Summary
Naming themselves Night Sky, a new ransomware family was spotted on the first day of 2022, by the MalwareHunterTeam. They appear to work in the RaaS (Ransomware-as-a-Service) model, similar to other ransomware groups like REvil, LockBit, and Hive, publishing stolen data exfiltrated throughout the attack in a deep web site if the ransom is not paid by the victim.
Currently, there are two companies listed on their deep web site, where the group has published the victim’s allegedly stolen data.
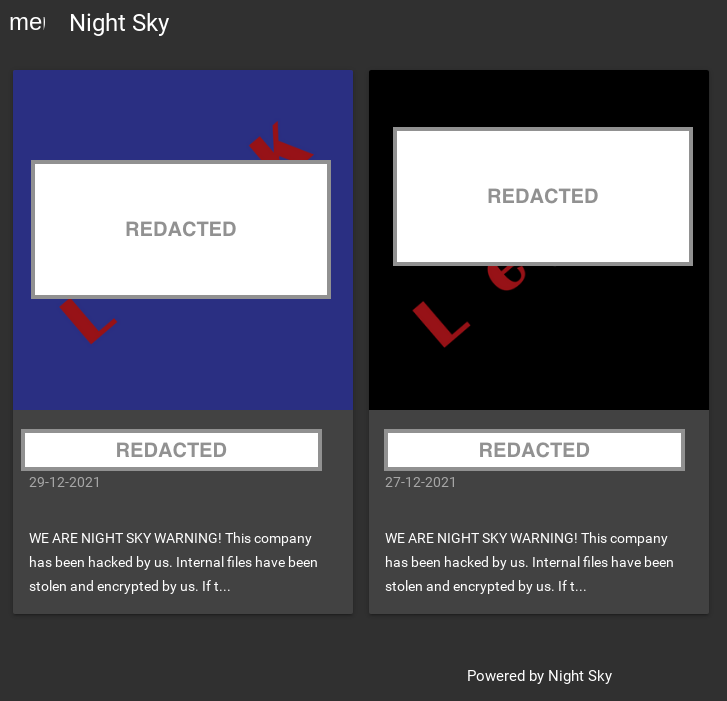
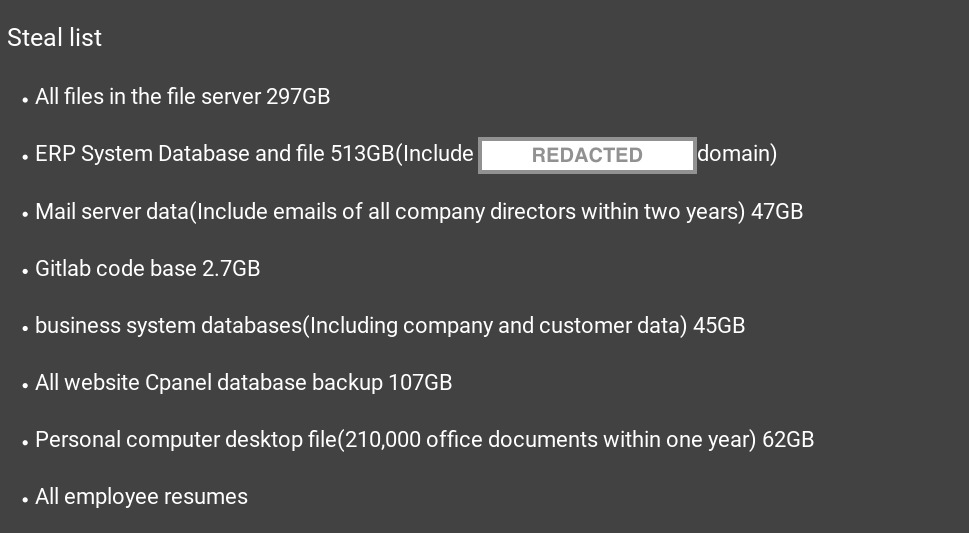
Night Sky publishes a list of everything they claim to have stolen.
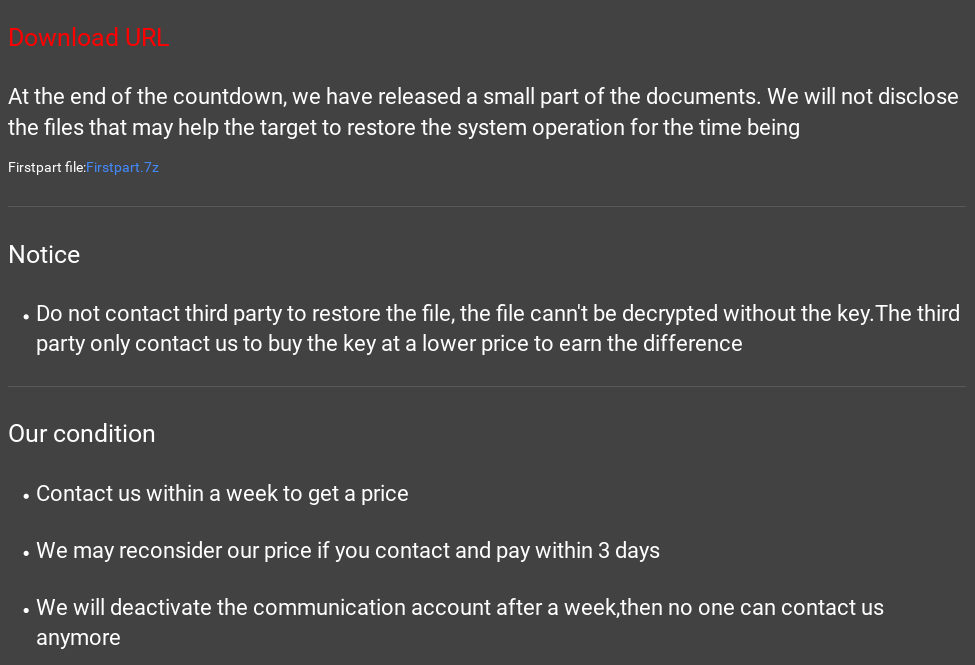
Aside from this list, there are also screenshots of the stolen files and data. The group demands the victim to contact them within a week after the attack, claiming that the contact website will be disabled after this period, eliminating the chances of recovery through payment.
Researchers have found that the Night Sky ransomware group was using the Log4Shell vulnerability (CVE-2021-44228) to successfully infect their targets as early as January 4, 2022. It’s not the first time a ransomware family has been found utilizing this vulnerability either, as Khonsari was using it in December 2021.
Furthermore, similarities between Night Sky and Rook ransomware were found by comparing their binaries, containing only a few differences in the encryption algorithm. However, at this point it’s unclear if this is the same threat group or a code reuse.
Threat
Only two samples of Night Sky were found in the wild so far, being both 64-bit executables using VMProtect software, which adds a strong protection against analysis and reverse engineering.
Before encrypting the files, Night Sky uses a hardcoded mutex to verify if another instance of the ransomware is already running.
We created a small code that creates the same mutex and we confirmed that the ransomware skips the encryption if the object already exists.
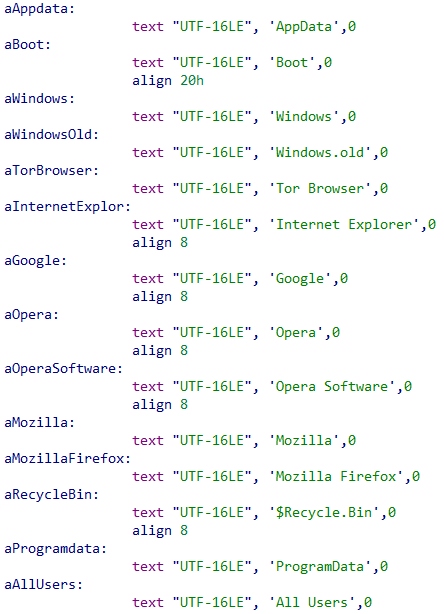
Once running, Night Sky starts listing all directories, skipping the following folders and files:
- #recycle
- $Recycle.Bin
- All Users
- AppData
- autorun.inf
- Boot
- boot.ini
- bootfont.bin
- bootmgfw.efi
- bootmgr
- bootmgr.efi
- bootsect.bak
- desktop.ini
- iconcache.db
- Internet Explorer
- Mozilla
- Mozilla Firefox
- ntldr
- ntuser.dat
- ntuser.dat.log
- ntuser.ini
- Opera
- Opera Software
- Program Files
- Program Files (x86)
- ProgramData
- thumbs.db
- Tor Browser
- Windows
- Windows.old
NightSky also skips files with the extensions “.exe”, “.dll”, and “.nightsky”.
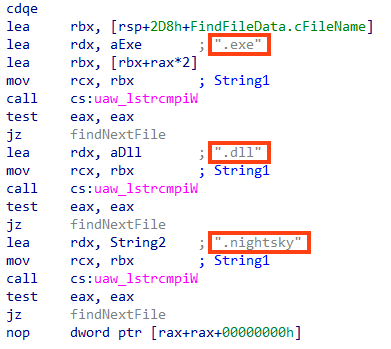
If the file doesn’t match the criteria above, Night Sky adds the “.nightsky” extension and starts the encryption routine.
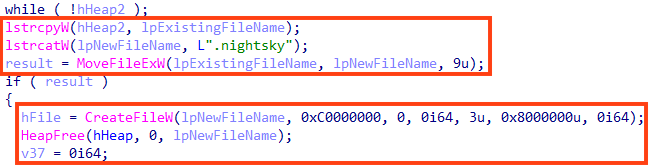
Night Sky uses the Mbed TLS library functions during the encryption.
Throughout the encryption process, Night Sky uses a combination of AES-128-CBC for file encryption, and a combination of RSA to encrypt the keys, which is appended to the file. This page contains more detailed information about Night Sky encryption processes, as well as similarities between Rook ransomware.
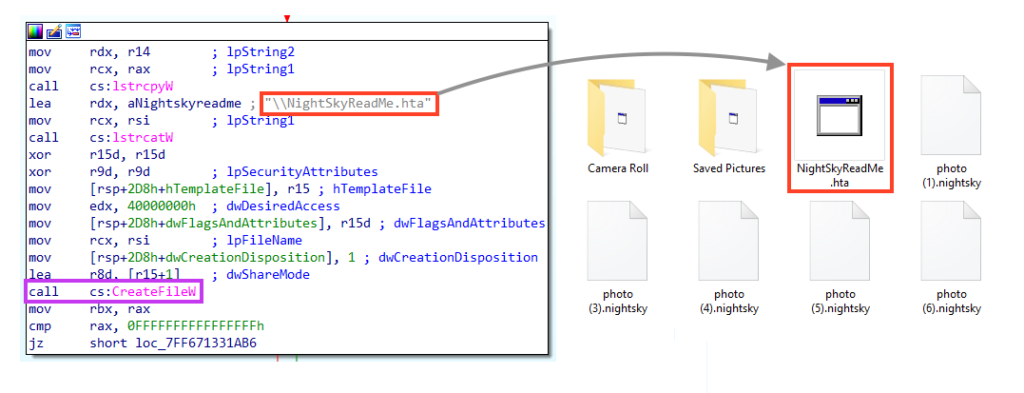
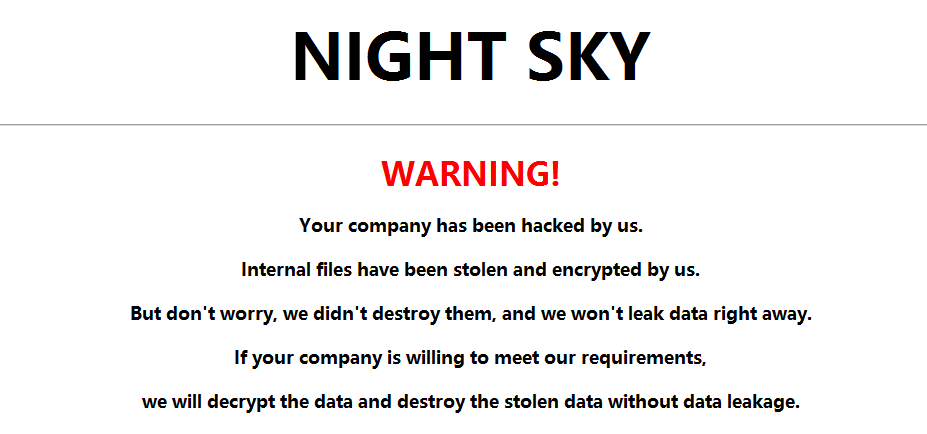
The ransomware creates the ransom note in HTA format in every single directory, named “NightSkyReadMe.hta”.
The ransom note contains some of the information that is also published on the deep web site, along with the URL and contact information.
Protection
Netskope Threat Labs is actively monitoring this campaign and has ensured coverage for all known threat indicators and payloads.
- Netskope Threat Protection
- Win64.Ransomware.NightSky
- Netskope Advanced Threat Protection provides proactive coverage against this threat.
- Gen.Malware.Detect.By.StHeur indicates a sample that was detected using static analysis
- Gen.Malware.Detect.By.Sandbox indicates a sample that was detected by our cloud sandbox
IOCs
A full list of IOCs and a Yara rule are all available in our Git repo.




 Back
Back 





















 Read the blog
Read the blog