As a follow up to yesterday’s post on the Logjam attack vulnerability, Netskope has been continuously monitoring SaaS applications to see whether they are vulnerable to this attack. We have done additional research on exactly which SaaS apps are vulnerable and have come up with some recommendations for enterprises to protect themselves.
As of today, we have identified 202 SaaS apps currently vulnerable to attack via Logjam spanning across 870 unique domains/IPs. Of note, we also found that Logjam is impacting less than half of all currently vulnerable SaaS apps in comparison to the FREAK attack (which had 473 vulnerable SaaS apps on the first day).
For existing Netskope customers, the information about vulnerable SaaS apps has been rolled into the Netskope Cloud Confidence Index™ (CCI) and can be accessed by logging into the respective Netskope tenant account. Among all SaaS apps vulnerable to a Logjam attack, we have found:
- 5 apps had a High CCI;
- 21 apps had a Medium CCI;
- The remainder had either a Low or Poor CCI. This category includes 87% of all vulnerable apps.
An important observation we made was that NONE of the Excellent CCI apps are vulnerable to Logjam attack.
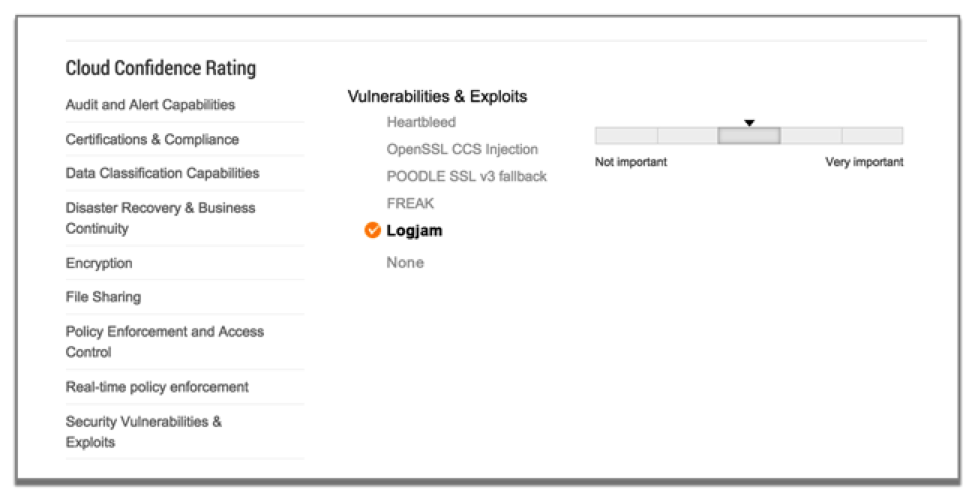
Figure from Netskope’s Cloud Confidence Index™ showing an app vulnerable to Logjam
So, what can enterprises do to protect themselves? Here are a few steps you can take:
Enterprise IT:
- Upgrade users’ browsers to their latest versions. Broswer testing can be conducted here: https://weakdh.org/. Vulnerable browsers will immediately trigger a warning.
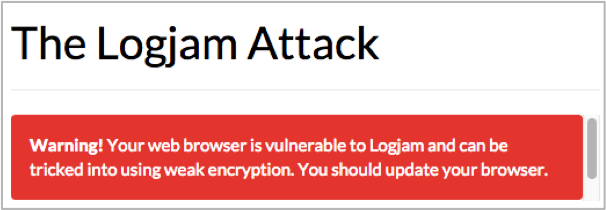
Figure from weakhd.org showing warning for browsers vulnerable to Logjam
As ComputerWorld reported on May 20 at 10:58a PT, only Microsoft’s Internet Explorer had been patched:
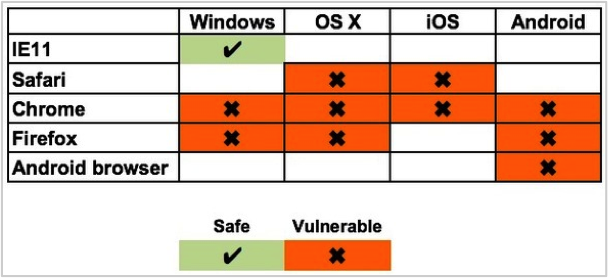
Figure from ComputerWorld shows IE11 as the only safe browser as of May 20, 10:58a PT
- If you’re a Netskope customer, create a policy that blocks uploading of data to vulnerable apps that are important to your business.
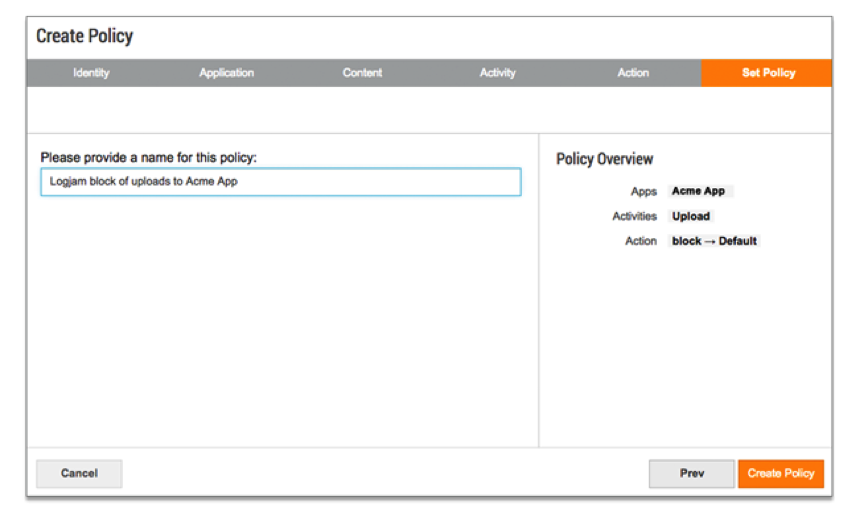
Example of Netskope policy that will block uploads to a specific app
- Enterprises without a CASB that allows for granular policy control can utilize their secure web gateway or next-gen firewall to block traffic to/from the app in its entirety.
SaaS app vendors:
- If you’re using SSL/TLS, you should disable support for export cipher suites. It is also recommended to deploy (Ephemeral) Elliptic-Curve Diffie-Hellman (ECDHE) and generate a unique 2048-bit Diffie-Hellman group. You can find more guidance and an online tool to test your web server here.
One of the popular SSL/TLS libraries, OpenSSL, published extensive details about Logjam and the upcoming changes to OpenSSL library here.




 Back
Back 




















 Read the blog
Read the blog