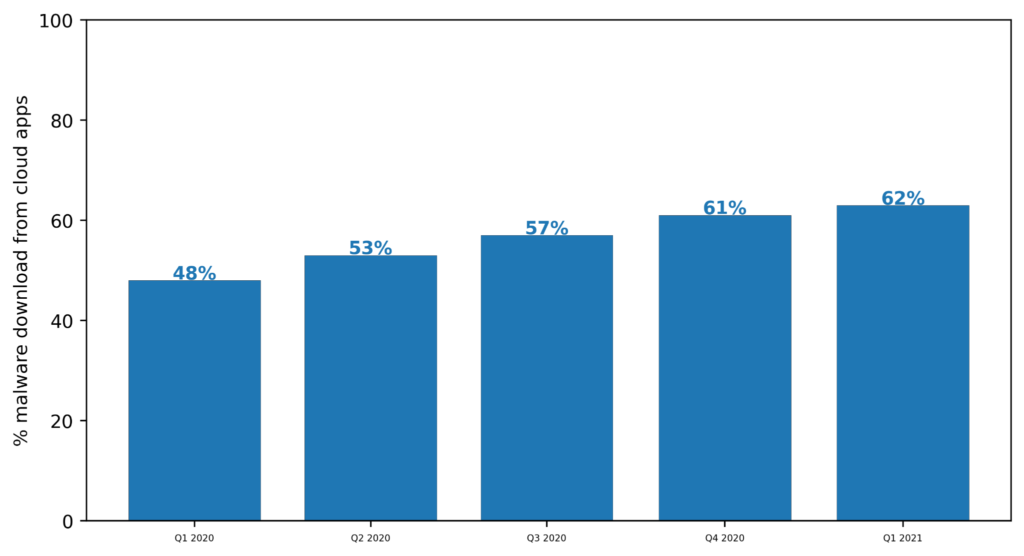
The following chart shows that the percentage of malware downloads from cloud apps has increased 14 points from 48% in Q1 2020 to 62% in Q1 2021. At the beginning of 2020, the majority of malware downloads came from the web. Starting in Q2 2020, the majority of malware downloads came from cloud apps, and that percentage continues to grow quarter-over-quarter.
Breakdown by app
Which cloud apps are the malware downloads detected on the Netskope Security Cloud platform coming from? In general, cybercriminals abuse popular apps to host malware. By selecting popular cloud apps, they aim to bypass blocklists that might block traditional malware delivery infrastructure. They also aim to exploit trust that users place in these popular apps. In other words, cybercriminals go wherever the users are. While the Netskope Security Cloud detected malware downloads from 166 distinct cloud apps in the past 18 months, the downloads were heavily concentrated in the most popular apps. The most popular webmail and cloud storage apps accounted for 70% of the total malware downloads:
- Amazon S3
- Box
- GitHub
- Google Drive
- Google Gmail
- Microsoft OneDrive
- Microsoft Outlook.com
- Sourceforge
While cloud apps are most commonly used for initial Trojan downloads, cybercriminals have also used them to host next-stage downloads. The GuLoader Trojan downloader was used by multiple threat actors in the past 18 months to download next-stage payloads from Google Drive and Microsoft OneDrive. GuLoader was the most common source of next-stage payloads in the cloud on the Netskope Security Cloud platform in 2020.
Breakdown by file type
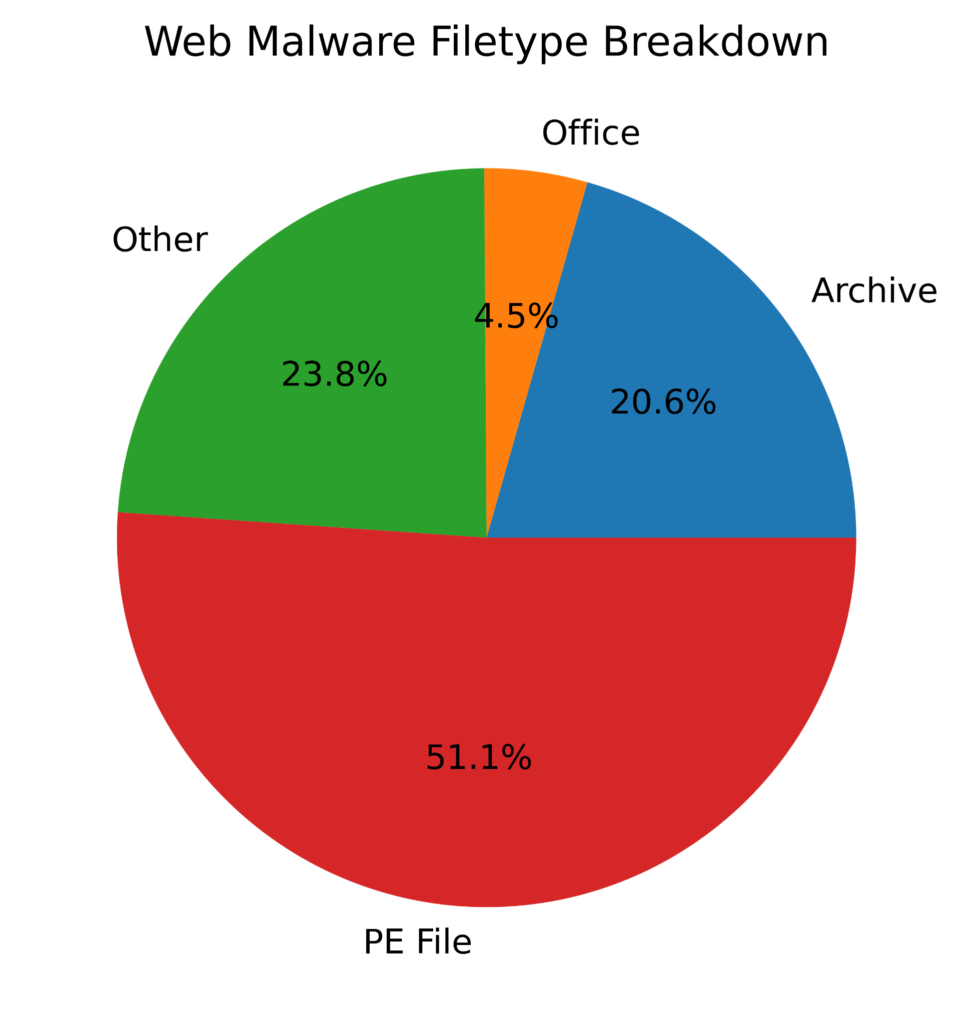
The distribution of the types of files differs between cloud apps and the web. From the web, the majority of malware downloads are of Windows Portable Executable (PE) files, like EXEs and DLLs. The other half are archive files, like Zip files, Microsoft Office file formats, and other types, like scripts and JARs.
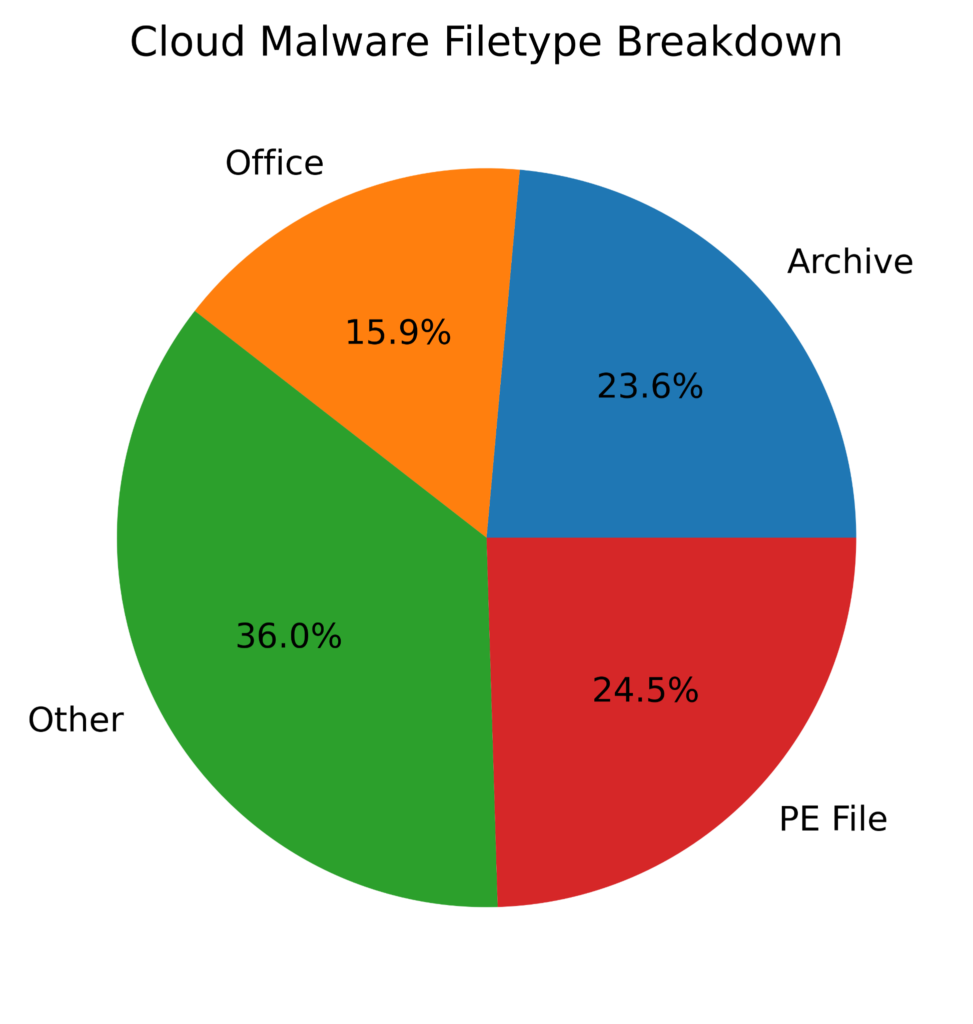
By comparison, malware files downloaded from cloud apps are more evenly distributed among these four file types, with PE files representing only one-quarter of all downloads and Office files notably representing 15.9% (compared to 4.5% for web malware downloads). In other words, the surge in malicious Office documents we observed in 2020 was driven primarily by malicious Office documents downloaded from cloud apps.
Data analysis
The analysis presented in this blog post is based on anonymized usage data collected by the Netskope Security Cloud platform relating to a subset of Netskope customers with prior authorization.
Conclusion
The rise in the popularity of cloud apps as a channel for cybercriminals to deliver malware is a result of the overall rise in popularity of cloud apps—cybercriminals go wherever their victims are. Because nearly any cloud app can be abused as a malware distribution channel, organizations should enact policies to scan all content entering their networks—from the web or from the cloud—for malware.




 Zurück
Zurück 















 Den Blog lesen
Den Blog lesen